Awesome
<img src="https://github.com/9001/copyparty/raw/hovudstraum/docs/logo.svg" width="250" align="right"/>💾🎉 copyparty
turn almost any device into a file server with resumable uploads/downloads using any web browser
- server only needs Python (2 or 3), all dependencies optional
- 🔌 protocols: http // webdav // ftp // tftp // smb/cifs
- 📱 android app // iPhone shortcuts
👉 Get started! or visit the read-only demo server 👀 running from a basement in finland
📷 screenshots: browser // upload // unpost // thumbnails // search // fsearch // zip-DL // md-viewer
🎬 videos: upload // cli-upload // race-the-beam
readme toc
- top
- quickstart - just run copyparty-sfx.py -- that's it! 🎉
- at home - make it accessible over the internet
- on servers - you may also want these, especially on servers
- features - also see comparison to similar software
- testimonials - small collection of user feedback
- quickstart - just run copyparty-sfx.py -- that's it! 🎉
- motivations - project goals / philosophy
- notes - general notes
- bugs - roughly sorted by chance of encounter
- not my bugs - same order here too
- breaking changes - upgrade notes
- FAQ - "frequently" asked questions
- accounts and volumes - per-folder, per-user permissions
- the browser - accessing a copyparty server using a web-browser
- tabs - the main tabs in the ui
- hotkeys - the browser has the following hotkeys
- navpane - switching between breadcrumbs or navpane
- thumbnails - press
gor田to toggle grid-view instead of the file listing - zip downloads - download folders (or file selections) as
ziportarfiles - uploading - drag files/folders into the web-browser to upload
- file-search - dropping files into the browser also lets you see if they exist on the server
- unpost - undo/delete accidental uploads
- self-destruct - uploads can be given a lifetime
- race the beam - download files while they're still uploading (demo video)
- incoming files - the control-panel shows the ETA for all incoming files
- file manager - cut/paste, rename, and delete files/folders (if you have permission)
- shares - share a file or folder by creating a temporary link
- batch rename - select some files and press
F2to bring up the rename UI - rss feeds - monitor a folder with your RSS reader
- recent uploads - list all recent uploads
- media player - plays almost every audio format there is
- audio equalizer - and dynamic range compressor
- fix unreliable playback on android - due to phone / app settings
- markdown viewer - and there are two editors
- markdown vars - dynamic docs with serverside variable expansion
- other tricks
- searching - search by size, date, path/name, mp3-tags, ...
- server config - using arguments or config files, or a mix of both
- zeroconf - announce enabled services on the LAN (pic)
- qr-code - print a qr-code (screenshot) for quick access
- ftp server - an FTP server can be started using
--ftp 3921 - webdav server - with read-write support
- connecting to webdav from windows - using the GUI
- tftp server - a TFTP server (read/write) can be started using
--tftp 3969 - smb server - unsafe, slow, not recommended for wan
- browser ux - tweaking the ui
- opengraph - discord and social-media embeds
- file deduplication - enable symlink-based upload deduplication
- file indexing - enable music search, upload-undo, and better dedup
- exclude-patterns - to save some time
- filesystem guards - avoid traversing into other filesystems
- periodic rescan - filesystem monitoring
- upload rules - set upload rules using volflags
- compress uploads - files can be autocompressed on upload
- other flags
- database location - in-volume (
.hist/up2k.db, default) or somewhere else - metadata from audio files - set
-e2tto index tags on upload - file parser plugins - provide custom parsers to index additional tags
- event hooks - trigger a program on uploads, renames etc (examples)
- upload events - the older, more powerful approach (examples)
- handlers - redefine behavior with plugins (examples)
- ip auth - autologin based on IP range (CIDR)
- identity providers - replace copyparty passwords with oauth and such
- user-changeable passwords - if permitted, users can change their own passwords
- using the cloud as storage - connecting to an aws s3 bucket and similar
- hiding from google - tell search engines you don't wanna be indexed
- themes
- complete examples
- listen on port 80 and 443 - become a real webserver
- reverse-proxy - running copyparty next to other websites
- real-ip - teaching copyparty how to see client IPs
- prometheus - metrics/stats can be enabled
- other extremely specific features - you'll never find a use for these
- custom mimetypes - change the association of a file extension
- feature chickenbits - buggy feature? rip it out
- packages - the party might be closer than you think
- arch package - now available on aur maintained by @icxes
- fedora package - does not exist yet
- nix package -
nix profile install github:9001/copyparty - nixos module
- browser support - TLDR: yes
- client examples - interact with copyparty using non-browser clients
- folder sync - sync folders to/from copyparty
- mount as drive - a remote copyparty server as a local filesystem
- android app - upload to copyparty with one tap
- iOS shortcuts - there is no iPhone app, but
- performance - defaults are usually fine - expect
8 GiB/sdownload,1 GiB/supload- client-side - when uploading files
- security - there is a discord server
- recovering from crashes
- client crashes
- firefox wsod - firefox 87 can crash during uploads
- client crashes
- HTTP API - see devnotes
- dependencies - mandatory deps
- optional dependencies - install these to enable bonus features
- dependency chickenbits - prevent loading an optional dependency
- optional gpl stuff
- optional dependencies - install these to enable bonus features
- sfx - the self-contained "binary" (recommended!)
- copyparty.exe - download copyparty.exe (win8+) or copyparty32.exe (win7+)
- zipapp - another emergency alternative, copyparty.pyz
- install on android
- reporting bugs - ideas for context to include, and where to submit them
- devnotes - for build instructions etc, see ./docs/devnotes.md
quickstart
just run copyparty-sfx.py -- that's it! 🎉
- or install through pypi:
python3 -m pip install --user -U copyparty - or if you cannot install python, you can use copyparty.exe instead
- or install on arch ╱ on NixOS ╱ through nix
- or if you are on android, install copyparty in termux
- or if your computer is messed up and nothing else works, try the pyz
- or if you prefer to use docker 🐋 you can do that too
- docker has all deps built-in, so skip this step:
enable thumbnails (images/audio/video), media indexing, and audio transcoding by installing some recommended deps:
- Alpine:
apk add py3-pillow ffmpeg - Debian:
apt install --no-install-recommends python3-pil ffmpeg - Fedora: rpmfusion +
dnf install python3-pillow ffmpeg --allowerasing - FreeBSD:
pkg install py39-sqlite3 py39-pillow ffmpeg - MacOS:
port install py-Pillow ffmpeg - MacOS (alternative):
brew install pillow ffmpeg - Windows:
python -m pip install --user -U Pillow- install python and ffmpeg manually; do not use
wingetorMicrosoft Store(it breaks $PATH) - copyparty.exe comes with
Pillowand only needsffmpeg
- install python and ffmpeg manually; do not use
- see optional dependencies to enable even more features
running copyparty without arguments (for example doubleclicking it on Windows) will give everyone read/write access to the current folder; you may want accounts and volumes
or see some usage examples for inspiration, or the complete windows example
some recommended options:
-e2dsaenables general file indexing-e2tsenables audio metadata indexing (needs either FFprobe or Mutagen)-v /mnt/music:/music:r:rw,foo -a foo:barshares/mnt/musicas/music,readable by anyone, and read-write for userfoo, passwordbar- replace
:r:rw,foowith:r,footo only make the folder readable byfooand nobody else - see accounts and volumes (or
--help-accounts) for the syntax and other permissions
- replace
at home
make it accessible over the internet by starting a cloudflare quicktunnel like so:
first download cloudflared and then start the tunnel with cloudflared tunnel --url http://127.0.0.1:3923
as the tunnel starts, it will show a URL which you can share to let anyone browse your stash or upload files to you
since people will be connecting through cloudflare, run copyparty with --xff-hdr cf-connecting-ip to detect client IPs correctly
on servers
you may also want these, especially on servers:
- contrib/systemd/copyparty.service to run copyparty as a systemd service (see guide inside)
- contrib/systemd/prisonparty.service to run it in a chroot (for extra security)
- contrib/openrc/copyparty to run copyparty on Alpine / Gentoo
- contrib/rc/copyparty to run copyparty on FreeBSD
- nixos module to run copyparty on NixOS hosts
- contrib/nginx/copyparty.conf to reverse-proxy behind nginx (for better https)
and remember to open the ports you want; here's a complete example including every feature copyparty has to offer:
firewall-cmd --permanent --add-port={80,443,3921,3923,3945,3990}/tcp # --zone=libvirt
firewall-cmd --permanent --add-port=12000-12099/tcp # --zone=libvirt
firewall-cmd --permanent --add-port={69,1900,3969,5353}/udp # --zone=libvirt
firewall-cmd --reload
(69:tftp, 1900:ssdp, 3921:ftp, 3923:http/https, 3945:smb, 3969:tftp, 3990:ftps, 5353:mdns, 12000:passive-ftp)
features
also see comparison to similar software
- backend stuff
- ☑ IPv6 + unix-sockets
- ☑ multiprocessing (actual multithreading)
- ☑ volumes (mountpoints)
- ☑ accounts
- ☑ ftp server
- ☑ tftp server
- ☑ webdav server
- ☑ smb/cifs server
- ☑ qr-code for quick access
- ☑ upnp / zeroconf / mdns / ssdp
- ☑ event hooks / script runner
- ☑ reverse-proxy support
- upload
- ☑ basic: plain multipart, ie6 support
- ☑ up2k: js, resumable, multithreaded
- no filesize limit! even on Cloudflare
- ☑ stash: simple PUT filedropper
- ☑ filename randomizer
- ☑ write-only folders
- ☑ unpost: undo/delete accidental uploads
- ☑ self-destruct (specified server-side or client-side)
- ☑ race the beam (almost like peer-to-peer)
- ☑ symlink/discard duplicates (content-matching)
- download
- ☑ single files in browser
- ☑ folders as zip / tar files
- ☑ FUSE client (read-only)
- browser
- ☑ navpane (directory tree sidebar)
- ☑ file manager (cut/paste, delete, batch-rename)
- ☑ audio player (with OS media controls and opus/mp3 transcoding)
- ☑ play video files as audio (converted on server)
- ☑ image gallery with webm player
- ☑ textfile browser with syntax hilighting
- ☑ thumbnails
- ☑ ...of images using Pillow, pyvips, or FFmpeg
- ☑ ...of videos using FFmpeg
- ☑ ...of audio (spectrograms) using FFmpeg
- ☑ cache eviction (max-age; maybe max-size eventually)
- ☑ multilingual UI (english, norwegian, chinese, add your own))
- ☑ SPA (browse while uploading)
- server indexing
- ☑ locate files by contents
- ☑ search by name/path/date/size
- ☑ search by ID3-tags etc.
- client support
- ☑ folder sync
- ☑ curl-friendly
- ☑ opengraph (discord embeds)
- markdown
PS: something missing? post any crazy ideas you've got as a feature request or discussion 🤙
testimonials
small collection of user feedback
good enough, surprisingly correct, certified good software, just works, why, wow this is better than nextcloud
motivations
project goals / philosophy
- inverse linux philosophy -- do all the things, and do an okay job
- quick drop-in service to get a lot of features in a pinch
- some of the alternatives might be a better fit for you
- run anywhere, support everything
- as many web-browsers and python versions as possible
- every browser should at least be able to browse, download, upload files
- be a good emergency solution for transferring stuff between ancient boxes
- minimal dependencies
- but optional dependencies adding bonus-features are ok
- everything being plaintext makes it possible to proofread for malicious code
- no preparations / setup necessary, just run the sfx (which is also plaintext)
- as many web-browsers and python versions as possible
- adaptable, malleable, hackable
- no build steps; modify the js/python without needing node.js or anything like that
notes
general notes:
- paper-printing is affected by dark/light-mode! use lightmode for color, darkmode for grayscale
- because no browsers currently implement the media-query to do this properly orz
browser-specific:
- iPhone/iPad: use Firefox to download files
- Android-Chrome: increase "parallel uploads" for higher speed (android bug)
- Android-Firefox: takes a while to select files (their fix for ☝️)
- Desktop-Firefox:
may use gigabytes of RAM if your files are massiveseems to be OK now - Desktop-Firefox: may stop you from unplugging USB flashdrives until you visit
about:memoryand clickMinimize memory usage
server-os-specific:
- RHEL8 / Rocky8: you can run copyparty using
/usr/libexec/platform-python
server notes:
- pypy is supported but regular cpython is faster if you enable the database
bugs
roughly sorted by chance of encounter
-
general:
--th-ff-jpgmay fix video thumbnails on some FFmpeg versions (macos, some linux)--th-ff-swrmay fix audio thumbnails on some FFmpeg versions- if the
up2k.db(filesystem index) is on a samba-share or network disk, you'll get unpredictable behavior if the share is disconnected for a bit- use
--histor thehistvolflag (-v [...]:c,hist=/tmp/foo) to place the db on a local disk instead
- use
- all volumes must exist / be available on startup; up2k (mtp especially) gets funky otherwise
- probably more, pls let me know
-
python 3.4 and older (including 2.7):
- many rare and exciting edge-cases because python didn't handle EINTR yet
- downloads from copyparty may suddenly fail, but uploads should be fine
- many rare and exciting edge-cases because python didn't handle EINTR yet
-
python 2.7 on Windows:
- cannot index non-ascii filenames with
-e2d - cannot handle filenames with mojibake
- cannot index non-ascii filenames with
if you have a new exciting bug to share, see reporting bugs
not my bugs
same order here too
-
Chrome issue 1317069 -- if you try to upload a folder which contains symlinks by dragging it into the browser, the symlinked files will not get uploaded
-
Chrome issue 1352210 -- plaintext http may be faster at filehashing than https (but also extremely CPU-intensive)
-
Chrome issue 383568268 -- filereaders in webworkers can OOM / crash the browser-tab
- copyparty has a workaround which seems to work well enough
-
Firefox issue 1790500 -- entire browser can crash after uploading ~4000 small files
-
Android: music playback randomly stops due to battery usage settings
-
iPhones: the volume control doesn't work because apple doesn't want it to
AudioContextwill probably never be a viable workaround as apple introduces new issues faster than they fix current ones
-
iPhones: the preload feature (in the media-player-options tab) can cause a tiny audio glitch 20sec before the end of each song, but disabling it may cause worse iOS bugs to appear instead
- just a hunch, but disabling preloading may cause playback to stop entirely, or possibly mess with bluetooth speakers
- tried to add a tooltip regarding this but looks like apple broke my tooltips
-
Windows: folders cannot be accessed if the name ends with
.- python or windows bug
-
Windows: msys2-python 3.8.6 occasionally throws
RuntimeError: release unlocked lockwhen leaving a scoped mutex in up2k- this is an msys2 bug, the regular windows edition of python is fine
-
VirtualBox: sqlite throws
Disk I/O Errorwhen running in a VM and the up2k database is in a vboxsf- use
--histor thehistvolflag (-v [...]:c,hist=/tmp/foo) to place the db inside the vm instead - also happens on mergerfs, so put the db elsewhere
- use
-
Ubuntu: dragging files from certain folders into firefox or chrome is impossible
- due to snap security policies -- see
snap connections firefoxfor the allowlist,removable-mediapermits all of/mntand/mediaapparently
- due to snap security policies -- see
breaking changes
upgrade notes
1.9.16(2023-11-04):--stats/prometheus:cpp_bansrenamed tocpp_active_bans, and that +cpp_uptimeare gauges
1.6.0(2023-01-29):- http-api: delete/move is now
POSTinstead ofGET - everything other than
GETandHEADmust pass cors validation
- http-api: delete/move is now
1.5.0(2022-12-03): new chunksize formula for files larger than 128 GiB- users: upgrade to the latest cli uploader if you use that
- devs: update third-party up2k clients (if those even exist)
FAQ
"frequently" asked questions
-
is it possible to block read-access to folders unless you know the exact URL for a particular file inside?
