Awesome
黑手册(DarkHandBook)
Update by evilcos, for DarkHandBook.io
Blockchain dark forest selfguard handbook<br> Master these, master the security of your cryptocurrency.<br>
:fire:Website: https://darkhandbook.io/<br> :cn:中文版:《区块链黑暗森林自救手册》<br>
扩展阅读,持续更新...
这里会列一些我个人总结的、围绕黑手册的扩展阅读,基本都会是 Twitter Thread 形式。
Telegram Safeguard 骗局引导运行 Powershell 恶意代码<br> https://x.com/evilcos/status/1866454053129269371
@solana/web3.js 供应链投毒事件<br> https://x.com/evilcos/status/1864101006247907415
又一个画蛇添足机制导致的被盗...Arbitrum WBTC 支持的 permit 机制被钓鱼利用...<br> https://x.com/evilcos/status/1862851691214983365
又一起针对 Crypto 行业的 XSS 攻击,攻击者利用 Cointelegraph 网站的 XSS 漏洞,钓用户 X 账号权限<br> https://x.com/evilcos/status/1861938366541111372
Mac 电脑被投毒恶意代码(冒充假 VC 引用下载恶意的会议软件)后应该怎么办<br> https://x.com/evilcos/status/1861417641174552803
AI 投毒攻击:用 GPT 给出的代码来写 bot,没想到 GPT 给的代码是带后门的,会将私钥发给钓鱼网站<br> https://x.com/evilcos/status/1859752658061623593
安全小习惯:清除剪切板<br> https://x.com/evilcos/status/1855590656108007870
Lottie Player 模块投毒事件,前端引用第三方 js 的最佳安全实践<br> https://x.com/evilcos/status/1851795341710102694
黑客偷走用户 Passkey 的可能方法<br> https://x.com/evilcos/status/1851646271200928225
利用 ipfs[.]io 来托管的钓鱼工具 rocketDrainer<br> https://x.com/evilcos/status/1849093221609361415
呼吁缓解或根除 permit/permit2 这类离线授权签名风险<br> https://x.com/evilcos/status/1844675640718745874<br> https://x.com/evilcos/status/1844593157654086115<br> https://x.com/evilcos/status/1844746404922831183<br> https://x.com/evilcos/status/1845631292169503005<br> https://x.com/evilcos/status/1845632816077480435<br> https://x.com/evilcos/status/1846732024536879605<br> https://x.com/evilcos/status/1850842001836740711
注意 GMGN、DEXTools、DEX Screener 等平台的各种貔貅盘,除了第三方安全工具判断也可以结合 Claude/GPT 辅助,效果不错<br> https://x.com/evilcos/status/1838874085641859321
用 Cursor 实现的 BIP39 Mnemonic Recovery Calculator<br> https://x.com/evilcos/status/1837001617482338631
留意 Blast WETH 的可升级及 permit 离线授权签名钓鱼风险<br> https://x.com/evilcos/status/1836569696742838470
上古技巧,永不落后...🤣钓鱼引诱你按说明执行了恶意代码<br> https://x.com/evilcos/status/1834497295049691576
5547 万枚 DAI 被 Inferno Drainer 一笔钓走,受害者有关 DSProxy 合约的 owner 被钓鱼设置(SetOwner)成了钓鱼有关钱包地址。这个手法和当年搞 OpenSea Wyvern Protocol 类似<br> https://x.com/evilcos/status/1826129033324802433
TX1z3qJy1MQcma7VMab2rMrB5JrFvpHCMM<br> TX1z3qJy1MQcma7VMab2rMrB5JrFvpHСММ<br> 这两个地址最后三字符的区别是什么?<br> https://x.com/evilcos/status/1823216037325836323
老伎俩,汇丰银行账面余额的坑(USD CLEARING CHEQUE)<br> https://x.com/evilcos/status/1822813334972096765
X/Twitter 被盗了怎么办?<br> https://x.com/evilcos/status/1818809893907996676
