Awesome
Jarelllama's Scam Blocklist
Blocklist for newly created scam and phishing domains automatically retrieved daily using Google Search API, automated detection, and other public sources.
The automated retrieval is done daily at 16:00 UTC.
This blocklist aims to be an alternative to blocking all newly registered domains (NRDs) seeing how many, but not all, NRDs are malicious. A variety of sources are integrated to detect new malicious domains within a short time span of their registration date.
Download
| Format | Syntax |
|---|---|
| Adblock Plus | ||scam.com^ |
| Wildcard Domains | scam.com |
Statistics
Total domains: 166148
Light version: 14951
New domains from each source: *
Today | Yesterday | Excluded | Source
29 | 62 | 50% | Emerging Threats phishing
201 | 332 | 18% | FakeWebshopListHUN
51 | 48 | 4% | Google Search
78 | 64 | 10% | Greek Tax Scam
913 | 945 | 8% | Jeroengui phishing feed
23 | 10 | 6% | Jeroengui scam feed
0 | 0 | 0% | Manual Entries
3458 | 4833 | 18% | PhishStats
1023 | 1432 | 0% | PhishStats (NRDs)
1194 | 1278 | 1% | Regex Matching (NRDs)
16 | 14 | 10% | aa419.org
104 | 84 | 1% | dnstwist (NRDs)
218 | 232 | 31% | guntab.com
0 | 0 | 11% | scam.directory
5 | 5 | 32% | scamadviser.com
2 | 0 | 6% | stopgunscams.com
6292 | 7907 | 16% | All sources
* The new domain numbers reflect what was retrieved, not
what was added to the blocklist.
* The Excluded % is of domains not included in the
blocklist. Mostly dead, whitelisted, and parked domains.
<details> <summary>Domains over time (days)</summary>[!IMPORTANT] All data retrieved are publicly available and can be viewed from their respective sources.<br> Any data hidden behind account creation/commercial licenses is never used.
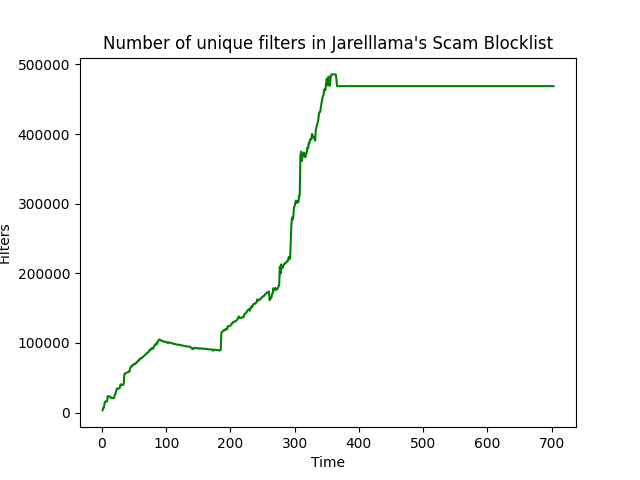
Courtesy of iam-py-test/blocklist_stats.
</details>Other blocklists
Light version
Targeted at list maintainers, a light version of the blocklist is available in the lists directory.
<details> <summary>Details about the light version</summary> <ul> <li>Intended for collated blocklists cautious about size</li> <li>Only includes sources whose domains can be filtered by date registered/reported</li> <li>Only includes domains retrieved/reported from February 2024 onwards, whereas the full list goes back further historically</li> <li>Note that dead and parked domains that become alive/unparked are not added back into the light version (due to limitations in the way these domains are recorded)</li> </ul> Sources excluded from the light version are marked in SOURCES.md. <br> <br> The full version should be used where possible as it fully contains the light version and accounts for resurrected/unparked domains. </details>NSFW Blocklist
Created from requests, a blocklist for NSFW domains is available in Adblock Plus format here: nsfw.txt
<details> <summary>Details about the NSFW Blocklist</summary> <ul> <li>Domains are automatically retrieved from the Tranco Top Sites Ranking daily</li> <li>Dead domains are removed daily</li> <li>Note that resurrected domains are not added back into the blocklist</li> <li>Note that parked domains are not checked for in this blocklist</li> </ul> Total domains: 12125 <br> <br> This blocklist does not just include adult videos, but also NSFW content of the artistic variety (rule34, illustrations, etc). </details>Malware Blocklist
A blocklist for malicious domains extracted from Proofpoint's Emerging Threats rulesets can be found here: jarelllama/Emerging-Threats
Parts of the rulesets are integrated into the Scam Blocklist as well.
Sources
Retrieving scam domains using Google Search API
Google provides a Search API to retrieve JSON-formatted results from Google Search. A list of search terms almost exclusively found in scam sites is used by the API to retrieve domains. See the list of search terms here: search_terms.csv
Details
Scam sites often do not have long lifespans; malicious domains may be replaced before they can be manually reported. By programmatically searching Google using paragraphs from real-world scam sites, new domains can be added as soon as Google crawls the site. This requires no manual reporting.