- yes, using the
gpermission, see the examples there - you can also do this with linux filesystem permissions;
chmod 111 musicwill make it possible to access files and folders inside themusicfolder but not list the immediate contents -- also works with other software, not just copyparty
- yes, using the
-
can I link someone to a password-protected volume/file by including the password in the URL?
- yes, by adding
?pw=hunter2to the end; replace?with&if there are parameters in the URL already, meaning it contains a?near the end
- yes, by adding
-
how do I stop
.histfolders from appearing everywhere on my HDD?- by default, a
.histfolder is created inside each volume for the filesystem index, thumbnails, audio transcodes, and markdown document history. Use the--histglobal-option or thehistvolflag to move it somewhere else; see database location
- by default, a
-
can I make copyparty download a file to my server if I give it a URL?
- yes, using hooks
-
firefox refuses to connect over https, saying "Secure Connection Failed" or "SEC_ERROR_BAD_SIGNATURE", but the usual button to "Accept the Risk and Continue" is not shown
- firefox has corrupted its certstore; fix this by exiting firefox, then find and delete the file named
cert9.dbsomewhere in your firefox profile folder
- firefox has corrupted its certstore; fix this by exiting firefox, then find and delete the file named
-
the server keeps saying
thank you for playingwhen I try to access the website- you've gotten banned for malicious traffic! if this happens by mistake, and you're running a reverse-proxy and/or something like cloudflare, see real-ip on how to fix this
-
copyparty seems to think I am using http, even though the URL is https
- your reverse-proxy is not sending the
X-Forwarded-Proto: httpsheader; this could be because your reverse-proxy itself is confused. Ensure that none of the intermediates (such as cloudflare) are terminating https before the traffic hits your entrypoint
- your reverse-proxy is not sending the
-
i want to learn python and/or programming and am considering looking at the copyparty source code in that occasion
-
_| _ __ _ _|_ (_| (_) | | (_) |_
-
accounts and volumes
per-folder, per-user permissions - if your setup is getting complex, consider making a config file instead of using arguments
- much easier to manage, and you can modify the config at runtime with
systemctl reload copypartyor more conveniently using the[reload cfg]button in the control-panel (if the user hasa/admin in any volume)- changes to the
[global]config section requires a restart to take effect
- changes to the
a quick summary can be seen using --help-accounts
configuring accounts/volumes with arguments:
-a usr:pwdadds accountusrwith passwordpwd-v .::radds current-folder.as the webroot,readable by anyone- the syntax is
-v src:dst:perm:perm:...so local-path, url-path, and one or more permissions to set - granting the same permissions to multiple accounts:
-v .::r,usr1,usr2:rw,usr3,usr4= usr1/2 read-only, 3/4 read-write
- the syntax is
permissions:
r(read): browse folder contents, download files, download as zip/tar, see filekeys/dirkeysw(write): upload files, move/copy files into this folderm(move): move files/folders from this folderd(delete): delete files/folders.(dots): user can ask to show dotfiles in directory listingsg(get): only download files, cannot see folder contents or zip/tarG(upget): same asgexcept uploaders get to see their own filekeys (seefkin examples below)h(html): same asgexcept folders return their index.html, and filekeys are not necessary for index.htmla(admin): can see upload time, uploader IPs, config-reloadA("all"): same asrwmda.(read/write/move/delete/admin/dotfiles)
examples:
- add accounts named u1, u2, u3 with passwords p1, p2, p3:
-a u1:p1 -a u2:p2 -a u3:p3 - make folder
/srvthe root of the filesystem, read-only by anyone:-v /srv::r - make folder
/mnt/musicavailable at/music, read-only for u1 and u2, read-write for u3:-v /mnt/music:music:r,u1,u2:rw,u3- unauthorized users accessing the webroot can see that the
musicfolder exists, but cannot open it
- unauthorized users accessing the webroot can see that the
- make folder
/mnt/incomingavailable at/inc, write-only for u1, read-move for u2:-v /mnt/incoming:inc:w,u1:rm,u2- unauthorized users accessing the webroot can see that the
incfolder exists, but cannot open it u1can open theincfolder, but cannot see the contents, only upload new files to itu2can browse it and move files from/incinto any folder whereu2has write-access
- unauthorized users accessing the webroot can see that the
- make folder
/mnt/ssavailable at/i, read-write for u1, get-only for everyone else, and enable filekeys:-v /mnt/ss:i:rw,u1:g:c,fk=4c,fk=4sets thefk(filekey) volflag to 4, meaning each file gets a 4-character accesskeyu1can upload files, browse the folder, and see the generated filekeys- other users cannot browse the folder, but can access the files if they have the full file URL with the filekey
- replacing the
gpermission withwgwould let anonymous users upload files, but not see the required filekey to access it - replacing the
gpermission withwGwould let anonymous users upload files, receiving a working direct link in return
anyone trying to bruteforce a password gets banned according to --ban-pw; default is 24h ban for 9 failed attempts in 1 hour
shadowing
hiding specific subfolders by mounting another volume on top of them
for example -v /mnt::r -v /var/empty:web/certs:r mounts the server folder /mnt as the webroot, but another volume is mounted at /web/certs -- so visitors can only see the contents of /mnt and /mnt/web (at URLs / and /web), but not /mnt/web/certs because URL /web/certs is mapped to /var/empty
dotfiles
unix-style hidden files/folders by starting the name with a dot
anyone can access these if they know the name, but they normally don't appear in directory listings
a client can request to see dotfiles in directory listings if global option -ed is specified, or the volume has volflag dots, or the user has permission .
dotfiles do not appear in search results unless one of the above is true, and the global option / volflag dotsrch is set
the browser
accessing a copyparty server using a web-browser

tabs
the main tabs in the ui
[🔎]search by size, date, path/name, mp3-tags ...[🧯]unpost: undo/delete accidental uploads[🚀]and[🎈]are the uploaders[📂]mkdir: create directories[📝]new-md: create a new markdown document[📟]send-msg: either to server-log or into textfiles if--urlform save[🎺]audio-player config options[⚙️]general client config options
hotkeys
the browser has the following hotkeys (always qwerty)
?show hotkeys helpBtoggle breadcrumbs / navpaneI/Kprev/next folderMparent folder (or unexpand current)Vtoggle folders / textfiles in the navpaneGtoggle list / grid view -- same as田bottom-rightTtoggle thumbnails / iconsESCclose various thingsctrl-Kdelete selected files/foldersctrl-Xcut selected files/foldersctrl-Ccopy selected files/folders to clipboardctrl-Vpaste (move/copy)Ydownload selected filesF2rename selected file/folder- when a file/folder is selected (in not-grid-view):
Up/Downmove cursor- shift+
Up/Downselect and move cursor - ctrl+
Up/Downmove cursor and scroll viewport Spacetoggle file selectionCtrl-Atoggle select all
- when a textfile is open:
I/Kprev/next textfileStoggle selection of open fileMclose textfile
- when playing audio:
J/Lprev/next songU/Oskip 10sec back/forward0..9jump to 0%..90%Pplay/pause (also starts playing the folder)Ydownload file
- when viewing images / playing videos:
J/L, Left/Rightprev/next fileHome/Endfirst/last fileFtoggle fullscreenStoggle selectionRrotate clockwise (shift=ccw)Ydownload fileEscclose viewer- videos:
U/Oskip 10sec back/forward0..9jump to 0%..90%P/K/Spaceplay/pauseMmuteCcontinue playing next videoVloop entire file[loop range (start)]loop range (end)
- when the navpane is open:
A/Dadjust tree width
- in the grid view:
Stoggle multiselect- shift+
A/Dzoom
- in the markdown editor:
^ssave^hheader^kautoformat table^ujump to next unicode character^etoggle editor / preview^up, ^downjump paragraphs
navpane
switching between breadcrumbs or navpane
click the 🌲 or pressing the B hotkey to toggle between breadcrumbs path (default), or a navpane (tree-browser sidebar thing)
[+]and[-](or hotkeysA/D) adjust the size[🎯]jumps to the currently open folder[📃]toggles between showing folders and textfiles[📌]shows the name of all parent folders in a docked panel[a]toggles automatic widening as you go deeper[↵]toggles wordwrap[👀]show full name on hover (if wordwrap is off)
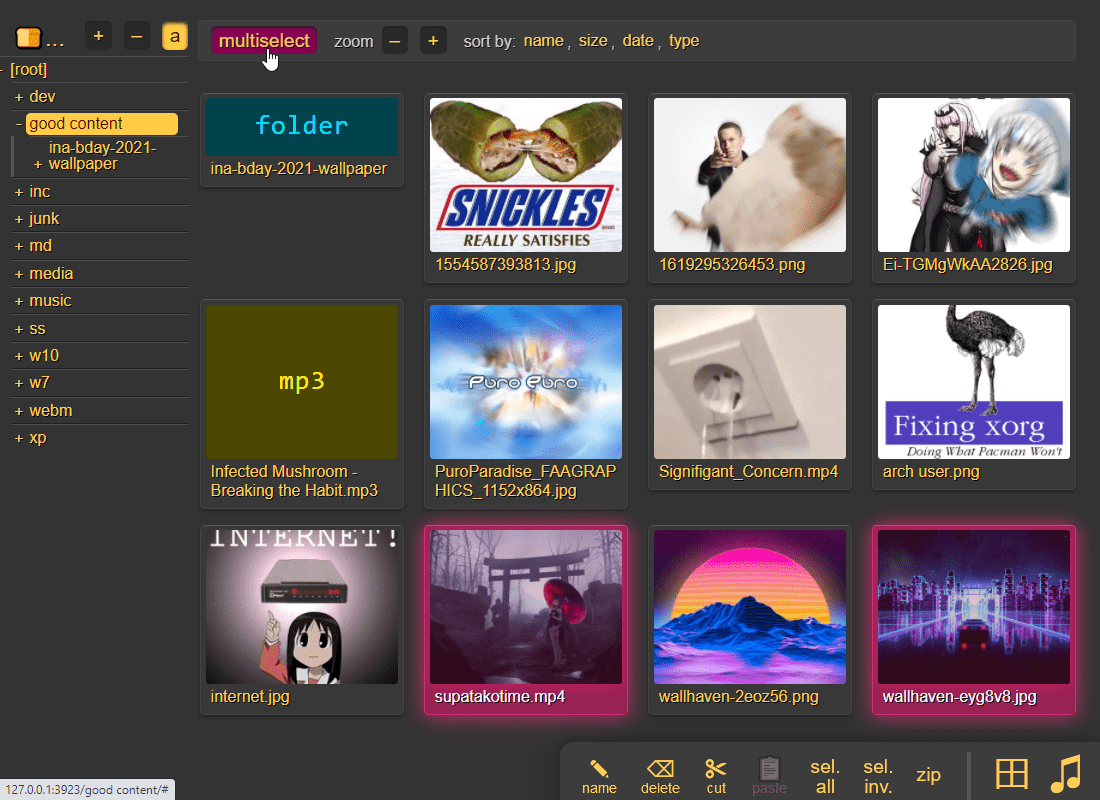
thumbnails
press g or 田 to toggle grid-view instead of the file listing and t toggles icons / thumbnails
- can be made default globally with
--gridor per-volume with volflaggrid - enable by adding
?imgsto a link, or disable with?imgs=0
it does static images with Pillow / pyvips / FFmpeg, and uses FFmpeg for video files, so you may want to --no-thumb or maybe just --no-vthumb depending on how dangerous your users are
- pyvips is 3x faster than Pillow, Pillow is 3x faster than FFmpeg
- disable thumbnails for specific volumes with volflag
dthumbfor all, ordvthumb/dathumb/dithumbfor video/audio/images only
audio files are converted into spectrograms using FFmpeg unless you --no-athumb (and some FFmpeg builds may need --th-ff-swr)
images with the following names (see --th-covers) become the thumbnail of the folder they're in: folder.png, folder.jpg, cover.png, cover.jpg
- the order is significant, so if both
cover.pngandfolder.jpgexist in a folder, it will pick the first matching--th-coversentry (folder.jpg) - and, if you enable file indexing, it will also try those names as dotfiles (
.folder.jpgand so), and then fallback on the first picture in the folder (if it has any pictures at all)
enabling multiselect lets you click files to select them, and then shift-click another file for range-select
multiselectis mostly intended for phones/tablets, but theseloption in the[⚙️] settingstab is better suited for desktop use, allowing selection by CTRL-clicking and range-selection with SHIFT-click, all without affecting regular clicking- the
seloption can be made default globally with--gselor per-volume with volflaggsel
- the
zip downloads
download folders (or file selections) as zip or tar files
select which type of archive you want in the [⚙️] config tab:
| name | url-suffix | description |
|---|---|---|
tar | ?tar | plain gnutar, works great with curl | tar -xv |
pax | ?tar=pax | pax-format tar, futureproof, not as fast |
tgz | ?tar=gz | gzip compressed gnu-tar (slow), for curl | tar -xvz |
txz | ?tar=xz | gnu-tar with xz / lzma compression (v.slow) |
zip | ?zip=utf8 | works everywhere, glitchy filenames on win7 and older |
zip_dos | ?zip | traditional cp437 (no unicode) to fix glitchy filenames |
zip_crc | ?zip=crc | cp437 with crc32 computed early for truly ancient software |
- gzip default level is
3(0=fast, 9=best), change with?tar=gz:9 - xz default level is
1(0=fast, 9=best), change with?tar=xz:9 - bz2 default level is
2(1=fast, 9=best), change with?tar=bz2:9 - hidden files (dotfiles) are excluded unless account is allowed to list them
up2k.dbanddir.txtis always excluded
- bsdtar supports streaming unzipping:
curl foo?zip=utf8 | bsdtar -xv- good, because copyparty's zip is faster than tar on small files
zip_crcwill take longer to download since the server has to read each file twice- this is only to support MS-DOS PKZIP v2.04g (october 1993) and older
- how are you accessing copyparty actually
- this is only to support MS-DOS PKZIP v2.04g (october 1993) and older
you can also zip a selection of files or folders by clicking them in the browser, that brings up a selection editor and zip button in the bottom right
cool trick: download a folder by appending url-params ?tar&opus or ?tar&mp3 to transcode all audio files (except aac|m4a|mp3|ogg|opus|wma) to opus/mp3 before they're added to the archive
- super useful if you're 5 minutes away from takeoff and realize you don't have any music on your phone but your server only has flac files and downloading those will burn through all your data + there wouldn't be enough time anyways
- and url-params
&j/&wproduce jpeg/webm thumbnails/spectrograms instead of the original audio/video/images (&pfor audio waveforms)- can also be used to pregenerate thumbnails; combine with
--th-maxage=9999999or--th-clean=0
- can also be used to pregenerate thumbnails; combine with
uploading
drag files/folders into the web-browser to upload
dragdrop is the recommended way, but you may also:
- select some files (not folders) in your file explorer and press CTRL-V inside the browser window
- use the command-line uploader
- upload using curl or sharex
when uploading files through dragdrop or CTRL-V, this initiates an upload using up2k; there are two browser-based uploaders available:
[🎈] bup, the basic uploader, supports almost every browser since netscape 4.0[🚀] up2k, the good / fancy one
NB: you can undo/delete your own uploads with [🧯] unpost (and this is also where you abort unfinished uploads, but you have to refresh the page first)
up2k has several advantages:
- you can drop folders into the browser (files are added recursively)
- files are processed in chunks, and each chunk is checksummed
- uploads autoresume if they are interrupted by network issues
- uploads resume if you reboot your browser or pc, just upload the same files again
- server detects any corruption; the client reuploads affected chunks
- the client doesn't upload anything that already exists on the server
- no filesize limit, even when a proxy limits the request size (for example Cloudflare)
- much higher speeds than ftp/scp/tarpipe on some internet connections (mainly american ones) thanks to parallel connections
- the last-modified timestamp of the file is preserved
it is perfectly safe to restart / upgrade copyparty while someone is uploading to it!
