Awesome
Ada Security Library
Ada Security provides a security framework which allows applications to define and enforce security policies. This framework allows users to authenticate by using OpenID Authentication 2.0 as well as OAuth 2.0 protocol. It allows a web application to integrate easily with Yahoo!, Gitlab, Github, Facebook and Google+ authentication systems. The Ada05 library includes:
- An OpenID client authentication,
- An OAuth 2.0 client authentication,
- An OpenID Connect authentication framework,
- An OAuth 2.0 server authentication framework,
- A policy based security framework to protect the resources
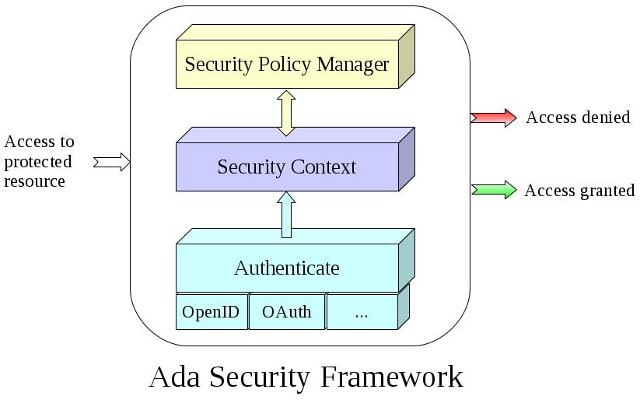
The Ada Security library is used by the Ada Web Application and the OpenAPI Ada library to provide authentication and access control to users within the web applications.
Version 1.5.1 - Aug 2024
- Cleanup build environment to drop configure
Using with Alire
If you are using Alire in your project, run the following command within your Alire project to use the library:
alr with security
Using without Alire
If you don't have Alire or want to build and install the library
on a specific place, run a setup command to configure the build as well as installation
directory.
For a detailed description on how you can configure, build and install the library
refer to the Installation guide.
Otherwise, you can easily configure and build the library with the steps described below.
The HAVE_ALIRE configuration allows you to disable the build with Alire:
make setup BUILD=debug PREFIX=/build/install HAVE_ALIRE=no
Since this build method does not verify that all dependencies are met, make sure that you
have already built and install the following components and they are available to gprbuild
through ADA_PROJECT_PATH if needed:
Then build, run the unit tests and install by using:
make
make test
make install
To use the installed libraries, make sure your ADA_PROJECT_PATH contains the directory
where you installed the libraries (configured by the PREFIX=<path> option in the setup phase).
The installed GNAT projects are the same as those used when using Alire.
Running the tests
The unit tests are built and executed with:
make test
Samples
The package provides a simple AWS server that illustrates the OpenID and OpenConnect authentication. Because OAuth2 relies exclusively on HTTPS, you must use an AWS server that has the SSL support. Build it as follows:
cd samples
alr build
Before launching the demo server, you must update the 'samples.properties' file and change the lines that contain PUT-HERE-YOUR-FACEBOOK-xxx with your client ID and client secrets. This change is required by the OAuth and OpenID Connect framework only. Then, run the server:
bin/auth_demo
and redirect your browser to:
http://localhost:8080/atlas/login.html
Documentation
The Ada Security sources as well as a wiki documentation is provided on:
Other Documentation
The OAuth literature is quite complete on the Internet and there are several good tutorials and documentation.
- Facebook Login
- Using OAuth 2.0 to Access Google APIs
- Yahoo OAuth 2.0 Guide
- Salesforce OAuth 2.0 Guide (this is a good guide if you want to learn)
References
- RFC 6749: The OAuth 2.0 Authorization Framework
- RFC 6750: The OAuth 2.0 Authorization Framework: Bearer Token Usage
- RFC 6819: OAuth 2.0 Threat Model and Security Considerations
- OpenID Connect Core 1.0