用魔法打败魔法:[ChatGPT] How AI helps me earn Ethereum 2,400$ Daily 骗局<br> https://x.com/evilcos/status/1816699668409262164
关于 permit 离线授权机制争议的看法<br> https://x.com/evilcos/status/1816030237584703546
案例:简单解析除了常见的授权钓鱼,还有什么姿势可以钓走你的资产<br> https://x.com/evilcos/status/1811622322375393613
🕵️黑 U 泛滥,我们在 MistTrack 平台上上线了个小工具,方便查询你关心的钱包地址是否存在黑 U 风险<br> https://x.com/evilcos/status/1811412196691460530
TON 钓鱼一键盗取用户 TON 钱包里的有关资产(包括 NFT,特别的如 Anonymous Telegram Numbers 等)<br> https://x.com/evilcos/status/1805478404382507305<br> https://x.com/evilcos/status/1805051980634857798
Chrome 恶意扩展如果有 Cookies 读写权限,危害<br> https://x.com/evilcos/status/1797639815917384080<br> https://x.com/evilcos/status/1797550276926411080
是不是飘了?来来来,安全小考题又来了...下面哪个 token 没有 permit 离线授权钓鱼风险?<br> https://x.com/evilcos/status/1797219088085004391
在 Crypto 行业,许多朋友还不清楚 approve/permit 的区别,虽然科普多次...🤖于是我问了 GPT 3 个问题,解析得还不错了<br> https://x.com/evilcos/status/1796136187125793260
TON Tonkeeper 转账消息 comment 机制被钓鱼利用<br> https://x.com/evilcos/status/1788755896186880276
如何防御首尾号钓鱼<br> https://x.com/evilcos/status/1786576421688660111
首尾号被钓 1155 个 WBTC,价值近 7000 万美金。这个用户刚刚遭遇了首尾号相似钱包地址的钓鱼攻击<br> https://x.com/evilcos/status/1786385658002522293
📓黑手册(区块链黑暗森林自救手册) v1.2 中文版发布,新增“那些工具”章节及更新“贡献者”、“那些官网”<br> https://x.com/evilcos/status/1783007122235736369
写得非常好,图亮了😍,授权钓鱼的主要三种技巧的科普:approve/permit/permit2<br> https://x.com/evilcos/status/1781999083818992059
带毒的挖矿工具 Ore.vbs<br> https://x.com/evilcos/status/1779356331381838157
一个有趣问题:iPhone 安装个知名钱包,然后飞行模式,是否算是很好的硬件钱包?<br> https://x.com/evilcos/status/1775727351693037732
X/Twitter 被黑发送钓鱼链接,被黑的几个主要原因<br> https://x.com/evilcos/status/1773912704635580559?s=20
再科普 permit 离线授权签名<br> https://x.com/evilcos/status/1771350889808408780?s=20
比特币钓鱼又来了,理论上一键可以钓走目标钱包地址里的所有 UTXO,其中包括铭文资产、Atomicals 资产等<br> https://x.com/evilcos/status/1767709209397956710?s=20
反向钓鱼,揭露骗子团伙,利用 token 精度钓鱼的套路<br> https://x.com/evilcos/status/1767493811524206831?s=20
想法:钱包用户交互的“冷静期”/“防火墙”机制<br> https://x.com/evilcos/status/1766390328360394907?s=20
想法:有许多被盗是难以知道具体原因的,尤其助记词/私钥泄露这种<br> https://x.com/evilcos/status/1764528033556533730?s=20
老钓鱼团伙 PinkDrainer 这样来偷目标地址上的 ETH<br> https://x.com/evilcos/status/1763914259262755123?s=20
早上又一位 X 友被视频会议木马将数多个钱包洗劫一空,已知损失至少 15 万美金,需要注意的点<br> https://x.com/evilcos/status/1761252214369354040?s=20
再披露:“假记者”骗 X 授权发钓鱼链接的套路<br> https://x.com/evilcos/status/1756240509969092745?s=20
关于 ERC404 项目安全风险的一些观点<br> https://x.com/evilcos/status/1755777391778279525?s=20<br> https://x.com/evilcos/status/1755466102061351289?s=20