all known up2k clients will resume just fine 💪
see up2k for details on how it works, or watch a demo video

protip: you can avoid scaring away users with contrib/plugins/minimal-up2k.js which makes it look much simpler
protip: if you enable favicon in the [⚙️] settings tab (by typing something into the textbox), the icon in the browser tab will indicate upload progress -- also, the [🔔] and/or [🔊] switches enable visible and/or audible notifications on upload completion
the up2k UI is the epitome of polished intuitive experiences:
- "parallel uploads" specifies how many chunks to upload at the same time
[🏃]analysis of other files should continue while one is uploading[🥔]shows a simpler UI for faster uploads from slow devices[🎲]generate random filenames during upload[📅]preserve last-modified timestamps; server times will match yours[🔎]switch between upload and file-search mode- ignore
[🔎]if you add files by dragging them into the browser
- ignore
and then theres the tabs below it,
[ok]is the files which completed successfully[ng]is the ones that failed / got rejected (already exists, ...)[done]shows a combined list of[ok]and[ng], chronological order[busy]files which are currently hashing, pending-upload, or uploading- plus up to 3 entries each from
[done]and[que]for context
- plus up to 3 entries each from
[que]is all the files that are still queued
note that since up2k has to read each file twice, [🎈] bup can theoretically be up to 2x faster in some extreme cases (files bigger than your ram, combined with an internet connection faster than the read-speed of your HDD, or if you're uploading from a cuo2duo)
if you are resuming a massive upload and want to skip hashing the files which already finished, you can enable turbo in the [⚙️] config tab, but please read the tooltip on that button
if the server is behind a proxy which imposes a request-size limit, you can configure up2k to sneak below the limit with server-option --u2sz (the default is 96 MiB to support Cloudflare)
file-search
dropping files into the browser also lets you see if they exist on the server

when you drag/drop files into the browser, you will see two dropzones: Upload and Search
on a phone? toggle the
[🔎]switch green before tapping the big yellow Search button to select your files
the files will be hashed on the client-side, and each hash is sent to the server, which checks if that file exists somewhere
files go into [ok] if they exist (and you get a link to where it is), otherwise they land in [ng]
- the main reason filesearch is combined with the uploader is cause the code was too spaghetti to separate it out somewhere else, this is no longer the case but now i've warmed up to the idea too much
unpost
undo/delete accidental uploads using the [🧯] tab in the UI

you can unpost even if you don't have regular move/delete access, however only for files uploaded within the past --unpost seconds (default 12 hours) and the server must be running with -e2d
self-destruct
uploads can be given a lifetime, after which they expire / self-destruct
the feature must be enabled per-volume with the lifetime upload rule which sets the upper limit for how long a file gets to stay on the server
clients can specify a shorter expiration time using the up2k ui -- the relevant options become visible upon navigating into a folder with lifetimes enabled -- or by using the life upload modifier
specifying a custom expiration time client-side will affect the timespan in which unposts are permitted, so keep an eye on the estimates in the up2k ui
race the beam
download files while they're still uploading (demo video) -- it's almost like peer-to-peer
requires the file to be uploaded using up2k (which is the default drag-and-drop uploader), alternatively the command-line program
incoming files
the control-panel shows the ETA for all incoming files , but only for files being uploaded into volumes where you have read-access
file manager
cut/paste, rename, and delete files/folders (if you have permission)
file selection: click somewhere on the line (not the link itself), then:
-
spaceto toggle -
up/downto move -
shift-up/downto move-and-select -
ctrl-shift-up/downto also scroll -
shift-click another line for range-select
-
cut: select some files and
ctrl-x -
copy: select some files and
ctrl-c -
paste:
ctrl-vin another folder -
rename:
F2
you can copy/move files across browser tabs (cut/copy in one tab, paste in another)
shares
share a file or folder by creating a temporary link
when enabled in the server settings (--shr), click the bottom-right share button to share the folder you're currently in, or alternatively:
- select a folder first to share that folder instead
- select one or more files to share only those files
this feature was made with identity providers in mind -- configure your reverseproxy to skip the IdP's access-control for a given URL prefix and use that to safely share specific files/folders sans the usual auth checks
when creating a share, the creator can choose any of the following options:
- password-protection
- expire after a certain time;
0or blank means infinite - allow visitors to upload (if the user who creates the share has write-access)
semi-intentional limitations:
- cleanup of expired shares only works when global option
e2dis set, and/or at least one volume on the server has volflage2d - only folders from the same volume are shared; if you are sharing a folder which contains other volumes, then the contents of those volumes will not be available
- related to IdP volumes being forgotten on shutdown, any shares pointing into a user's IdP volume will be unavailable until that user makes their first request after a restart
- no option to "delete after first access" because tricky
- when linking something to discord (for example) it'll get accessed by their scraper and that would count as a hit
- browsers wouldn't be able to resume a broken download unless the requester's IP gets allowlisted for X minutes (ref. tricky)
specify --shr /foobar to enable this feature; a toplevel virtual folder named foobar is then created, and that's where all the shares will be served from
- you can name it whatever,
foobaris just an example - if you're using config files, put
shr: /foobarinside the[global]section instead
users can delete their own shares in the controlpanel, and a list of privileged users (--shr-adm) are allowed to see and/or delet any share on the server
after a share has expired, it remains visible in the controlpanel for --shr-rt minutes (default is 1 day), and the owner can revive it by extending the expiration time there
security note: using this feature does not mean that you can skip the accounts and volumes section -- you still need to restrict access to volumes that you do not intend to share with unauthenticated users! it is not sufficient to use rules in the reverseproxy to restrict access to just the /share folder.
batch rename
select some files and press F2 to bring up the rename UI

quick explanation of the buttons,
[✅ apply rename]confirms and begins renaming[❌ cancel]aborts and closes the rename window[↺ reset]reverts any filename changes back to the original name[decode]does a URL-decode on the filename, fixing stuff like&and%20[advanced]toggles advanced mode
advanced mode: rename files based on rules to decide the new names, based on the original name (regex), or based on the tags collected from the file (artist/title/...), or a mix of both
in advanced mode,
[case]toggles case-sensitive regexregexis the regex pattern to apply to the original filename; any files which don't match will be skippedformatis the new filename, taking values from regex capturing groups and/or from file tags- very loosely based on foobar2000 syntax
presetslets you save rename rules for later
available functions:
$lpad(text, length, pad_char)$rpad(text, length, pad_char)
so,
say you have a file named meganeko - Eclipse - 07 Sirius A.mp3 (absolutely fantastic album btw) and the tags are: Album:Eclipse, Artist:meganeko, Title:Sirius A, tn:7
you could use just regex to rename it:
regex=(.*) - (.*) - ([0-9]{2}) (.*)format=(3). (1) - (4)output=07. meganeko - Sirius A.mp3
or you could use just tags:
format=$lpad((tn),2,0). (artist) - (title).(ext)output=7. meganeko - Sirius A.mp3
or a mix of both:
regex=- ([0-9]{2})format=(1). (artist) - (title).(ext)output=07. meganeko - Sirius A.mp3
the metadata keys you can use in the format field are the ones in the file-browser table header (whatever is collected with -mte and -mtp)
rss feeds
monitor a folder with your RSS reader , optionally recursive
must be enabled per-volume with volflag rss or globally with --rss
the feed includes itunes metadata for use with podcast readers such as AntennaPod
a feed example: https://cd.ocv.me/a/d2/d22/?rss&fext=mp3
url parameters:
pw=hunter2for password authrecursiveto also include subfolderstitle=foochanges the feed title (default: folder name)fext=mp3,opusonly include mp3 and opus files (default: all)nf=30only show the first 30 results (default: 250)sort=msort by mtime (file last-modified), newest first (default)u= upload-time; NOTE: non-uploaded files have upload-time0n= filenamea= filesize- uppercase = reverse-sort;
M= oldest file first
recent uploads
list all recent uploads by clicking "show recent uploads" in the controlpanel
will show uploader IP and upload-time if the visitor has the admin permission
- global-option
--ups-whenmakes upload-time visible to all users, and not just admins
note that the 🧯 unpost feature is better suited for viewing your own recent uploads, as it includes the option to undo/delete them
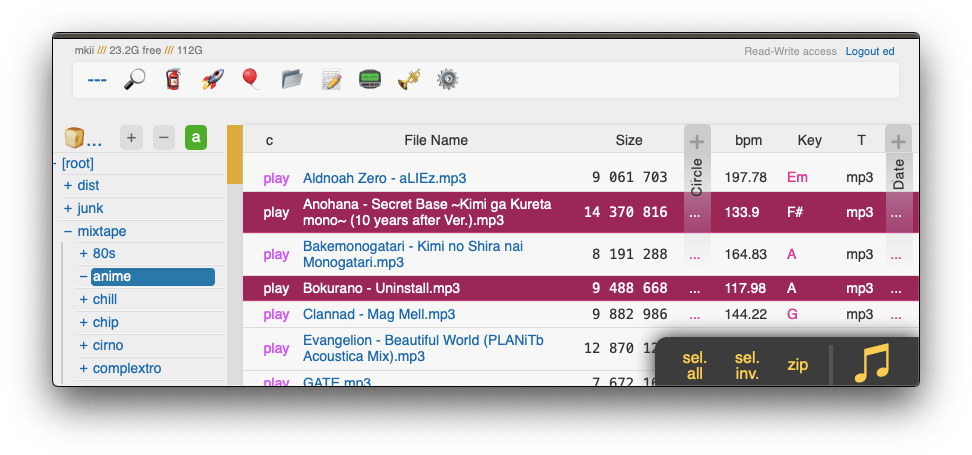
media player
plays almost every audio format there is (if the server has FFmpeg installed for on-demand transcoding)
the following audio formats are usually always playable, even without FFmpeg: aac|flac|m4a|mp3|ogg|opus|wav
some hilights:
- OS integration; control playback from your phone's lockscreen (windows // iOS // android)
- shows the audio waveform in the seekbar
- not perfectly gapless but can get really close (see settings + eq below); good enough to enjoy gapless albums as intended
- videos can be played as audio, without wasting bandwidth on the video
click the play link next to an audio file, or copy the link target to share it (optionally with a timestamp to start playing from, like that example does)
open the [🎺] media-player-settings tab to configure it,
- "switches":
[🔀]shuffles the files inside each folder[preload]starts loading the next track when it's about to end, reduces the silence between songs[full]does a full preload by downloading the entire next file; good for unreliable connections, bad for slow connections[~s]toggles the seekbar waveform display[/np]enables buttons to copy the now-playing info as an irc message[os-ctl]makes it possible to control audio playback from the lockscreen of your device (enables mediasession)[seek]allows seeking with lockscreen controls (buggy on some devices)[art]shows album art on the lockscreen[🎯]keeps the playing song scrolled into view (good when using the player as a taskbar dock)[⟎]shrinks the playback controls
- "buttons":
[uncache]may fix songs that won't play correctly due to bad files in browser cache
- "at end of folder":
[loop]keeps looping the folder[next]plays into the next folder
- "transcode":
[flac]convertsflacandwavfiles into opus (if supported by browser) or mp3[aac]convertsaacandm4afiles into opus (if supported by browser) or mp3[oth]converts all other known formats into opus (if supported by browser) or mp3aac|ac3|aif|aiff|alac|alaw|amr|ape|au|dfpwm|dts|flac|gsm|it|m4a|mo3|mod|mp2|mp3|mpc|mptm|mt2|mulaw|ogg|okt|opus|ra|s3m|tak|tta|ulaw|wav|wma|wv|xm|xpk
- "tint" reduces the contrast of the playback bar
audio equalizer
can also boost the volume in general, or increase/decrease stereo width (like crossfeed just worse)
has the convenient side-effect of reducing the pause between songs, so gapless albums play better with the eq enabled (just make it flat)
not available on iPhones / iPads because AudioContext currently breaks background audio playback on iOS (15.7.8)
fix unreliable playback on android
due to phone / app settings, android phones may randomly stop playing music when the power saver kicks in, especially at the end of an album -- you can fix it by disabling power saving in the app settings of the browser you use for music streaming (preferably a dedicated one)
markdown viewer
and there are two editors

there is a built-in extension for inline clickable thumbnails;
- enable it by adding
<!-- th -->somewhere in the doc - add thumbnails with
!th[l](your.jpg)wherelmeans left-align (r= right-align) - a single line with
---clears the float / inlining - in the case of README.md being displayed below a file listing, thumbnails will open in the gallery viewer
other notes,
- the document preview has a max-width which is the same as an A4 paper when printed
markdown vars
dynamic docs with serverside variable expansion to replace stuff like {{self.ip}} with the client's IP, or {{srv.htime}} with the current time on the server
see ./srv/expand/ for usage and examples
other tricks
-
you can link a particular timestamp in an audio file by adding it to the URL, such as
&20/&20s/&1m20/&t=1:20after the.../#af-c8960dab -
enabling the audio equalizer can help make gapless albums fully gapless in some browsers (chrome), so consider leaving it on with all the values at zero
-
get a plaintext file listing by adding
?ls=tto a URL, or a compact colored one with?ls=v(for unix terminals) -
if you are using media hotkeys to switch songs and are getting tired of seeing the OSD popup which Windows doesn't let you disable, consider ./contrib/media-osd-bgone.ps1
-
click the bottom-left
πto open a javascript prompt for debugging -
files named
.prologue.html/.epilogue.htmlwill be rendered before/after directory listings unless--no-logues -
files named
descript.ion/DESCRIPT.IONare parsed and displayed in the file listing, or as the epilogue if nonstandard -
files named
README.md/readme.mdwill be rendered after directory listings unless--no-readme(but.epilogue.htmltakes precedence)- and
PREADME.md/preadme.mdis shown above directory listings unless--no-readmeor.prologue.html
- and
-
README.mdand*logue.htmlcan contain placeholder values which are replaced server-side before embedding into directory listings; see--help-exp
searching
search by size, date, path/name, mp3-tags, ...

