Awesome
PoSh-R2PowerShell - Rapid Response (PoSH-R2)... For the incident responder in you!
PoSH-R2 is a set of Windows Management Instrumentation (WMI) scripts that investigators and forensic analysts can use to retrieve information from a compromised (or potentially compromised) Windows system. The scripts use WMI to pull this information from the operating system. Therefore, this script will need to be executed with a user that has the necessary privileges and authentication is done via a Network logon. Retreived data is written to CSVs and SQLite databases on the system running the script. <br> <br> In a single execution, PoSH-R2 will retrieve the following data from an individual machine or a group of systems: <br> <br> - Autorun entries <br> - Disk info <br> - Environment variables <br> - Event logs (50 lastest) <br> - Installed Software <br> - Logon sessions <br> - List of drivers <br> - List of mapped network drives <br> - List of running processes <br> - Logged in user <br> - Local groups <br> - Local user accounts <br> - Network configuration <br> - Network connections <br> - Patches <br> - Scheduled tasks with AT command <br> - Shares <br> - Services <br> - System Information <br>
Usage <br>
- Call upon the script from a PowerShell window with applicable rights for WMI and follow the prompts. <br>
- Data will be saved to a new directory called "PoSH_R2--Results" within the same directory from which this script was executed from. <br>
Additional Notes <br>
- This script will work with PowerShell version 2 and above
Screenshots <br>
<br>Running the script<br>
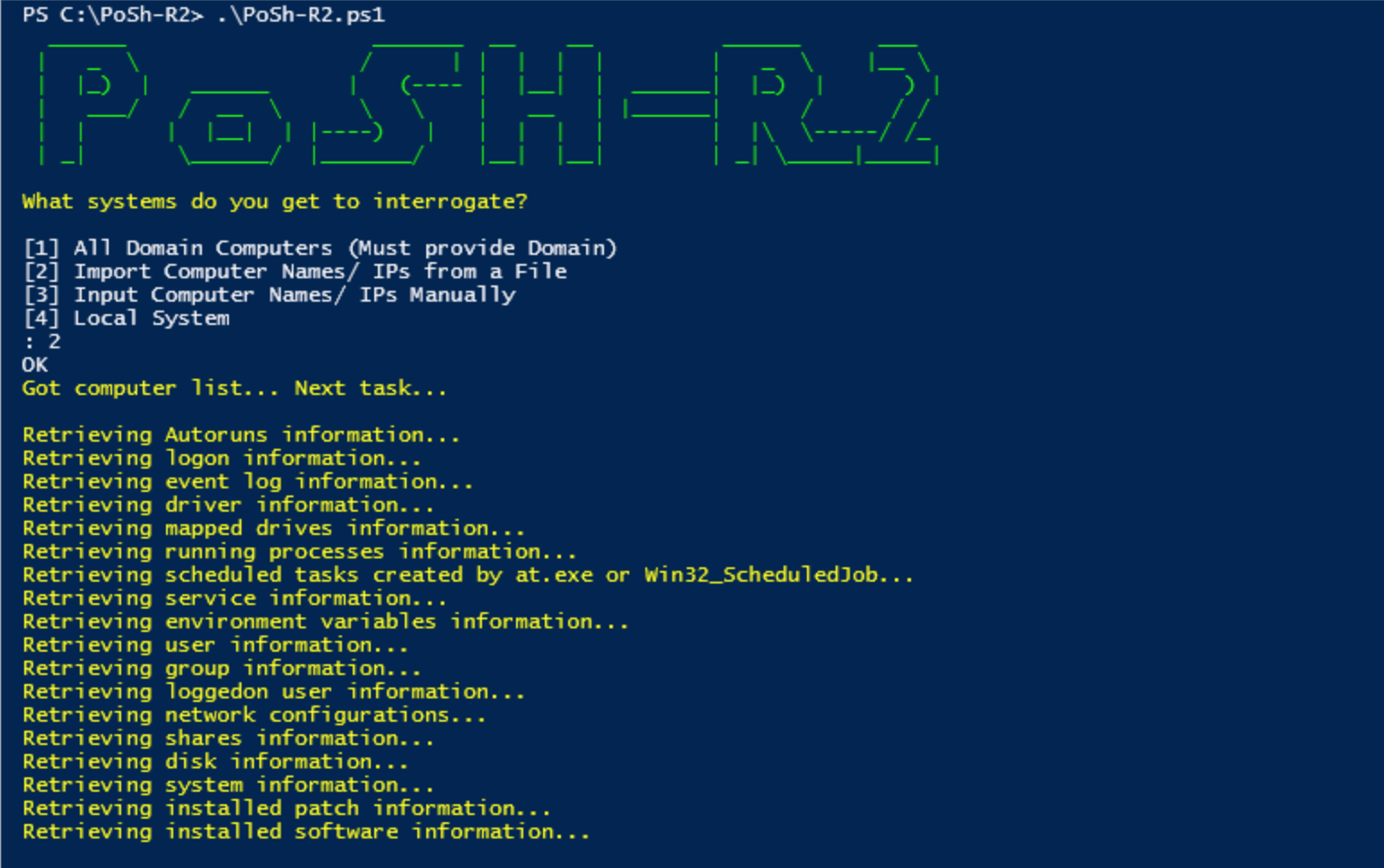 <br>
<br>
A listing of the results written to csv files<br>
<br>
<br>
A listing of the results written to csv files<br>
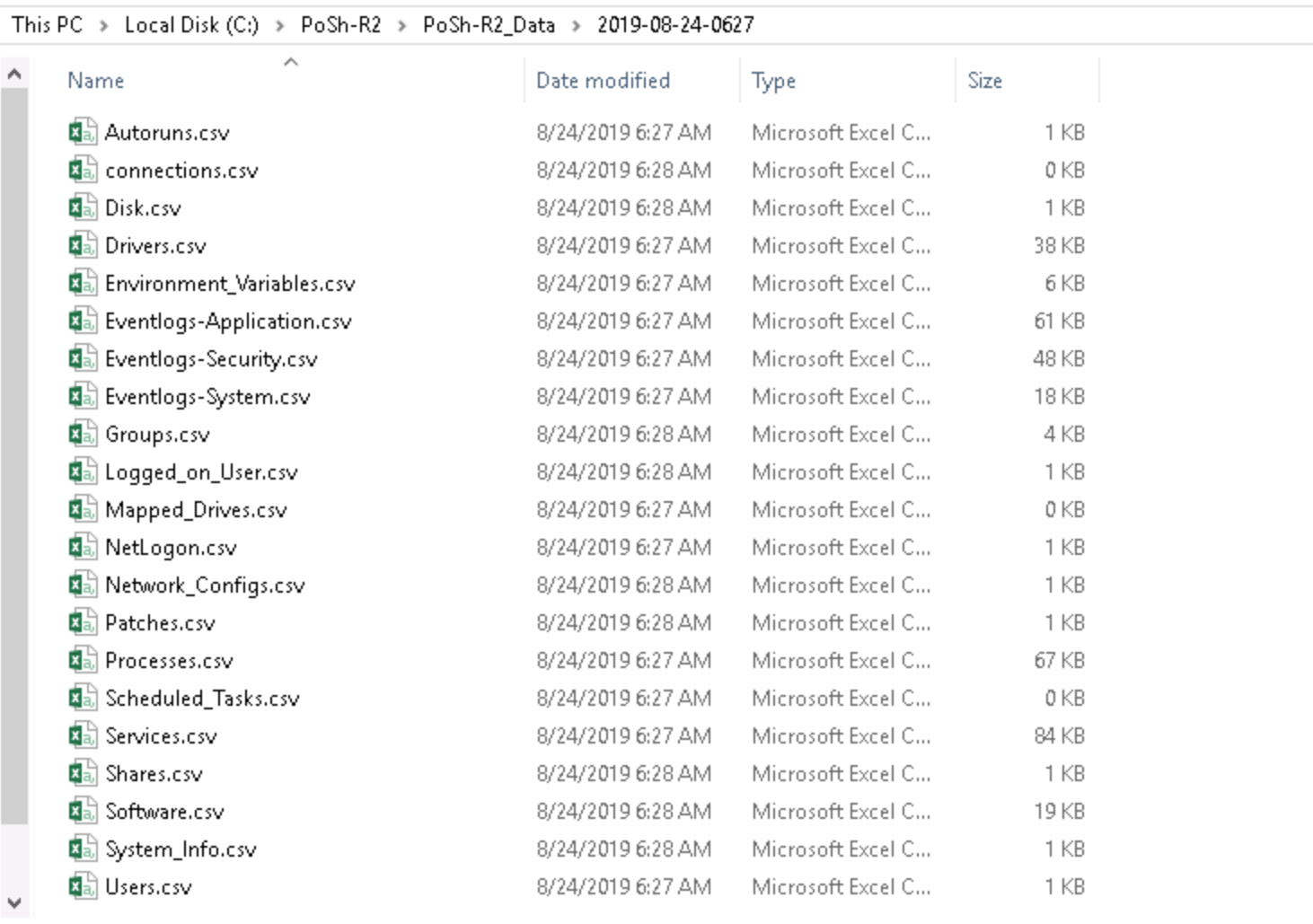 <br>
<br>
<br>
A listing of the databases<br>
<br>
<br>
<br>
A listing of the databases<br>
 <br>
<br>
<br>
Reading the data back into PowerShell using out-gridview (import-csv .<some_file.csv> | out-gridview)<br>
<br>
<br>
<br>
Reading the data back into PowerShell using out-gridview (import-csv .<some_file.csv> | out-gridview)<br>
 <br>
<br>
Filtering only on splunk.exe. From the screenshot, we see it is running on six systems<br>
<br>
<br>
Filtering only on splunk.exe. From the screenshot, we see it is running on six systems<br>