推荐教程:私钥泄露的钱包地址如何抢救之后的空投资金或待解锁资金<br> https://x.com/evilcos/status/1754820371319300527?s=20
关于 EVM/Solidity/ERC20/721 等等以太坊的这些玩意天生不安全的观点<br> https://x.com/evilcos/status/1753064430198526177?s=20
Angel Drainer 针对 EigenLayer Strategy Manager 合约的 queueWithdrawal (0xf123991e) 函数的钓鱼利用<br> https://x.com/evilcos/status/1752875528070279623?s=20
如何武装自己的钱包,避开钓鱼<br> https://x.com/evilcos/status/1752513050060763502?s=20
一次失败的救援,渔翁最终获利超 470 万美金<br> https://x.com/evilcos/status/1749664598742155481?s=20
关于授权的小考题<br> https://x.com/evilcos/status/1749644865464660416?s=20<br> https://x.com/evilcos/status/1746448070840402390?s=20
Solana 钓鱼在页面上教用户 1->2->3 一步步关闭 Phantom 钱包的安全提醒<br> https://x.com/evilcos/status/1748622024748957952?s=20
[UPDATE 20240119] Crypto 钓鱼常见手法<br> https://x.com/evilcos/status/1748284899453481221?s=20
Solana 代币授权风险检查<br> https://x.com/evilcos/status/1746360655593226738?s=20
MEV 套利陷阱合约:Easy to Use Arbitrage MEV Bot for Uniswap<br> https://x.com/evilcos/status/1745728599171457120?s=20
骗子私信发来的链接为什么显示的是 calendly[.]com 这种真 Calendly 官方链接?<br> https://x.com/evilcos/status/1745274487569076354?s=20
案例分享:定位两年多前留下的授权隐患<br> https://x.com/evilcos/status/1743842996498714831?s=20
DDoS/CC 是非常典型的上古时代就开始流行的丛林法则<br> https://x.com/evilcos/status/1742123750185947188?s=20
铭文 saʦ vs sats, raʦ vs rats 欺骗 MySQL 数据库解析导致恶意挂单<br> https://x.com/evilcos/status/1741064972975952098?s=20
小心土狗铭文项目<br> https://x.com/evilcos/status/1740224294494580910?s=20
Avascriptions 平台错误网络提醒机制不充分导致用户打错资产到其他 EVM 链(已解决)<br> https://x.com/evilcos/status/1739474148387385783?s=20
小心 Solana 上的钓鱼:一笔签名可以几乎转走你目标钱包地址里的所有资产<br> https://x.com/evilcos/status/1739187245456961557?s=20
Atomicals 资产燃烧风险<br> https://x.com/evilcos/status/1737738046265872455?s=20
比特币低手续费霸占铭文等资产 PSBT 交易风险<br> https://x.com/evilcos/status/1735685957662441563?s=20
使用 Passkey 认证机制的钱包,一种安全与体验平衡不错的方式<br> https://x.com/evilcos/status/1734137806015037631?s=20
案例分享:经典授权钓鱼如何分析定位<br> https://x.com/evilcos/status/1732627608440115665?s=20
细节是魔鬼👹,钱包 UI 对抗首尾号钓鱼技巧的建议<br> https://x.com/evilcos/status/1727940167649124627?s=20
案例分享:钓鱼合约 create2 + permit 将离线授权签名在链上授权后转走 $ARB<br> https://x.com/evilcos/status/1730517667810083189?s=20
比特币被盗的几种方式(注意下签名)<br> https://x.com/evilcos/status/1727940167649124627?s=20
比特币生态 Atomicals 由于签名类型支持 SIGHASH_NONE,导致用户资产被盗<br> https://x.com/evilcos/status/1726992159436644708?s=20
friend.tech 用户被盗的一次成功追回<br> https://x.com/evilcos/status/1725148293502767404?s=20
钓鱼用 Create2 来预创建资金接收地址,绕过钱包的安全检测机制<br> https://x.com/evilcos/status/1723642251853922595?s=20