when started with -e2dsa copyparty will scan/index all your files. This avoids duplicates on upload, and also makes the volumes searchable through the web-ui:
- make search queries by
size/date/directory-path/filename, or... - drag/drop a local file to see if the same contents exist somewhere on the server, see file-search
path/name queries are space-separated, AND'ed together, and words are negated with a - prefix, so for example:
- path:
shibayan -bossafinds all files where one of the folders containshibayanbut filters out any results wherebossaexists somewhere in the path - name:
demetori styxgives you good stuff
the raw field allows for more complex stuff such as ( tags like *nhato* or tags like *taishi* ) and ( not tags like *nhato* or not tags like *taishi* ) which finds all songs by either nhato or taishi, excluding collabs (terrible example, why would you do that)
for the above example to work, add the commandline argument -e2ts to also scan/index tags from music files, which brings us over to:
server config
using arguments or config files, or a mix of both:
- config files (
-c some.conf) can set additional commandline arguments; see ./docs/example.conf and ./docs/example2.conf kill -s USR1(same assystemctl reload copyparty) to reload accounts and volumes from config files without restarting- or click the
[reload cfg]button in the control-panel if the user hasa/admin in any volume - changes to the
[global]config section requires a restart to take effect
- or click the
NB: as humongous as this readme is, there is also a lot of undocumented features. Run copyparty with --help to see all available global options; all of those can be used in the [global] section of config files, and everything listed in --help-flags can be used in volumes as volflags.
- if running in docker/podman, try this:
docker run --rm -it copyparty/ac --help - or see this (probably outdated): https://ocv.me/copyparty/helptext.html
- or if you prefer plaintext, https://ocv.me/copyparty/helptext.txt
zeroconf
announce enabled services on the LAN (pic) -- -z enables both mdns and ssdp
--z-on/--z-off' limits the feature to certain networks
mdns
LAN domain-name and feature announcer
uses multicast dns to give copyparty a domain which any machine on the LAN can use to access it
all enabled services (webdav, ftp, smb) will appear in mDNS-aware file managers (KDE, gnome, macOS, ...)
the domain will be partybox.local if the machine's hostname is partybox unless --name specifies something else
and the web-UI will be available at http://partybox.local:3923/
- if you want to get rid of the
:3923so you can use http://partybox.local/ instead then see listen on port 80 and 443
ssdp
windows-explorer announcer
uses ssdp to make copyparty appear in the windows file explorer on all machines on the LAN
doubleclicking the icon opens the "connect" page which explains how to mount copyparty as a local filesystem
if copyparty does not appear in windows explorer, use --zsv to see why:
- maybe the discovery multicast was sent from an IP which does not intersect with the server subnets
qr-code
print a qr-code (screenshot) for quick access, great between phones on android hotspots which keep changing the subnet
--qrenables it--qrsdoes https instead of http--qrl lootbox/?pw=hunter2appends to the url, linking to thelootboxfolder with passwordhunter2--qrz 1forces 1x zoom instead of autoscaling to fit the terminal size- 1x may render incorrectly on some terminals/fonts, but 2x should always work
it uses the server hostname if mdns is enabled, otherwise it'll use your external ip (default route) unless --qri specifies a specific ip-prefix or domain
ftp server
an FTP server can be started using --ftp 3921, and/or --ftps for explicit TLS (ftpes)
- based on pyftpdlib
- needs a dedicated port (cannot share with the HTTP/HTTPS API)
- uploads are not resumable -- delete and restart if necessary
- runs in active mode by default, you probably want
--ftp-pr 12000-13000- if you enable both
ftpandftps, the port-range will be divided in half - some older software (filezilla on debian-stable) cannot passive-mode with TLS
- if you enable both
- login with any username + your password, or put your password in the username field
some recommended FTP / FTPS clients; wark = example password:
- https://winscp.net/eng/download.php
- https://filezilla-project.org/ struggles a bit with ftps in active-mode, but is fine otherwise
- https://rclone.org/ does FTPS with
tls=false explicit_tls=true lftp -u k,wark -p 3921 127.0.0.1 -e lslftp -u k,wark -p 3990 127.0.0.1 -e 'set ssl:verify-certificate no; ls'
webdav server
with read-write support, supports winXP and later, macos, nautilus/gvfs ... a great way to access copyparty straight from the file explorer in your OS
click the connect button in the control-panel to see connection instructions for windows, linux, macos
general usage:
- login with any username + your password, or put your password in the username field (password field can be empty/whatever)
on macos, connect from finder:
- [Go] -> [Connect to Server...] -> http://192.168.123.1:3923/
in order to grant full write-access to webdav clients, the volflag daw must be set and the account must also have delete-access (otherwise the client won't be allowed to replace the contents of existing files, which is how webdav works)
connecting to webdav from windows
using the GUI (winXP or later):
- rightclick [my computer] -> [map network drive] -> Folder:
http://192.168.123.1:3923/- on winXP only, click the
Sign up for online storagehyperlink instead and put the URL there - providing your password as the username is recommended; the password field can be anything or empty
- on winXP only, click the
the webdav client that's built into windows has the following list of bugs; you can avoid all of these by connecting with rclone instead:
- win7+ doesn't actually send the password to the server when reauthenticating after a reboot unless you first try to login with an incorrect password and then switch to the correct password
- or just type your password into the username field instead to get around it entirely
- connecting to a folder which allows anonymous read will make writing impossible, as windows has decided it doesn't need to login
- workaround: connect twice; first to a folder which requires auth, then to the folder you actually want, and leave both of those mounted
- or set the server-option
--dav-authto force password-auth for all webdav clients
- win7+ may open a new tcp connection for every file and sometimes forgets to close them, eventually needing a reboot
- maybe NIC-related (??), happens with win10-ltsc on e1000e but not virtio
- windows cannot access folders which contain filenames with invalid unicode or forbidden characters (
<>:"/\|?*), or names ending with. - winxp cannot show unicode characters outside of some range
- latin-1 is fine, hiragana is not (not even as shift-jis on japanese xp)
tftp server
a TFTP server (read/write) can be started using --tftp 3969 (you probably want ftp instead unless you are actually communicating with hardware from the 90s (in which case we should definitely hang some time))
that makes this the first RTX DECT Base that has been updated using copyparty 🎉
- based on partftpy
- no accounts; read from world-readable folders, write to world-writable, overwrite in world-deletable
- needs a dedicated port (cannot share with the HTTP/HTTPS API)
- run as root (or see below) to use the spec-recommended port
69(nice)
- run as root (or see below) to use the spec-recommended port
- can reply from a predefined portrange (good for firewalls)
- only supports the binary/octet/image transfer mode (no netascii)
- RFC 7440 is not supported, so will be extremely slow over WAN
- assuming default blksize (512), expect 1100 KiB/s over 100BASE-T, 400-500 KiB/s over wifi, 200 on bad wifi
most clients expect to find TFTP on port 69, but on linux and macos you need to be root to listen on that. Alternatively, listen on 3969 and use NAT on the server to forward 69 to that port;
- on linux:
iptables -t nat -A PREROUTING -i eth0 -p udp --dport 69 -j REDIRECT --to-port 3969
some recommended TFTP clients:
- curl (cross-platform, read/write)
- get:
curl --tftp-blksize 1428 tftp://127.0.0.1:3969/firmware.bin - put:
curl --tftp-blksize 1428 -T firmware.bin tftp://127.0.0.1:3969/
- get:
- windows:
tftp.exe(you probably already have it)tftp -i 127.0.0.1 put firmware.bin
- linux:
tftp-hpa,atftpatftp --option "blksize 1428" 127.0.0.1 3969 -p -l firmware.bin -r firmware.bintftp -v -m binary 127.0.0.1 3969 -c put firmware.bin
smb server
unsafe, slow, not recommended for wan, enable with --smb for read-only or --smbw for read-write
click the connect button in the control-panel to see connection instructions for windows, linux, macos
dependencies: python3 -m pip install --user -U impacket==0.11.0
- newer versions of impacket will hopefully work just fine but there is monkeypatching so maybe not
some BIG WARNINGS specific to SMB/CIFS, in decreasing importance:
- not entirely confident that read-only is read-only
- the smb backend is not fully integrated with vfs, meaning there could be security issues (path traversal). Please use
--smb-port(see below) and prisonparty- account passwords work per-volume as expected, and so does account permissions (read/write/move/delete), but
--smbwmust be given to allow write-access from smb - shadowing probably works as expected but no guarantees
- account passwords work per-volume as expected, and so does account permissions (read/write/move/delete), but
and some minor issues,
- clients only see the first ~400 files in big folders;
- this was originally due to impacket#1433 which was fixed in impacket-0.12, so you can disable the workaround with
--smb-nwa-1but then you get unacceptably poor performance instead
- this was originally due to impacket#1433 which was fixed in impacket-0.12, so you can disable the workaround with
- hot-reload of server config (
/?reload=cfg) does not include the[global]section (commandline args) - listens on the first IPv4
-iinterface only (default = :: = 0.0.0.0 = all) - login doesn't work on winxp, but anonymous access is ok -- remove all accounts from copyparty config for that to work
- win10 onwards does not allow connecting anonymously / without accounts
- python3 only
- slow (the builtin webdav support in windows is 5x faster, and rclone-webdav is 30x faster)
known client bugs:
- on win7 only,
--smb1is much faster than smb2 (default) because it keeps rescanning folders on smb2- however smb1 is buggy and is not enabled by default on win10 onwards
- windows cannot access folders which contain filenames with invalid unicode or forbidden characters (
<>:"/\|?*), or names ending with.