The list of search terms is proactively maintained and is mostly sourced from investigating new scam site templates seen on r/Scams.
Active search terms: 9
API calls made today: 69
Domains retrieved today: 51
Retrieving phishing NRDs using dnstwist
New phishing domains are created daily, and unlike other sources that rely on manual reporting, dnstwist can automatically detect new phishing domains within days of their registration date.
dnstwist is an open-source detection tool for common cybersquatting techniques like Typosquatting, Doppelganger Domains, and IDN Homograph Attacks.
Details
dnstwist uses a list of common phishing targets to find permutations of the targets' domains. The target list is a handpicked compilation of cryptocurrency exchanges, delivery companies, etc. collated while wary of potential false positives. The list of phishing targets can be viewed here: phishing_targets.csv
The generated domain permutations are checked for matches in a newly registered domains (NRDs) feed comprising domains registered within the last 30 days. Each permutation is tested for alternate top-level domains (TLDs) using the 15 most prevalent TLDs from the NRD feed at the time of retrieval.
Active targets: 50
Domains retrieved today: 104
Regarding other sources
All sources used presently or formerly are credited here: SOURCES.md
The domain retrieval process for all sources can be viewed in the repository's code.
Automated filtering process
- The domains collated from all sources are filtered against an actively maintained whitelist (scam reporting sites, forums, vetted stores, etc.)
- The domains are checked against the Tranco Top Sites Ranking for potential false positives which are then vetted manually
- Common subdomains like 'www' are stripped. The list of subdomains checked for can be viewed here: subdomains.txt
- Only domains are included in the blocklist; URLs are stripped down to their domains and IP addresses are manually checked for resolving DNS records
- Redundant rules are removed via wildcard matching. For example, 'abc.example.com' is a wildcard match of 'example.com' and, therefore, is redundant and removed. Wildcards are occasionally added to the blocklist manually to further optimize the number of entries
Entries that require manual verification/intervention are sent in a Telegram notification for fast remediations.
The full filtering process can be viewed in the repository's code.
Dead domains
Dead domains are removed daily using AdGuard's Dead Domains Linter.
Dead domains that are resolving again are included back into the blocklist.
Dead domains removed today: 4637
Resurrected domains added today: 154
Parked domains
From initial testing, 9% of the blocklist consisted of parked domains that inflated the number of entries. Because these domains pose no real threat (besides the obnoxious advertising), they are removed from the blocklist daily.
A list of common parked domain messages is used to automatically detect these domains. This list can be viewed here: parked_terms.txt
If these parked sites no longer contain any of the parked messages, they are assumed to be unparked and are added back into the blocklist.
[!TIP] For list maintainers interested in integrating the parked domains as a source, the list of daily-updated parked domains can be found here: parked_domains.txt (capped to newest 8000 entries)
Parked domains removed today: 229
Unparked domains added today: 87
As seen in
- Fabriziosalmi's Hourly Updated Domains Blacklist
- Hagezi's Threat Intelligence Feeds
- Sefinek24's blocklist generator and collection
- T145's Black Mirror
- The oisd blocklist
- doh.tiar.app privacy DNS
- dnswarden privacy-focused DNS
- file-git.trli.club
- iam-py-test/my_filters_001
Resources / See also
- AdGuard's Dead Domains Linter: simple tool to check adblock filtering rules for dead domains
- AdGuard's Hostlist Compiler: simple tool that compiles hosts blocklists and removes redundant rules
- Elliotwutingfeng's repositories: various original blocklists
- Google's Shell Style Guide: Shell script style guide
- Grammarly: spelling and grammar checker
- Jarelllama's Blocklist Checker: generate a simple static report for blocklists or see previous reports of requested blocklists
- Legality of web scraping: the law firm of Quinn Emanuel Urquhart & Sullivan's memoranda on web scraping
- ShellCheck: static analysis tool for Shell scripts
- Tranco: research-oriented top sites ranking hardened against manipulation
- VirusTotal: analyze suspicious files, domains, IPs, and URLs to detect malware (also includes WHOIS lookup)
- iam-py-test/blocklist_stats: statistics on various blocklists
Appreciation
Thanks to the following people for the help, inspiration, and support!
@T145 - @bongochong - @hagezi - @iam-py-test - @sefinek24 - @sjhgvr
Contributing
You can contribute to this project in the following ways:
- Sponsorship
- Star this repository
- Code reviews
- Report domains and false positives
- Report false negatives in the whitelist
- Suggest search terms for the Google Search source
- Suggest phishing targets for the dnstwist and Regex Matching sources
- Suggest new sources
- Suggest parked terms for the parked domains detection
- Report false positives in the parked domains file