又一个设计感很好的链游木马<br> https://x.com/evilcos/status/1721847917152198914?s=20
记住 approve 与 permit/permit2 授权的区别<br> https://x.com/evilcos/status/1721753572436738218?s=20
硬件安全密钥(Security Key)是安全认证的标配之一了,在 2FA 场景下可以很好对抗钓鱼网站<br> https://x.com/evilcos/status/1721705293250461842?s=20
貔貅盘一直很泛滥,谨慎对待“机扫安全数据”...<br> https://x.com/evilcos/status/1720311395512906196?s=20
慢雾发布《智能合约安全审计技能树》<br> https://x.com/evilcos/status/1714893390800945587?s=20
慎用围绕 friend.tech 做的各类工具<br> https://x.com/evilcos/status/1714178009291456602?s=20
恶意书签盗取用户 friend.tech 资金<br> https://x.com/evilcos/status/1713164067358294293?s=20
Crypto 钓鱼目前流行的手法大概分类(技术线)<br> https://x.com/evilcos/status/1709135646294671595?s=20
friend.tech 用户账号被黑资产被盗案例<br> https://x.com/evilcos/status/1709030582150381713?s=20
钓鱼网站诱骗用户添加一个“新网络”,但 Chain ID 不变<br> https://x.com/evilcos/status/1707723997780344904?s=20
陷阱合约:目标地址通过较隐蔽方式计算得出…<br> https://x.com/evilcos/status/1705156497481904519?s=20
Coinbase Wallet 上的 Web3 消息网络协议钓鱼风险<br> https://x.com/evilcos/status/1704389310089453666?s=20
friend.tech code 遍历风险<br> https://x.com/evilcos/status/1702649514283381218?s=20
Vitalik 推特号被 SIM Swap 攻击<br> https://x.com/evilcos/status/1701413519798026676?s=20
Lido 的 LDO Token 假充值风险<br> https://x.com/evilcos/status/1700796470163841125?s=20<br> 注:假充值风险是我们 2018 年首提且一直在沉淀研究的细分安全方向,这种风险主要影响的是中心化平台,如果没正确对接相关公链或 Token,就可能导致被假充值。这种风险广泛存在。
一个安全考点:有朋友私信问我:不小心点了这种签名,是否有被盗币风险<br> https://x.com/evilcos/status/1699691438802620781?s=20
Discord 自定义靓号链接过期时被钓鱼团伙抢注风险<br> https://x.com/evilcos/status/1698259690000679049?s=20
黑手册灵魂的安全建议就这两条:
- 始终保持怀疑
- 持续验证
能真 get 这两点的,在 Crypto 行业也挺难踩大坑的…<br> https://twitter.com/evilcos/status/1694536755066875914?s=20
警惕恶意合约放长线钓大鱼<br> https://twitter.com/evilcos/status/1693083229191114875?s=20
friend.tech 的一些安全风险<br> https://twitter.com/evilcos/status/1692780573507596585?s=20<br> https://twitter.com/evilcos/status/1693581053972402453?s=20
在时间紧迫的场景下,当发现电脑疑似有“木马”,应当如何及时止损<br> https://twitter.com/evilcos/status/1691438131852312576?s=20
一笔交易盗走用户可能所有有价值的 token<br> https://twitter.com/evilcos/status/1690202721260081153?s=20
链上喊话指南<br> https://twitter.com/evilcos/status/1687452679625486337?s=20
陷阱合约:隐蔽的 Rug Pull,合约存储引起的跑路盘<br> https://twitter.com/evilcos/status/1684126488910761985?s=20
关于 Worldcoin 采集虹膜这件事<br> https://twitter.com/evilcos/status/1683484789674844167?s=20
关于匿名货币<br> https://twitter.com/evilcos/status/1682044499143569409?s=20
钱包地址缩写建议:0x0000ac61…eb000000<br> https://twitter.com/evilcos/status/1679367167215812608?s=20