the smb protocol listens on TCP port 445, which is a privileged port on linux and macos, which would require running copyparty as root. However, this can be avoided by listening on another port using --smb-port 3945 and then using NAT on the server to forward the traffic from 445 to there;
- on linux:
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 445 -j REDIRECT --to-port 3945
authenticate with one of the following:
- username
$username, password$password - username
$password, passwordk
browser ux
tweaking the ui
- set default sort order globally with
--sortor per-volume with thesortvolflag; specify one or more comma-separated columns to sort by, and prefix the column name with-for reverse sort- the column names you can use are visible as tooltips when hovering over the column headers in the directory listing, for example
href ext sz ts tags/.up_at tags/Circle tags/.tn tags/Artist tags/Title - to sort in music order (album, track, artist, title) with filename as fallback, you could
--sort tags/Circle,tags/.tn,tags/Artist,tags/Title,href - to sort by upload date, first enable showing the upload date in the listing with
-e2d -mte +.up_atand then--sort tags/.up_at
- the column names you can use are visible as tooltips when hovering over the column headers in the directory listing, for example
see ./docs/rice for more, including how to add stuff (css/<meta>/...) to the html <head> tag, or to add your own translation
opengraph
discord and social-media embeds
can be enabled globally with --og or per-volume with volflag og
note that this disables hotlinking because the opengraph spec demands it; to sneak past this intentional limitation, you can enable opengraph selectively by user-agent, for example --og-ua '(Discord|Twitter|Slack)bot' (or volflag og_ua)
you can also hotlink files regardless by appending ?raw to the url
if you want to entirely replace the copyparty response with your own jinja2 template, give the template filepath to --og-tpl or volflag og_tpl (all members of HttpCli are available through the this object)
file deduplication
enable symlink-based upload deduplication globally with --dedup or per-volume with volflag dedup
by default, when someone tries to upload a file that already exists on the server, the upload will be politely declined, and the server will copy the existing file over to where the upload would have gone
if you enable deduplication with --dedup then it'll create a symlink instead of a full copy, thus reducing disk space usage
- on the contrary, if your server is hooked up to s3-glacier or similar storage where reading is expensive, and you cannot use
--safe-dedup=1because you have other software tampering with your files, so you want to entirely disable detection of duplicate data instead, then you can specify--no-cloneglobally ornocloneas a volflag
warning: when enabling dedup, you should also:
- enable indexing with
-e2dsaor volflage2dsa(see file indexing section below); strongly recommended - ...and/or
--hardlink-onlyto use hardlink-based deduplication instead of symlinks; see explanation below
it will not be safe to rename/delete files if you only enable dedup and none of the above; if you enable indexing then it is not necessary to also do hardlinks (but you may still want to)
by default, deduplication is done based on symlinks (symbolic links); these are tiny files which are pointers to the nearest full copy of the file
you can choose to use hardlinks instead of softlinks, globally with --hardlink-only or volflag hardlinkonly;
advantages of using hardlinks:
- hardlinks are more compatible with other software; they behave entirely like regular files
- you can safely move and rename files using other file managers
- symlinks need to be managed by copyparty to ensure the destinations remain correct
advantages of using symlinks (default):
- each symlink can have its own last-modified timestamp, but a single timestamp is shared by all hardlinks
- symlinks make it more obvious to other software that the file is not a regular file, so this can be less dangerous
- hardlinks look like regular files, so other software may assume they are safe to edit without affecting the other copies
warning: if you edit the contents of a deduplicated file, then you will also edit all other copies of that file! This is especially surprising with hardlinks, because they look like regular files, but that same file exists in multiple locations
global-option --xlink / volflag xlink additionally enables deduplication across volumes, but this is probably buggy and not recommended
file indexing
enable music search, upload-undo, and better dedup
file indexing relies on two database tables, the up2k filetree (-e2d) and the metadata tags (-e2t), stored in .hist/up2k.db. Configuration can be done through arguments, volflags, or a mix of both.
through arguments:
-e2denables file indexing on upload-e2dsalso scans writable folders for new files on startup-e2dsaalso scans all mounted volumes (including readonly ones)-e2tenables metadata indexing on upload-e2tsalso scans for tags in all files that don't have tags yet-e2tsralso deletes all existing tags, doing a full reindex-e2vverifies file integrity at startup, comparing hashes from the db-e2vupatches the database with the new hashes from the filesystem-e2vppanics and kills copyparty instead
the same arguments can be set as volflags, in addition to d2d, d2ds, d2t, d2ts, d2v for disabling:
-v ~/music::r:c,e2ds,e2tsrdoes a full reindex of everything on startup-v ~/music::r:c,d2ddisables all indexing, even if any-e2*are on-v ~/music::r:c,d2tdisables all-e2t*(tags), does not affect-e2d*-v ~/music::r:c,d2dsdisables on-boot scans; only index new uploads-v ~/music::r:c,d2tssame except only affecting tags
note:
- upload-times can be displayed in the file listing by enabling the
.up_atmetadata key, either globally with-e2d -mte +.up_ator per-volume with volflagse2d,mte=+.up_at(will have a ~17% performance impact on directory listings) e2tsris probably always overkill, sincee2ds/e2dsawould pick up any file modifications ande2tswould then reindex those, unless there is a new copyparty version with new parsers and the release note says otherwise- the rescan button in the admin panel has no effect unless the volume has
-e2dsor higher
exclude-patterns
to save some time, you can provide a regex pattern for filepaths to only index by filename/path/size/last-modified (and not the hash of the file contents) by setting --no-hash '\.iso$' or the volflag :c,nohash=\.iso$, this has the following consequences:
- initial indexing is way faster, especially when the volume is on a network disk
- makes it impossible to file-search
- if someone uploads the same file contents, the upload will not be detected as a dupe, so it will not get symlinked or rejected
similarly, you can fully ignore files/folders using --no-idx [...] and :c,noidx=\.iso$
- when running on macos, all the usual apple metadata files are excluded by default
if you set --no-hash [...] globally, you can enable hashing for specific volumes using flag :c,nohash=
to exclude certain filepaths from search-results, use --srch-excl or volflag srch_excl instead of --no-idx, for example --srch-excl 'password|logs/[0-9]'
filesystem guards
avoid traversing into other filesystems using --xdev / volflag :c,xdev, skipping any symlinks or bind-mounts to another HDD for example
and/or you can --xvol / :c,xvol to ignore all symlinks leaving the volume's top directory, but still allow bind-mounts pointing elsewhere
- symlinks are permitted with
xvolif they point into another volume where the user has the same level of access
these options will reduce performance; unlikely worst-case estimates are 14% reduction for directory listings, 35% for download-as-tar
as of copyparty v1.7.0 these options also prevent file access at runtime -- in previous versions it was just hints for the indexer
periodic rescan
filesystem monitoring; if copyparty is not the only software doing stuff on your filesystem, you may want to enable periodic rescans to keep the index up to date
argument --re-maxage 60 will rescan all volumes every 60 sec, same as volflag :c,scan=60 to specify it per-volume
uploads are disabled while a rescan is happening, so rescans will be delayed by --db-act (default 10 sec) when there is write-activity going on (uploads, renames, ...)
upload rules
set upload rules using volflags, some examples:
:c,sz=1k-3msets allowed filesize between 1 KiB and 3 MiB inclusive (suffixes:b,k,m,g):c,df=4gblock uploads if there would be less than 4 GiB free disk space afterwards:c,vmaxb=1gblock uploads if total volume size would exceed 1 GiB afterwards:c,vmaxn=4kblock uploads if volume would contain more than 4096 files afterwards:c,nosubdisallow uploading into subdirectories; goes well withrotnandrotf::c,rotn=1000,2moves uploads into subfolders, up to 1000 files in each folder before making a new one, two levels deep (must be at least 1):c,rotf=%Y/%m/%d/%Henforces files to be uploaded into a structure of subfolders according to that date format- if someone uploads to
/foo/barthe path would be rewritten to/foo/bar/2021/08/06/23for example - but the actual value is not verified, just the structure, so the uploader can choose any values which conform to the format string
- just to avoid additional complexity in up2k which is enough of a mess already
- if someone uploads to
:c,lifetime=300delete uploaded files when they become 5 minutes old
you can also set transaction limits which apply per-IP and per-volume, but these assume -j 1 (default) otherwise the limits will be off, for example -j 4 would allow anywhere between 1x and 4x the limits you set depending on which processing node the client gets routed to
:c,maxn=250,3600allows 250 files over 1 hour from each IP (tracked per-volume):c,maxb=1g,300allows 1 GiB total over 5 minutes from each IP (tracked per-volume)
notes:
vmaxbandvmaxnrequires either thee2dsvolflag or-e2dsaglobal-option
compress uploads
files can be autocompressed on upload, either on user-request (if config allows) or forced by server-config
- volflag
gzallows gz compression - volflag
xzallows lzma compression - volflag
pkforces compression on all files - url parameter
pkrequests compression with server-default algorithm - url parameter
gzorxzrequests compression with a specific algorithm - url parameter
xzrequests xz compression
things to note,
- the
gzandxzarguments take a single optional argument, the compression level (range 0 to 9) - the
pkvolflag takes the optional argumentALGORITHM,LEVELwhich will then be forced for all uploads, for examplegz,9orxz,0 - default compression is gzip level 9
- all upload methods except up2k are supported
- the files will be indexed after compression, so dupe-detection and file-search will not work as expected
some examples,
-v inc:inc:w:c,pk=xz,0
folder named inc, shared at inc, write-only for everyone, forces xz compression at level 0-v inc:inc:w:c,pk
same write-only inc, but forces gz compression (default) instead of xz-v inc:inc:w:c,gz
allows (but does not force) gz compression if client uploads to/inc?pkor/inc?gzor/inc?gz=4
other flags
:c,magicenables filetype detection for nameless uploads, same as--magic- needs https://pypi.org/project/python-magic/
python3 -m pip install --user -U python-magic - on windows grab this instead
python3 -m pip install --user -U python-magic-bin
- needs https://pypi.org/project/python-magic/
database location
in-volume (.hist/up2k.db, default) or somewhere else
copyparty creates a subfolder named .hist inside each volume where it stores the database, thumbnails, and some other stuff
this can instead be kept in a single place using the --hist argument, or the hist= volflag, or a mix of both:
--hist ~/.cache/copyparty -v ~/music::r:c,hist=-sets~/.cache/copypartyas the default place to put volume info, but~/musicgets the regular.histsubfolder (-restores default behavior)
note:
- markdown edits are always stored in a local
.histsubdirectory - on windows the volflag path is cyglike, so
/c/tempmeansC:\tempbut use regular paths for--hist- you can use cygpaths for volumes too,
-v C:\Users::rand-v /c/users::rboth work
- you can use cygpaths for volumes too,
metadata from audio files
set -e2t to index tags on upload
-mte decides which tags to index and display in the browser (and also the display order), this can be changed per-volume:
-v ~/music::r:c,mte=title,artistindexes and displays title followed by artist
if you add/remove a tag from mte you will need to run with -e2tsr once to rebuild the database, otherwise only new files will be affected
but instead of using -mte, -mth is a better way to hide tags in the browser: these tags will not be displayed by default, but they still get indexed and become searchable, and users can choose to unhide them in the [⚙️] config pane
-mtm can be used to add or redefine a metadata mapping, say you have media files with foo and bar tags and you want them to display as qux in the browser (preferring foo if both are present), then do -mtm qux=foo,bar and now you can -mte artist,title,qux
tags that start with a . such as .bpm and .dur(ation) indicate numeric value
see the beautiful mess of a dictionary in mtag.py for the default mappings (should cover mp3,opus,flac,m4a,wav,aif,)
--no-mutagen disables Mutagen and uses FFprobe instead, which...