陷阱合约:以取消授权名义盗走用户过大的 Gas<br> https://twitter.com/evilcos/status/1677837819350495233?s=20
Blur V2 挂单盲签风险<br> https://twitter.com/evilcos/status/1676899283914870784?s=20
Emblem Vault 中心化风险<br> https://twitter.com/evilcos/status/1676385791269011456?s=20
OPENDIME 这个超级大骰子,功能非常单一的类硬件钱包<br> https://twitter.com/evilcos/status/1674955233364185088?s=20
MetaMask 安全沙盒机制 LavaMoat<br> https://twitter.com/evilcos/status/1674789379125178370?s=20
MPC 与智能合约钱包的一点看法<br> https://twitter.com/evilcos/status/1674394959615754241?s=20
HTML 铭文引入的安全风险<br> https://twitter.com/evilcos/status/1673316843501793282?s=20
Web3 安全入门(重点智能合约安全)<br> https://twitter.com/evilcos/status/1671088109591863296?s=20
比特币铭文一键批量钓鱼<br> https://twitter.com/evilcos/status/1667389165804343297?s=20
把以太坊 NFT 带到比特币的做法是有去无回的(BRC-721E)<br> https://twitter.com/evilcos/status/1666674623554129921?s=20
别以为开启了 Discord 2FA 就万事大吉了<br> https://twitter.com/evilcos/status/1665673399731998720?s=20
伪造事件的诈骗合约,再科普<br> https://twitter.com/evilcos/status/1664226365959446534?s=20
Telegram 骗子伪造安全助手<br> https://twitter.com/evilcos/status/1663848225554706432?s=20
歌曲:) 随风潜入夜、润物细无声<br> https://twitter.com/evilcos/status/1662274150319423489?s=20
Ledger Recovery 引起有关硬件钱包的一些安全话题<br> https://twitter.com/evilcos/status/1659724906609909761?s=20<br> https://twitter.com/evilcos/status/1659526623962755072?s=20<br> https://twitter.com/evilcos/status/1658400654195568641?s=20
检查与取消与漏洞合约有关的授权<br> https://twitter.com/evilcos/status/1659236088979034113?s=20
一个安全冷知识:连接陌生 Wi-Fi 的安全风险已经比数年前小了非常非常多<br> https://twitter.com/evilcos/status/1658817516599386112?s=20
硬件钱包被高手替换了个有问题的固件<br> https://twitter.com/evilcos/status/1658341670105288704?s=20
小心小应用拿走你 Twitter 账号的许多关键权限<br> https://twitter.com/evilcos/status/1657220098174889984?s=20
慢雾:Web3 钱包 eth_sign 支持情况分析<br> https://twitter.com/evilcos/status/1656576468946915328?s=20
流行的 Permit 签名钓鱼再解析<br> https://twitter.com/evilcos/status/1656543466707648514?s=20
Scam Sniffer 专门针对 Permit2 签名钓鱼出的安全检查和取消授权解决方案<br> https://twitter.com/evilcos/status/1655831186743394306?s=20
RevokeCash 出的取消签名功能<br> https://twitter.com/evilcos/status/1655744296828694528?s=20
比特币铭文(Ordinals)/BRC-20 风险提醒<br> https://twitter.com/evilcos/status/1654710328960364544?s=20<br> https://twitter.com/evilcos/status/1654408076605407232?s=20<br> https://twitter.com/evilcos/status/1653296237662334976?s=20
钓鱼网页禁用开发者工具(DevTools)技巧<br> https://twitter.com/evilcos/status/1652873300534767616?s=20
进化中的钱包地址首尾号钓鱼技术能力<br> https://twitter.com/evilcos/status/1652622264028766208?s=20
CryptoPunks 一个漏洞导致的分叉文化<br> https://twitter.com/evilcos/status/1650014094920151041?s=20
RevokeCash 的这篇关于 Crypto 钓鱼的几种方式的总结很赞<br> https://twitter.com/evilcos/status/1648697629453488128?s=20
警惕 WalletConnect 使用不当可能存在的钓鱼风险<br> https://twitter.com/evilcos/status/1648306943583457280?s=20
关于链游木马及浏览器扩展木马的安全提醒<br> https://twitter.com/evilcos/status/1644551979618955265?s=20
慢雾针对 Web3 项目的安全实践要求<br>
https://twitter.com/evilcos/status/1644237107945414656?s=20
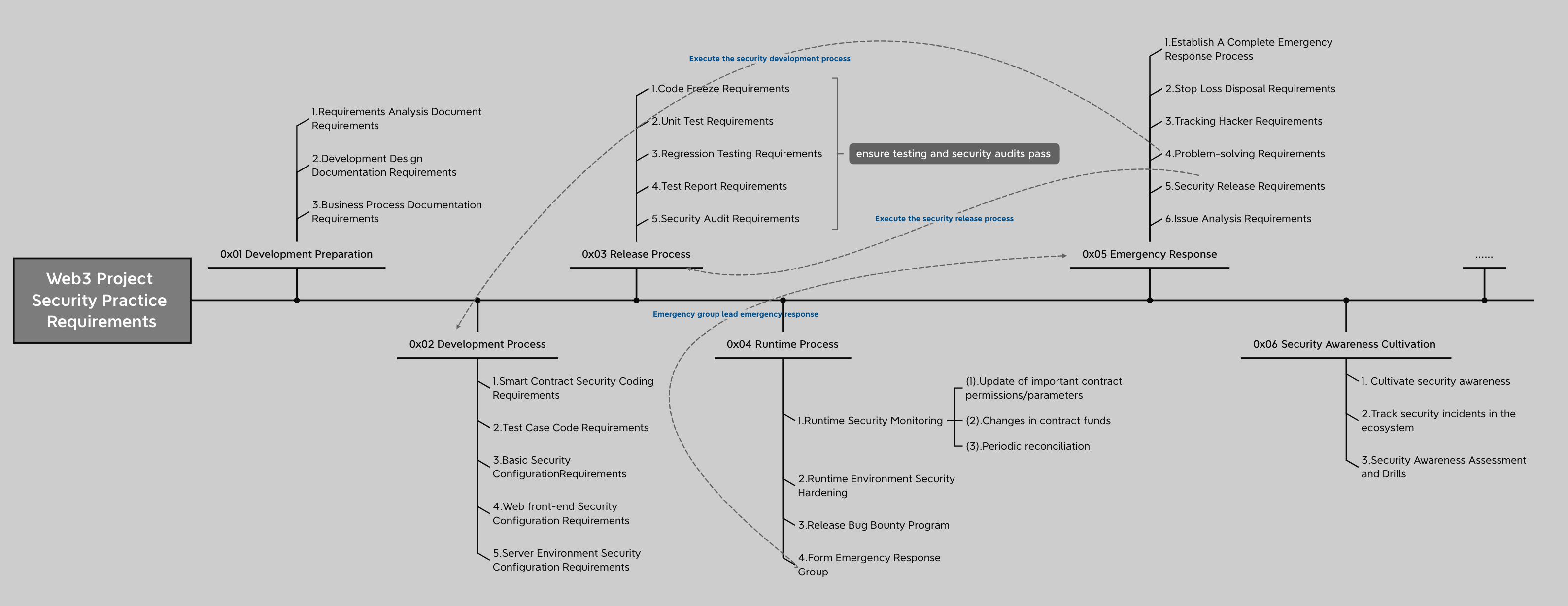
呼吁钱包们禁用 eth_sign 这种盲签机制<br> https://twitter.com/evilcos/status/1643410971409670145?s=20
Mac 电脑中毒后的危害都有哪些<br> https://twitter.com/evilcos/status/1640935800195125248?s=20
偷 Gas 的空投代币<br> https://twitter.com/evilcos/status/1640618513676263424?s=20
小心你的钱包及相关账号被链游木马一窝端<br> https://twitter.com/evilcos/status/1640366330405883906?s=20
钱包有关的事件伪造+首尾字符欺骗钓鱼<br> https://twitter.com/evilcos/status/1639125376285945857?s=20
针对 Cloudflare 的静默劫持攻击<br> https://twitter.com/evilcos/status/1639122575229087744?s=20
可升级智能合约偷梁换柱钓鱼盗币<br> https://twitter.com/evilcos/status/1639114967680159744?s=20
MetaMask 支持 EIP-4361,钱包同源策略开始来了<br> https://twitter.com/evilcos/status/1639091781374717953?s=20
针对 Blur 平台的 NFT “盲签”钓鱼<br> https://twitter.com/evilcos/status/1632712060114194433?s=20
如下四种签名弹框,安全性如何?为什么?<br> https://twitter.com/evilcos/status/1632663595757760512?s=20
闪电网络通道科普一例<br> https://twitter.com/evilcos/status/1628945985811660800?s=20
如果你的 Discord token 被钓了,但被你及时发现,以下哪个做法并不能阻止黑客使用你的 Discord token 权限?<br> https://twitter.com/evilcos/status/1628018317893181440?s=20
被钓鱼网站钓走钱包签名后,相关资产被盗了,这个钱包还安全吗?<br> https://twitter.com/evilcos/status/1625387330117992449?s=20
Twitter 链接预览 User-Agent 欺骗钓鱼<br> https://twitter.com/evilcos/status/1624268782993821696?s=20
闪电网络地址等有关科普<br> https://twitter.com/evilcos/status/1621380824867430400?s=20
NFT 钓鱼 Apetainz 的 UI 伪装欺骗<br> https://twitter.com/evilcos/status/1619504230586535936?s=20
删除 MetaMask 扩展时,私钥/助记词文件会如何?<br> https://twitter.com/evilcos/status/1615540204441591814?s=20
当你电脑中相关木马后,木马是如何黑掉你的 MetaMask 的<br> https://twitter.com/evilcos/status/1615931120457220100?s=20
为什么 WETH 一个签名就被钓走<br> https://twitter.com/evilcos/status/1615220059299000324?s=20
Web3 Cybersecurity Academy - Enhancing user asset security Lesson 1<br> https://twitter.com/1nf0s3cpt/status/1614612129671438343?s=20
Telegram 盗号导致盗币<br> https://twitter.com/evilcos/status/1611541986120732672?s=20
APTOS 钓鱼<br> https://twitter.com/evilcos/status/1610910301934989313?s=20
讨论钱包的一个关键安全点<br> https://twitter.com/evilcos/status/1607721007837769728?s=20