- is about 20x slower than Mutagen
- catches a few tags that Mutagen doesn't
- melodic key, video resolution, framerate, pixfmt
- avoids pulling any GPL code into copyparty
- more importantly runs FFprobe on incoming files which is bad if your FFmpeg has a cve
--mtag-to sets the tag-scan timeout; very high default (60 sec) to cater for zfs and other randomly-freezing filesystems. Lower values like 10 are usually safe, allowing for faster processing of tricky files
file parser plugins
provide custom parsers to index additional tags, also see ./bin/mtag/README.md
copyparty can invoke external programs to collect additional metadata for files using mtp (either as argument or volflag), there is a default timeout of 60sec, and only files which contain audio get analyzed by default (see ay/an/ad below)
-mtp .bpm=~/bin/audio-bpm.pywill execute~/bin/audio-bpm.pywith the audio file as argument 1 to provide the.bpmtag, if that does not exist in the audio metadata-mtp key=f,t5,~/bin/audio-key.pyuses~/bin/audio-key.pyto get thekeytag, replacing any existing metadata tag (f,), aborting if it takes longer than 5sec (t5,)-v ~/music::r:c,mtp=.bpm=~/bin/audio-bpm.py:c,mtp=key=f,t5,~/bin/audio-key.pyboth as a per-volume config wow this is getting ugly
but wait, there's more! -mtp can be used for non-audio files as well using the a flag: ay only do audio files (default), an only do non-audio files, or ad do all files (d as in dontcare)
- "audio file" also means videos btw, as long as there is an audio stream
-mtp ext=an,~/bin/file-ext.pyruns~/bin/file-ext.pyto get theexttag only if file is not audio (an)-mtp arch,built,ver,orig=an,eexe,edll,~/bin/exe.pyruns~/bin/exe.pyto get properties about windows-binaries only if file is not audio (an) and file extension is exe or dll- if you want to daisychain parsers, use the
pflag to set processing order-mtp foo=p1,~/a.pyruns before-mtp foo=p2,~/b.pyand will forward all the tags detected so far as json to the stdin of b.py
- option
c0disables capturing of stdout/stderr, so copyparty will not receive any tags from the process at all -- instead the invoked program is free to print whatever to the console, just using copyparty as a launcherc1captures stdout only,c2only stderr, andc3(default) captures both
- you can control how the parser is killed if it times out with option
ktkilling the entire process tree (default),kmjust the main process, orknlet it continue running until copyparty is terminated
if something doesn't work, try --mtag-v for verbose error messages
event hooks
trigger a program on uploads, renames etc (examples)
you can set hooks before and/or after an event happens, and currently you can hook uploads, moves/renames, and deletes
there's a bunch of flags and stuff, see --help-hooks
if you want to write your own hooks, see devnotes
upload events
the older, more powerful approach (examples):
-v /mnt/inc:inc:w:c,mte=+x1:c,mtp=x1=ad,kn,/usr/bin/notify-send
so filesystem location /mnt/inc shared at /inc, write-only for everyone, appending x1 to the list of tags to index (mte), and using /usr/bin/notify-send to "provide" tag x1 for any filetype (ad) with kill-on-timeout disabled (kn)
that'll run the command notify-send with the path to the uploaded file as the first and only argument (so on linux it'll show a notification on-screen)
note that this is way more complicated than the new event hooks but this approach has the following advantages:
- non-blocking and multithreaded; doesn't hold other uploads back
- you get access to tags from FFmpeg and other mtp parsers
- only trigger on new unique files, not dupes
note that it will occupy the parsing threads, so fork anything expensive (or set kn to have copyparty fork it for you) -- otoh if you want to intentionally queue/singlethread you can combine it with --mtag-mt 1
handlers
redefine behavior with plugins (examples)
replace 404 and 403 errors with something completely different (that's it for now)
ip auth
autologin based on IP range (CIDR) , using the global-option --ipu
for example, if everyone with an IP that starts with 192.168.123 should automatically log in as the user spartacus, then you can either specify --ipu=192.168.123.0/24=spartacus as a commandline option, or put this in a config file:
[global]
ipu: 192.168.123.0/24=spartacus
repeat the option to map additional subnets
be careful with this one! if you have a reverseproxy, then you definitely want to make sure you have real-ip configured correctly, and it's probably a good idea to nullmap the reverseproxy's IP just in case; so if your reverseproxy is sending requests from 172.24.27.9 then that would be --ipu=172.24.27.9/32=
identity providers
replace copyparty passwords with oauth and such
you can disable the built-in password-based login system, and instead replace it with a separate piece of software (an identity provider) which will then handle authenticating / authorizing of users; this makes it possible to login with passkeys / fido2 / webauthn / yubikey / ldap / active directory / oauth / many other single-sign-on contraptions
- the regular config-defined users will be used as a fallback for requests which don't include a valid (trusted) IdP username header
some popular identity providers are Authelia (config-file based) and authentik (GUI-based, more complex)
there is a docker-compose example which is hopefully a good starting point (alternatively see ./docs/idp.md if you're the DIY type)
a more complete example of the copyparty configuration options look like this
but if you just want to let users change their own passwords, then you probably want user-changeable passwords instead
user-changeable passwords
if permitted, users can change their own passwords in the control-panel
-
not compatible with identity providers
-
must be enabled with
--chpwbecause account-sharing is a popular usecase- if you want to enable the feature but deny password-changing for a specific list of accounts, you can do that with
--chpw-no name1,name2,name3,...
- if you want to enable the feature but deny password-changing for a specific list of accounts, you can do that with
-
to perform a password reset, edit the server config and give the user another password there, then do a config reload or server restart
-
the custom passwords are kept in a textfile at filesystem-path
--chpw-db, by defaultchpw.jsonin the copyparty config folder-
if you run multiple copyparty instances with different users you almost definitely want to specify separate DBs for each instance
-
if password hashing is enabled, the passwords in the db are also hashed
- ...which means that all user-defined passwords will be forgotten if you change password-hashing settings
-
using the cloud as storage
connecting to an aws s3 bucket and similar
there is no built-in support for this, but you can use FUSE-software such as rclone / geesefs / JuiceFS to first mount your cloud storage as a local disk, and then let copyparty use (a folder in) that disk as a volume
you may experience poor upload performance this way, but that can sometimes be fixed by specifying the volflag sparse to force the use of sparse files; this has improved the upload speeds from 1.5 MiB/s to over 80 MiB/s in one case, but note that you are also more likely to discover funny bugs in your FUSE software this way, so buckle up
someone has also tested geesefs in combination with gocryptfs with surprisingly good results, getting 60 MiB/s upload speeds on a gbit line, but JuiceFS won with 80 MiB/s using its built-in encryption
you may improve performance by specifying larger values for --iobuf / --s-rd-sz / --s-wr-sz
hiding from google
tell search engines you don't wanna be indexed, either using the good old robots.txt or through copyparty settings:
--no-robotsadds HTTP (X-Robots-Tag) and HTML (<meta>) headers withnoindex, nofollowglobally- volflag
[...]:c,norobotsdoes the same thing for that single volume - volflag
[...]:c,robotsALLOWS search-engine crawling for that volume, even if--no-robotsis set globally
also, --force-js disables the plain HTML folder listing, making things harder to parse for search engines
themes
you can change the default theme with --theme 2, and add your own themes by modifying browser.css or providing your own css to --css-browser, then telling copyparty they exist by increasing --themes
the classname of the HTML tag is set according to the selected theme, which is used to set colors as css variables ++
- each theme generally has a dark theme (even numbers) and a light theme (odd numbers), showing in pairs
- the first theme (theme 0 and 1) is
html.a, second theme (2 and 3) ishtml.b - if a light theme is selected,
html.yis set, otherwisehtml.zis - so if the dark edition of the 2nd theme is selected, you use any of
html.b,html.z,html.bzto specify rules
see the top of ./copyparty/web/browser.css where the color variables are set, and there's layout-specific stuff near the bottom
if you want to change the fonts, see ./docs/rice/
complete examples
-
see running on windows for a fancy windows setup
- or use any of the examples below, just replace
python copyparty-sfx.pywithcopyparty.exeif you're using the exe edition
- or use any of the examples below, just replace
-
allow anyone to download or upload files into the current folder:
python copyparty-sfx.py-
enable searching and music indexing with
-e2dsa -e2ts -
start an FTP server on port 3921 with
--ftp 3921 -
announce it on your LAN with
-zso it appears in windows/Linux file managers
-
-
anyone can upload, but nobody can see any files (even the uploader):
python copyparty-sfx.py -e2dsa -v .::w-
block uploads if there's less than 4 GiB free disk space with
--df 4 -
show a popup on new uploads with
--xau bin/hooks/notify.py
-
-
anyone can upload, and receive "secret" links for each upload they do:
python copyparty-sfx.py -e2dsa -v .::wG:c,fk=8 -
anyone can browse (
r), onlykevin(passwordokgo) can upload/move/delete (A) files:
python copyparty-sfx.py -e2dsa -a kevin:okgo -v .::r:A,kevin -
read-only music server:
python copyparty-sfx.py -v /mnt/nas/music:/music:r -e2dsa -e2ts --no-robots --force-js --theme 2-
...with bpm and key scanning
-mtp .bpm=f,audio-bpm.py -mtp key=f,audio-key.py -
...with a read-write folder for
kevinwhose password isokgo
-a kevin:okgo -v /mnt/nas/inc:/inc:rw,kevin -
...with logging to disk
-lo log/cpp-%Y-%m%d-%H%M%S.txt.xz
-
listen on port 80 and 443
become a real webserver which people can access by just going to your IP or domain without specifying a port
if you're on windows, then you just need to add the commandline argument -p 80,443 and you're done! nice
if you're on macos, sorry, I don't know
if you're on Linux, you have the following 4 options:
-
option 1: set up a reverse-proxy -- this one makes a lot of sense if you're running on a proper headless server, because that way you get real HTTPS too
-
option 2: NAT to port 3923 -- this is cumbersome since you'll need to do it every time you reboot, and the exact command may depend on your linux distribution:
iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-port 3923 iptables -t nat -A PREROUTING -p tcp --dport 443 -j REDIRECT --to-port 3923 -
option 3: disable the security policy which prevents the use of 80 and 443; this is probably fine:
setcap CAP_NET_BIND_SERVICE=+eip $(realpath $(which python)) python copyparty-sfx.py -p 80,443 -
option 4: run copyparty as root (please don't)
reverse-proxy
running copyparty next to other websites hosted on an existing webserver such as nginx, caddy, or apache
you can either:
- give copyparty its own domain or subdomain (recommended)
- or do location-based proxying, using
--rp-loc=/stuffto tell copyparty where it is mounted -- has a slight performance cost and higher chance of bugs- if copyparty says
incorrect --rp-loc or webserver config; expected vpath starting with [...]it's likely because the webserver is stripping away the proxy location from the request URLs -- see theProxyPassin the apache example below
- if copyparty says
when running behind a reverse-proxy (this includes services like cloudflare), it is important to configure real-ip correctly, as many features rely on knowing the client's IP. Look out for red and yellow log messages which explain how to do this. But basically, set --xff-hdr to the name of the http header to read the IP from (usually x-forwarded-for, but cloudflare uses cf-connecting-ip), and then --xff-src to the IP of the reverse-proxy so copyparty will trust the xff-hdr. Note that --rp-loc in particular will not work at all unless you do this
some reverse proxies (such as Caddy) can automatically obtain a valid https/tls certificate for you, and some support HTTP/2 and QUIC which could be a nice speed boost, depending on a lot of factors
- warning: nginx-QUIC (HTTP/3) is still experimental and can make uploads much slower, so HTTP/1.1 is recommended for now
- depending on server/client, HTTP/1.1 can also be 5x faster than HTTP/2
for improved security (and a 10% performance boost) consider listening on a unix-socket with -i unix:770:www:/tmp/party.sock (permission 770 means only members of group www can access it)
example webserver configs:
- nginx config -- entire domain/subdomain
- apache2 config -- location-based
real-ip
teaching copyparty how to see client IPs when running behind a reverse-proxy, or a WAF, or another protection service such as cloudflare
if you (and maybe everybody else) keep getting a message that says thank you for playing, then you've gotten banned for malicious traffic. This ban applies to the IP address that copyparty thinks identifies the shady client -- so, depending on your setup, you might have to tell copyparty where to find the correct IP
for most common setups, there should be a helpful message in the server-log explaining what to do, but see docs/xff.md if you want to learn more, including a quick hack to just make it work (which is not recommended, but hey...)
prometheus
metrics/stats can be enabled at URL /.cpr/metrics for grafana / prometheus / etc (openmetrics 1.0.0)
must be enabled with --stats since it reduces startup time a tiny bit, and you probably want -e2dsa too
the endpoint is only accessible by admin accounts, meaning the a in rwmda in the following example commandline: python3 -m copyparty -a ed:wark -v /mnt/nas::rwmda,ed --stats -e2dsa
follow a guide for setting up node_exporter except have it read from copyparty instead; example /etc/prometheus/prometheus.yml below
scrape_configs:
- job_name: copyparty
metrics_path: /.cpr/metrics
basic_auth:
password: wark
static_configs:
- targets: ['192.168.123.1:3923']
currently the following metrics are available,
cpp_uptime_secondstime since last copyparty restartcpp_boot_unixtime_secondssame but as an absolute timestampcpp_active_dlnumber of active downloadscpp_http_connsnumber of open http(s) connectionscpp_http_reqsnumber of http(s) requests handledcpp_sus_reqsnumber of 403/422/malicious requestscpp_active_bansnumber of currently banned IPscpp_total_bansnumber of IPs banned since last restart
these are available unless --nos-vst is specified:
cpp_db_idle_secondstime since last database activity (upload/rename/delete)cpp_db_act_secondssame but as an absolute timestampcpp_idle_volsnumber of volumes which are idle / readycpp_busy_volsnumber of volumes which are busy / indexingcpp_offline_volsnumber of volumes which are offline / unavailablecpp_hashing_filesnumber of files queued for hashing / indexingcpp_tagq_filesnumber of files queued for metadata scanningcpp_mtpq_filesnumber of files queued for plugin-based analysis
and these are available per-volume only:
cpp_disk_size_bytestotal HDD sizecpp_disk_free_bytesfree HDD space
and these are per-volume and total:
cpp_vol_bytessize of all files in volumecpp_vol_filesnumber of filescpp_dupe_bytesdisk space presumably saved by deduplicationcpp_dupe_filesnumber of dupe filescpp_unf_bytescurrently unfinished / incoming uploads
some of the metrics have additional requirements to function correctly,
cpp_vol_*requires either thee2dsvolflag or-e2dsaglobal-option
the following options are available to disable some of the metrics:
--nos-hdddisablescpp_disk_*which can prevent spinning up HDDs--nos-voldisablescpp_vol_*which reduces server startup time--nos-vstdisables volume state, reducing the worst-case prometheus query time by 0.5 sec--nos-dupdisablescpp_dupe_*which reduces the server load caused by prometheus queries--nos-unfdisablescpp_unf_*for no particular purpose
note: the following metrics are counted incorrectly if multiprocessing is enabled with -j: cpp_http_conns, cpp_http_reqs, cpp_sus_reqs, cpp_active_bans, cpp_total_bans
other extremely specific features
you'll never find a use for these:
custom mimetypes
change the association of a file extension
using commandline args, you can do something like --mime gif=image/jif and --mime ts=text/x.typescript (can be specified multiple times)
in a config-file, this is the same as:
[global]
mime: gif=image/jif
mime: ts=text/x.typescript
run copyparty with --mimes to list all the default mappings
feature chickenbits
buggy feature? rip it out by setting any of the following environment variables to disable its associated bell or whistle,
| env-var | what it does |
|---|---|
PRTY_NO_IFADDR | disable ip/nic discovery by poking into your OS with ctypes |
PRTY_NO_IPV6 | disable some ipv6 support (should not be necessary since windows 2000) |
PRTY_NO_LZMA | disable streaming xz compression of incoming uploads |
PRTY_NO_MP | disable all use of the python multiprocessing module (actual multithreading, cpu-count for parsers/thumbnailers) |
PRTY_NO_SQLITE | disable all database-related functionality (file indexing, metadata indexing, most file deduplication logic) |
PRTY_NO_TLS | disable native HTTPS support; if you still want to accept HTTPS connections then TLS must now be terminated by a reverse-proxy |
PRTY_NO_TPOKE | disable systemd-tmpfilesd avoider |
example: PRTY_NO_IFADDR=1 python3 copyparty-sfx.py
packages
the party might be closer than you think
if your distro/OS is not mentioned below, there might be some hints in the «on servers» section
arch package
now available on aur maintained by @icxes
it comes with a systemd service and expects to find one or more config files in /etc/copyparty.d/
fedora package
does not exist yet; using the copr-pypi builds is NOT recommended because updates can be delayed by several months
nix package
nix profile install github:9001/copyparty
requires a flake-enabled installation of nix
some recommended dependencies are enabled by default; override the package if you want to add/remove some features/deps
ffmpeg-full was chosen over ffmpeg-headless mainly because we need withWebp (and withOpenmpt is also nice) and being able to use a cached build felt more important than optimizing for size at the time -- PRs welcome if you disagree 👍
nixos module
for this setup, you will need a flake-enabled installation of NixOS.
{
# add copyparty flake to your inputs
inputs.copyparty.url = "github:9001/copyparty";
# ensure that copyparty is an allowed argument to the outputs function
outputs = { self, nixpkgs, copyparty }: {
nixosConfigurations.yourHostName = nixpkgs.lib.nixosSystem {
modules = [
# load the copyparty NixOS module
copyparty.nixosModules.default
({ pkgs, ... }: {
# add the copyparty overlay to expose the package to the module
nixpkgs.overlays = [ copyparty.overlays.default ];
# (optional) install the package globally
environment.systemPackages = [ pkgs.copyparty ];
# configure the copyparty module
services.copyparty.enable = true;
})
];
};
};
}
copyparty on NixOS is configured via services.copyparty options, for example:
services.copyparty = {
enable = true;
# directly maps to values in the [global] section of the copyparty config.
# see `copyparty --help` for available options
settings = {
i = "0.0.0.0";
# use lists to set multiple values
p = [ 3210 3211 ];
# use booleans to set binary flags
no-reload = true;
# using 'false' will do nothing and omit the value when generating a config
ignored-flag = false;
};
# create users
accounts = {
# specify the account name as the key
ed = {
# provide the path to a file containing the password, keeping it out of /nix/store
# must be readable by the copyparty service user
passwordFile = "/run/keys/copyparty/ed_password";
};
# or do both in one go
k.passwordFile = "/run/keys/copyparty/k_password";
};
# create a volume
volumes = {
# create a volume at "/" (the webroot), which will
"/" = {
# share the contents of "/srv/copyparty"
path = "/srv/copyparty";
# see `copyparty --help-accounts` for available options
access = {
# everyone gets read-access, but
r = "*";
# users "ed" and "k" get read-write
rw = [ "ed" "k" ];
};
# see `copyparty --help-flags` for available options
flags = {
# "fk" enables filekeys (necessary for upget permission) (4 chars long)
fk = 4;
# scan for new files every 60sec
scan = 60;
# volflag "e2d" enables the uploads database
e2d = true;
# "d2t" disables multimedia parsers (in case the uploads are malicious)
d2t = true;
# skips hashing file contents if path matches *.iso
nohash = "\.iso$";
};
};
};
# you may increase the open file limit for the process
openFilesLimit = 8192;
};
the passwordFile at /run/keys/copyparty/ could for example be generated by agenix, or you could just dump it in the nix store instead if that's acceptable
browser support
TLDR: yes

ie = internet-explorer, ff = firefox, c = chrome, iOS = iPhone/iPad, Andr = Android
| feature | ie6 | ie9 | ie10 | ie11 | ff 52 | c 49 | iOS | Andr |
|---|---|---|---|---|---|---|---|---|
| browse files | yep | yep | yep | yep | yep | yep | yep | yep |
| thumbnail view | - | yep | yep | yep | yep | yep | yep | yep |
| basic uploader | yep | yep | yep | yep | yep | yep | yep | yep |
| up2k | - | - | *1 | *1 | yep | yep | yep | yep |
| make directory | yep | yep | yep | yep | yep | yep | yep | yep |
| send message | yep | yep | yep | yep | yep | yep | yep | yep |
| set sort order | - | yep | yep | yep | yep | yep | yep | yep |
| zip selection | - | yep | yep | yep | yep | yep | yep | yep |
| file rename | - | yep | yep | yep | yep | yep | yep | yep |
| file cut/paste | - | yep | yep | yep | yep | yep | yep | yep |
| navpane | - | yep | yep | yep | yep | yep | yep | yep |
| image viewer | - | yep | yep | yep | yep | yep | yep | yep |
| video player | - | yep | yep | yep | yep | yep | yep | yep |
| markdown editor | - | - | *2 | *2 | yep | yep | yep | yep |
| markdown viewer | - | *2 | *2 | *2 | yep | yep | yep | yep |
| play mp3/m4a | - | yep | yep | yep | yep | yep | yep | yep |
| play ogg/opus | - | - | - | - | yep | yep | *3 | yep |
| = feature = | ie6 | ie9 | ie10 | ie11 | ff 52 | c 49 | iOS | Andr |
- internet explorer 6 through 8 behave the same
- firefox 52 and chrome 49 are the final winxp versions
*1yes, but extremely slow (ie10:1 MiB/s, ie11:270 KiB/s)*2only able to do plaintext documents (no markdown rendering)*3iOS 11 and newer, opus only, and requires FFmpeg on the server
quick summary of more eccentric web-browsers trying to view a directory index:
| browser | will it blend |
|---|---|
| links (2.21/macports) | can browse, login, upload/mkdir/msg |
| lynx (2.8.9/macports) | can browse, login, upload/mkdir/msg |
| w3m (0.5.3/macports) | can browse, login, upload at 100kB/s, mkdir/msg |
| netsurf (3.10/arch) | is basically ie6 with much better css (javascript has almost no effect) |
| opera (11.60/winxp) | OK: thumbnails, image-viewer, zip-selection, rename/cut/paste. NG: up2k, navpane, markdown, audio |
| ie4 and netscape 4.0 | can browse, upload with ?b=u, auth with &pw=wark |
| ncsa mosaic 2.7 | does not get a pass, pic1 - pic2 |
| SerenityOS (7e98457) | hits a page fault, works with ?b=u, file upload not-impl |
| nintendo 3ds | can browse, upload, view thumbnails (thx bnjmn) |
client examples
interact with copyparty using non-browser clients
-
javascript: dump some state into a file (two separate examples)
await fetch('//127.0.0.1:3923/', {method:"PUT", body: JSON.stringify(foo)});var xhr = new XMLHttpRequest(); xhr.open('POST', '//127.0.0.1:3923/msgs?raw'); xhr.send('foo');
-
curl/wget: upload some files (post=file, chunk=stdin)
post(){ curl -F f=@"$1" http://127.0.0.1:3923/?pw=wark;}
post movie.mkv(gives HTML in return)post(){ curl -F f=@"$1" 'http://127.0.0.1:3923/?want=url&pw=wark';}
post movie.mkv(gives hotlink in return)post(){ curl -H pw:wark -H rand:8 -T "$1" http://127.0.0.1:3923/;}
post movie.mkv(randomized filename)post(){ wget --header='pw: wark' --post-file="$1" -O- http://127.0.0.1:3923/?raw;}
post movie.mkvchunk(){ curl -H pw:wark -T- http://127.0.0.1:3923/;}
chunk <movie.mkv
-
bash: when curl and wget is not available or too boring
(printf 'PUT /junk?pw=wark HTTP/1.1\r\n\r\n'; cat movie.mkv) | nc 127.0.0.1 3923(printf 'PUT / HTTP/1.1\r\n\r\n'; cat movie.mkv) >/dev/tcp/127.0.0.1/3923
-
python: u2c.py is a command-line up2k client (webm)
- file uploads, file-search, folder sync, autoresume of aborted/broken uploads
- can be downloaded from copyparty: controlpanel -> connect -> u2c.py
- see ./bin/README.md#u2cpy
-
FUSE: mount a copyparty server as a local filesystem
- cross-platform python client available in ./bin/
- able to mount nginx and iis directory listings too, not just copyparty
- can be downloaded from copyparty: controlpanel -> connect -> partyfuse.py
- rclone as client can give ~5x performance, see ./docs/rclone.md
-
sharex (screenshot utility): see ./contrib/sharex.sxcu
- and for screenshots on linux, see ./contrib/flameshot.sh
-
contextlet (web browser integration); see contrib contextlet
-
igloo irc: Method:
postHost:https://you.com/up/?want=url&pw=hunter2Multipart:yesFile parameter:f
copyparty returns a truncated sha512sum of your PUT/POST as base64; you can generate the same checksum locally to verify uploads:
b512(){ printf "$((sha512sum||shasum -a512)|sed -E 's/ .*//;s/(..)/\\x\1/g')"|base64|tr '+/' '-_'|head -c44;}
b512 <movie.mkv
you can provide passwords using header PW: hunter2, cookie cppwd=hunter2, url-param ?pw=hunter2, or with basic-authentication (either as the username or password)
NOTE: curl will not send the original filename if you use -T combined with url-params! Also, make sure to always leave a trailing slash in URLs unless you want to override the filename
folder sync
sync folders to/from copyparty
the commandline uploader u2c.py with --dr is the best way to sync a folder to copyparty; verifies checksums and does files in parallel, and deletes unexpected files on the server after upload has finished which makes file-renames really cheap (it'll rename serverside and skip uploading)
alternatively there is rclone which allows for bidirectional sync and is way more flexible (stream files straight from sftp/s3/gcs to copyparty, ...), although there is no integrity check and it won't work with files over 100 MiB if copyparty is behind cloudflare
- starting from rclone v1.63, rclone is faster than u2c.py on low-latency connections
mount as drive
a remote copyparty server as a local filesystem; go to the control-panel and click connect to see a list of commands to do that
alternatively, some alternatives roughly sorted by speed (unreproducible benchmark), best first:
- rclone-webdav (25s), read/WRITE (rclone v1.63 or later)
- rclone-http (26s), read-only
- partyfuse.py (26s), read-only
- rclone-ftp (47s), read/WRITE
- davfs2 (103s), read/WRITE
- win10-webdav (138s), read/WRITE
- win10-smb2 (387s), read/WRITE
most clients will fail to mount the root of a copyparty server unless there is a root volume (so you get the admin-panel instead of a browser when accessing it) -- in that case, mount a specific volume instead
if you have volumes that are accessible without a password, then some webdav clients (such as davfs2) require the global-option --dav-auth to access any password-protected areas
android app
upload to copyparty with one tap
<a href="https://f-droid.org/packages/me.ocv.partyup/"><img src="https://ocv.me/fdroid.png" alt="Get it on F-Droid" height="50" /> '' <img src="https://img.shields.io/f-droid/v/me.ocv.partyup.svg" alt="f-droid version info" /></a> '' <a href="https://github.com/9001/party-up"><img src="https://img.shields.io/github/release/9001/party-up.svg?logo=github" alt="github version info" /></a>
the app is NOT the full copyparty server! just a basic upload client, nothing fancy yet
if you want to run the copyparty server on your android device, see install on android
iOS shortcuts
there is no iPhone app, but the following shortcuts are almost as good:
- upload to copyparty (offline) (png) based on the original by Daedren (thx!)