Solana 钓鱼<br> https://twitter.com/evilcos/status/1607558572921217027?s=20
警惕密码管理器永久删除风险<br> https://twitter.com/evilcos/status/1606889696436813825?s=20
关于 LastPass 被黑<br> https://twitter.com/evilcos/status/1606615478277132289?s=20
一个有趣的“被盗”案例<br> https://twitter.com/evilcos/status/1605826949850374144?s=20
NFT 零元购技术解析<br> https://twitter.com/evilcos/status/1604067276265000960?s=20
Discord token 废弃方式,三选一:
- 主动登出账号,不是关闭页面;
- 修改密码;
- 添加 2FA 或修改 2FA。
MetaMask CLAIM REWARDS 欺骗<br> https://twitter.com/evilcos/status/1600356939845640193?s=20
看去像乱码的签名是否有风险<br> https://twitter.com/evilcos/status/1599258003798396929?s=20
零转账骗局<br> https://twitter.com/evilcos/status/1598245354951974913?s=20
钓鱼网页模仿 MetaMask 弹框<br> https://twitter.com/evilcos/status/1597813536323170304?s=20
波场(Tron)多重签名骗局<br> https://twitter.com/evilcos/status/1596374505751924736?s=20
突破钓鱼网页反调试<br> https://twitter.com/evilcos/status/1594514681401835520?s=20
MetaMask Security Update 欺骗<br> https://twitter.com/evilcos/status/1593588745353060352?s=20
当 Connect 一个钓鱼网站,会有安全风险吗?<br> https://twitter.com/evilcos/status/1593579289726709760?s=20
钱包「签名」和「授权」的区别<br> https://twitter.com/evilcos/status/1592888608364511233?s=20
Uniswap swapExactTokensForTokens 钓鱼<br> https://twitter.com/evilcos/status/1591783549505511426?s=20
假币安 App 钓鱼<br> https://twitter.com/evilcos/status/1589921365393805312?s=20
OpenSea 签名认证请求<br> https://twitter.com/evilcos/status/1588722701669404672?s=20
signTypedData 用成“盲签”的感觉<br> https://twitter.com/evilcos/status/1588522243285716994?s=20
双因素认证(2FA)安全的话题<br> https://twitter.com/evilcos/status/1587674436710584321?s=20
OpenSea upgradeTo 钓鱼<br> https://twitter.com/evilcos/status/1585909695990022145?s=20
DAI/USDC 等的 permit 签名钓鱼<br> https://twitter.com/evilcos/status/1581215108910309377?s=20
eth_sign 盲签钓鱼<br> https://twitter.com/evilcos/status/1579449487302725647?s=20
几种签名钓鱼区别:eth_sign/personal_sign/signTypedData<br> https://twitter.com/evilcos/status/1578988023945269248?s=20
OpenSea 空投假 Offer 骗局<br> https://twitter.com/evilcos/status/1576747276684259328?s=20
Punycode 字符欺骗钓鱼<br> https://twitter.com/evilcos/status/1563739097893462016?s=20
BGP 劫持案例与科普<br> https://twitter.com/evilcos/status/1560881728910426113?s=20
DNS Hijacking(劫持)案例与科普<br> https://twitter.com/evilcos/status/1557222249958350848?s=20
授权钓鱼识别技巧:0xa22cb465 即 setApprovalForAll<br> https://twitter.com/evilcos/status/1548581215648694273?s=20
被盗了怎么办?<br> https://twitter.com/evilcos/status/1533288715065634817?s=20
:smiling_imp:与其成为千奇百怪的猎物,不如成为特立独行的猎人。