- can strip exif, upload files, pics, vids, links, clipboard
- can download links and rehost the target file on copyparty (see first comment inside the shortcut)
- pics become lowres if you share from gallery to shortcut, so better to launch the shortcut and pick stuff from there
performance
defaults are usually fine - expect 8 GiB/s download, 1 GiB/s upload
below are some tweaks roughly ordered by usefulness:
- disabling HTTP/2 and HTTP/3 can make uploads 5x faster, depending on server/client software
-qdisables logging and can help a bunch, even when combined with-loto redirect logs to file--histpointing to a fast location (ssd) will make directory listings and searches faster when-e2dor-e2tis set- and also makes thumbnails load faster, regardless of e2d/e2t
--dedupenables deduplication and thus avoids writing to the HDD if someone uploads a dupe--safe-dedup 1makes deduplication much faster during upload by skipping verification of file contents; safe if there is no other software editing/moving the files in the volumes--no-dirszshows the size of folder inodes instead of the total size of the contents, giving about 30% faster folder listings--no-hash .when indexing a network-disk if you don't care about the actual filehashes and only want the names/tags searchable- if your volumes are on a network-disk such as NFS / SMB / s3, specifying larger values for
--iobufand/or--s-rd-szand/or--s-wr-szmay help; try setting all of them to524288or1048576or4194304 --no-htp --hash-mt=0 --mtag-mt=1 --th-mt=1minimizes the number of threads; can help in some eccentric environments (like the vscode debugger)-j0enables multiprocessing (actual multithreading), can reduce latency to20+80/numCorespercent and generally improve performance in cpu-intensive workloads, for example:- lots of connections (many users or heavy clients)
- simultaneous downloads and uploads saturating a 20gbps connection
- if
-e2dis enabled,-j2gives 4x performance for directory listings;-j4gives 16x
- using pypy instead of cpython can be 70% faster for some workloads, but slower for many others
- and pypy can sometimes crash on startup with
-j0(TODO make issue)
- and pypy can sometimes crash on startup with
client-side
when uploading files,
-
chrome is recommended (unfortunately), at least compared to firefox:
- up to 90% faster when hashing, especially on SSDs
- up to 40% faster when uploading over extremely fast internets
- but u2c.py can be 40% faster than chrome again
-
if you're cpu-bottlenecked, or the browser is maxing a cpu core:
- up to 30% faster uploads if you hide the upload status list by switching away from the
[🚀]up2k ui-tab (or closing it)- optionally you can switch to the lightweight potato ui by clicking the
[🥔] - switching to another browser-tab also works, the favicon will update every 10 seconds in that case
- optionally you can switch to the lightweight potato ui by clicking the
- unlikely to be a problem, but can happen when uploading many small files, or your internet is too fast, or PC too slow
- up to 30% faster uploads if you hide the upload status list by switching away from the
security
there is a discord server with an @everyone for all important updates (at the lack of better ideas)
some notes on hardening
- set
--rproxy 0if your copyparty is directly facing the internet (not through a reverse-proxy)- cors doesn't work right otherwise
- if you allow anonymous uploads or otherwise don't trust the contents of a volume, you can prevent XSS with volflag
nohtml- this returns html documents as plaintext, and also disables markdown rendering
- when running behind a reverse-proxy, listen on a unix-socket for tighter access control (and more performance); see reverse-proxy or
--help-bind
safety profiles:
-
option
-sis a shortcut to set the following options:--no-thumbdisables thumbnails and audio transcoding to stop copyparty from runningFFmpeg/Pillow/VIPSon uploaded files, which is a good idea if anonymous upload is enabled--no-mtag-ffusesmutagento grab music tags instead ofFFmpeg, which is safer and faster but less accurate--dotparthides uploads from directory listings while they're still incoming--no-robotsand--force-jsmakes life harder for crawlers, see hiding from google
-
option
-ssis a shortcut for the above plus:--unpost 0,--no-del,--no-mvdisables all move/delete support--hardlinkcreates hardlinks instead of symlinks when deduplicating uploads, which is less maintenance- however note if you edit one file it will also affect the other copies
--vague-403returns a "404 not found" instead of "401 unauthorized" which is a common enterprise meme-nihremoves the server hostname from directory listings
-
option
-sssis a shortcut for the above plus:--no-davdisables webdav support--no-loguesand--no-readmedisables support for readme's and prologues / epilogues in directory listings, which otherwise lets people upload arbitrary (but sandboxed)<script>tags-lo cpp-%Y-%m%d-%H%M%S.txt.xzenables logging to disk-ls **,*,ln,p,rdoes a scan on startup for any dangerous symlinks
other misc notes:
- you can disable directory listings by giving permission
ginstead ofr, only accepting direct URLs to files- you may want filekeys to prevent filename bruteforcing
- permission
hinstead ofrmakes copyparty behave like a traditional webserver with directory listing/index disabled, returning index.html instead- compatibility with filekeys: index.html itself can be retrieved without the correct filekey, but all other files are protected
gotchas
behavior that might be unexpected
- users without read-access to a folder can still see the
.prologue.html/.epilogue.html/PREADME.md/README.mdcontents, for the purpose of showing a description on how to use the uploader for example - users can submit
<script>s which autorun (in a sandbox) for other visitors in a few ways;- uploading a
README.md-- avoid with--no-readme - renaming
some.htmlto.epilogue.html-- avoid with either--no-loguesor--no-dot-ren - the directory-listing embed is sandboxed (so any malicious scripts can't do any damage) but the markdown editor is not 100% safe, see below
- uploading a
- markdown documents can contain html and
<script>s; attempts are made to prevent scripts from executing (unless-empis specified) but this is not 100% bulletproof, so setting thenohtmlvolflag is still the safest choice- or eliminate the problem entirely by only giving write-access to trustworthy people :^)
cors
cross-site request config
by default, except for GET and HEAD operations, all requests must either:
- not contain an
Originheader at all - or have an
Originmatching the server domain - or the header
PWwith your password as value
cors can be configured with --acao and --acam, or the protections entirely disabled with --allow-csrf
filekeys
prevent filename bruteforcing
volflag fk generates filekeys (per-file accesskeys) for all files; users which have full read-access (permission r) will then see URLs with the correct filekey ?k=... appended to the end, and g users must provide that URL including the correct key to avoid a 404
by default, filekeys are generated based on salt (--fk-salt) + filesystem-path + file-size + inode (if not windows); add volflag fka to generate slightly weaker filekeys which will not be invalidated if the file is edited (only salt + path)
permissions wG (write + upget) lets users upload files and receive their own filekeys, still without being able to see other uploads
dirkeys
share specific folders in a volume without giving away full read-access to the rest -- the visitor only needs the g (get) permission to view the link
volflag dk generates dirkeys (per-directory accesskeys) for all folders, granting read-access to that folder; by default only that folder itself, no subfolders
volflag dky disables the actual key-check, meaning anyone can see the contents of a folder where they have g access, but not its subdirectories
dk+dkygives the same behavior as if all users withgaccess have full read-access, but subfolders are hidden files (as if their names start with a dot), sodkyis an alternative to renaming all the folders for that purpose, maybe just for some users
volflag dks lets people enter subfolders as well, and also enables download-as-zip/tar
if you enable dirkeys, it is probably a good idea to enable filekeys too, otherwise it will be impossible to hotlink files from a folder which was accessed using a dirkey
dirkeys are generated based on another salt (--dk-salt) + filesystem-path and have a few limitations:
- the key does not change if the contents of the folder is modified
- if you need a new dirkey, either change the salt or rename the folder
- linking to a textfile (so it opens in the textfile viewer) is not possible if recipient doesn't have read-access
password hashing
you can hash passwords before putting them into config files / providing them as arguments; see --help-pwhash for all the details
--ah-alg argon2 enables it, and if you have any plaintext passwords then it'll print the hashed versions on startup so you can replace them
optionally also specify --ah-cli to enter an interactive mode where it will hash passwords without ever writing the plaintext ones to disk
the default configs take about 0.4 sec and 256 MiB RAM to process a new password on a decent laptop
https
both HTTP and HTTPS are accepted by default, but letting a reverse proxy handle the https/tls/ssl would be better (probably more secure by default)
copyparty doesn't speak HTTP/2 or QUIC, so using a reverse proxy would solve that as well -- but note that HTTP/1 is usually faster than both HTTP/2 and HTTP/3
if cfssl is installed, copyparty will automatically create a CA and server-cert on startup
- the certs are written to
--crt-dirfor distribution, see--helpfor the other--crtoptions - this will be a self-signed certificate so you must install your
ca.peminto all your browsers/devices - if you want to avoid the hassle of distributing certs manually, please consider using a reverse proxy
recovering from crashes
client crashes
firefox wsod
firefox 87 can crash during uploads -- the entire browser goes, including all other browser tabs, everything turns white
however you can hit F12 in the up2k tab and use the devtools to see how far you got in the uploads:
-
get a complete list of all uploads, organized by status (ok / no-good / busy / queued):
var tabs = { ok:[], ng:[], bz:[], q:[] }; for (var a of up2k.ui.tab) tabs[a.in].push(a); tabs -
list of filenames which failed:
var ng = []; for (var a of up2k.ui.tab) if (a.in != 'ok') ng.push(a.hn.split('<a href=\"').slice(-1)[0].split('\">')[0]); ng -
send the list of filenames to copyparty for safekeeping:
await fetch('/inc', {method:'PUT', body:JSON.stringify(ng,null,1)})
HTTP API
see devnotes
dependencies
mandatory deps:
jinja2(is built into the SFX)
optional dependencies
install these to enable bonus features
enable hashed passwords in config: argon2-cffi
enable ftp-server:
- for just plaintext FTP,
pyftpdlib(is built into the SFX) - with TLS encryption,
pyftpdlib pyopenssl
enable music tags:
- either
mutagen(fast, pure-python, skips a few tags, makes copyparty GPL? idk) - or
ffprobe(20x slower, more accurate, possibly dangerous depending on your distro and users)
enable thumbnails of...
- images:
Pillowand/orpyvipsand/orffmpeg(requires py2.7 or py3.5+) - videos/audio:
ffmpegandffprobesomewhere in$PATH - HEIF pictures:
pyvipsorffmpegorpyheif-pillow-opener(requires Linux or a C compiler) - AVIF pictures:
pyvipsorffmpegorpillow-avif-plugin - JPEG XL pictures:
pyvipsorffmpeg
enable smb support (not recommended):
impacket==0.12.0
pyvips gives higher quality thumbnails than Pillow and is 320% faster, using 270% more ram: sudo apt install libvips42 && python3 -m pip install --user -U pyvips
dependency chickenbits
prevent loading an optional dependency , for example if:
- you have an incompatible version installed and it causes problems
- you just don't want copyparty to use it, maybe to save ram
set any of the following environment variables to disable its associated optional feature,
| env-var | what it does |
|---|---|
PRTY_NO_ARGON2 | disable argon2-cffi password hashing |
PRTY_NO_CFSSL | never attempt to generate self-signed certificates using cfssl |
PRTY_NO_FFMPEG | audio transcoding goes byebye, thumbnailing must be handled by Pillow/libvips |
PRTY_NO_FFPROBE | audio transcoding goes byebye, thumbnailing must be handled by Pillow/libvips, metadata-scanning must be handled by mutagen |
PRTY_NO_MUTAGEN | do not use mutagen for reading metadata from media files; will fallback to ffprobe |
PRTY_NO_PIL | disable all Pillow-based thumbnail support; will fallback to libvips or ffmpeg |
PRTY_NO_PILF | disable Pillow ImageFont text rendering, used for folder thumbnails |
PRTY_NO_PIL_AVIF | disable 3rd-party Pillow plugin for AVIF support |
PRTY_NO_PIL_HEIF | disable 3rd-party Pillow plugin for HEIF support |
PRTY_NO_PIL_WEBP | disable use of native webp support in Pillow |
PRTY_NO_PSUTIL | do not use psutil for reaping stuck hooks and plugins on Windows |
PRTY_NO_VIPS | disable all libvips-based thumbnail support; will fallback to Pillow or ffmpeg |
example: PRTY_NO_PIL=1 python3 copyparty-sfx.py
PRTY_NO_PILsaves ramPRTY_NO_VIPSsaves ram and startup time- python2.7 on windows:
PRTY_NO_FFMPEG+PRTY_NO_FFPROBEsaves startup time
optional gpl stuff
some bundled tools have copyleft dependencies, see ./bin/#mtag
these are standalone programs and will never be imported / evaluated by copyparty, and must be enabled through -mtp configs
sfx
the self-contained "binary" (recommended!) copyparty-sfx.py will unpack itself and run copyparty, assuming you have python installed of course
you can reduce the sfx size by repacking it; see ./docs/devnotes.md#sfx-repack
copyparty.exe
download copyparty.exe (win8+) or copyparty32.exe (win7+)

can be convenient on machines where installing python is problematic, however is not recommended -- if possible, please use copyparty-sfx.py instead
-
copyparty.exe runs on win8 or newer, was compiled on win10, does thumbnails + media tags, and is currently safe to use, but any future python/expat/pillow CVEs can only be remedied by downloading a newer version of the exe
- on win8 it needs vc redist 2015, on win10 it just works
- some antivirus may freak out (false-positive), possibly Avast, AVG, and McAfee
-
dangerous: copyparty32.exe is compatible with windows7, which means it uses an ancient copy of python (3.7.9) which cannot be upgraded and should never be exposed to the internet (LAN is fine)
-
dangerous and deprecated: copyparty-winpe64.exe lets you run copyparty in WinPE and is otherwise completely useless
meanwhile copyparty-sfx.py instead relies on your system python which gives better performance and will stay safe as long as you keep your python install up-to-date
then again, if you are already into downloading shady binaries from the internet, you may also want my minimal builds of ffmpeg and ffprobe which enables copyparty to extract multimedia-info, do audio-transcoding, and thumbnails/spectrograms/waveforms, however it's much better to instead grab a recent official build every once ina while if you can afford the size
zipapp
another emergency alternative, copyparty.pyz has less features, is slow, requires python 3.7 or newer, worse compression, and more importantly is unable to benefit from more recent versions of jinja2 and such (which makes it less secure)... lots of drawbacks with this one really -- but it does not unpack any temporary files to disk, so it may just work if the regular sfx fails to start because the computer is messed up in certain funky ways, so it's worth a shot if all else fails
run it by doubleclicking it, or try typing python copyparty.pyz in your terminal/console/commandline/telex if that fails
it is a python zipapp meaning it doesn't have to unpack its own python code anywhere to run, so if the filesystem is busted it has a better chance of getting somewhere
- but note that it currently still needs to extract the web-resources somewhere (they'll land in the default TEMP-folder of your OS)
install on android
install Termux + its companion app Termux:API (see ocv.me/termux) and then copy-paste this into Termux (long-tap) all at once:
yes | pkg upgrade && termux-setup-storage && yes | pkg install python termux-api && python -m ensurepip && python -m pip install --user -U copyparty && { grep -qE 'PATH=.*\.local/bin' ~/.bashrc 2>/dev/null || { echo 'PATH="$HOME/.local/bin:$PATH"' >> ~/.bashrc && . ~/.bashrc; }; }
echo $?
after the initial setup, you can launch copyparty at any time by running copyparty anywhere in Termux -- and if you run it with --qr you'll get a neat qr-code pointing to your external ip
if you want thumbnails (photos+videos) and you're okay with spending another 132 MiB of storage, pkg install ffmpeg && python3 -m pip install --user -U pillow
- or if you want to use
vipsfor photo-thumbs instead,pkg install libvips && python -m pip install --user -U wheel && python -m pip install --user -U pyvips && (cd /data/data/com.termux/files/usr/lib/; ln -s libgobject-2.0.so{,.0}; ln -s libvips.so{,.42})
reporting bugs
ideas for context to include, and where to submit them
please get in touch using any of the following URLs:
- https://github.com/9001/copyparty/ (primary)
- https://gitlab.com/9001/copyparty/ (mirror)
- https://codeberg.org/9001/copyparty (mirror)
in general, commandline arguments (and config file if any)
if something broke during an upload (replacing FILENAME with a part of the filename that broke):
journalctl -aS '48 hour ago' -u copyparty | grep -C10 FILENAME | tee bug.log
if there's a wall of base64 in the log (thread stacks) then please include that, especially if you run into something freezing up or getting stuck, for example OperationalError('database is locked') -- alternatively you can visit /?stack to see the stacks live, so http://127.0.0.1:3923/?stack for example
devnotes
for build instructions etc, see ./docs/devnotes.md
see ./docs/TODO.md for planned features / fixes / changes