Awesome
Security-Toolkit
1.提权类:
1.juicy-potato
参考文章:
https://github.com/ohpe/juicy-potato
http://www.freebuf.com/column/181549.html

2.ALPC-EXP

参考文章:
https://hunter2.gitbook.io/darthsidious/privilege-escalation/alpc-bug-0day
http://www.ggsec.cn/ALPC-EXP.html
3.CVE-2018-8120
目标:win7、win2008

参考文章:http://www.freebuf.com/column/173797.html
https://github.com/rapid7/metasploit-framework/tree/master/data/exploits/CVE-2018-8120
https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/windows/local/ms18_8120_win32k_privesc.rb 4.过UAC UACME大量的UAC集锦 https://github.com/hfiref0x/UACME
2.测试类
1.text文件包含几个测试用的dll
2.stager-dll

http://www.ggsec.cn/stager-dll.html
powershell 脚本渗透类
1.powercat == nc
参考资料:http://www.4hou.com/info/news/5205.html
2.nvoke-Obfuscation
参考资料:
http://www.ggsec.cn/Invoke-Obfuscation.html
https://github.com/danielbohannon/Invoke-Obfuscation

3.COM-Object-hijacking
https://github.com/3gstudent/COM-Object-hijacking http://www.ggsec.cn/com-xml.html
4. MMFml
https://github.com/prnd432/MMFml
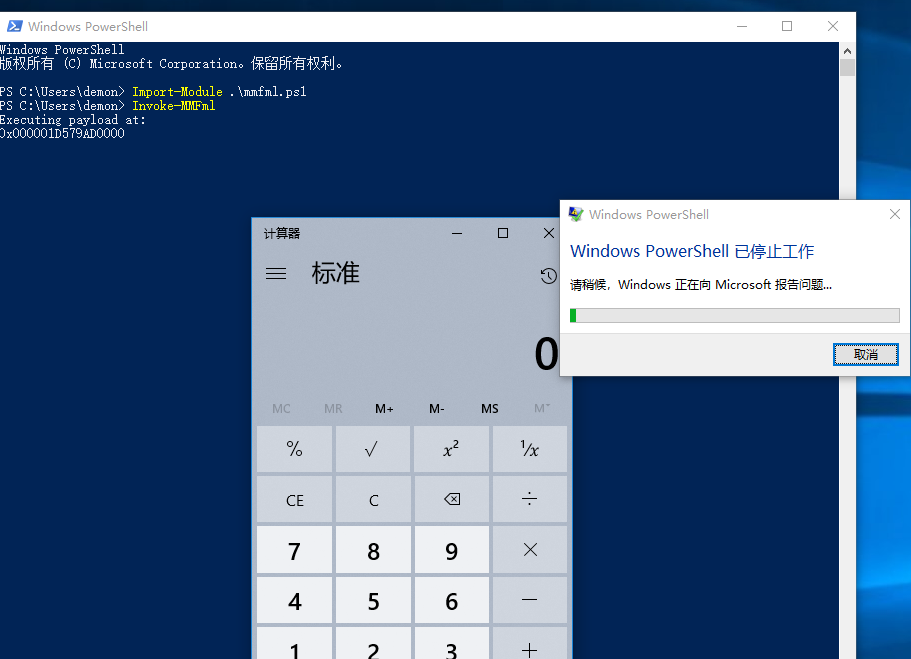
5.powershell文件 包含了大量的渗透脚本
这个就自己去研究吧 https://github.com/Mr-Un1k0d3r/RedTeamPowershellScripts https://github.com/fortify24x7/FuzzySecurity-PowerShell-Suite
其他
1.AnyFileToByte.exe 这是我比较喜欢的一款 将文件转换为数组为c代码。
2.ghosttunnel wif隐蔽通道
参考资料:
http://www.freebuf.com/articles/wireless/171108.html
https://github.com/360PegasusTeam/GhostTunnel
http://www.ggsec.cn/Ghost-tunnel.html
3.CFF Explorer,是一款脱壳后清理不必要的代码的软件
4.injection-master(propagate)
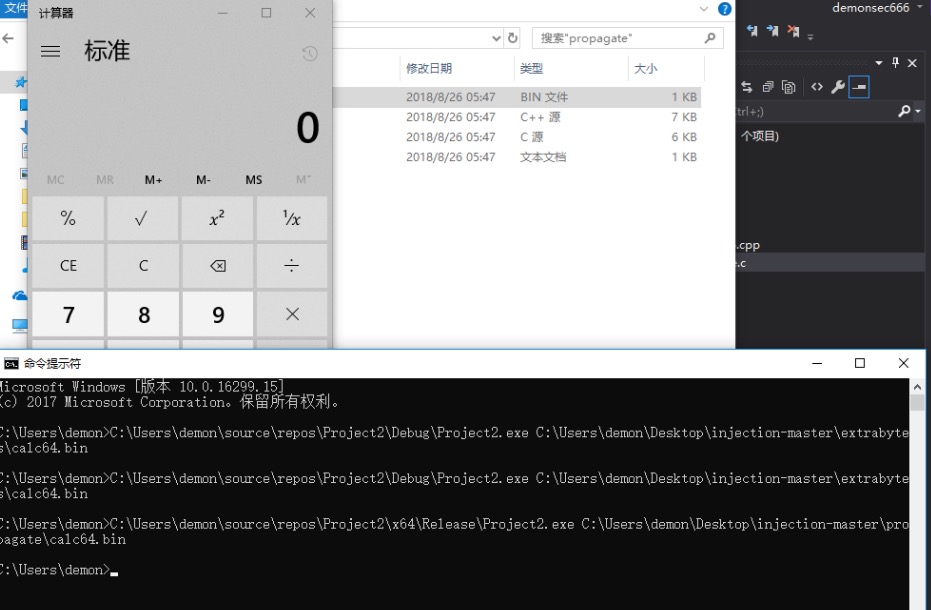
https://github.com/odzhan/injection
https://modexp.wordpress.com/2018/08/23/process-injection-propagate/
参考资料:http://www.ggsec.cn/propagate.html
5.ShellPop

http://www.ggsec.cn/ShellPop.html
https://github.com/0x00-0x00/ShellPop
6.xml_mimikatz
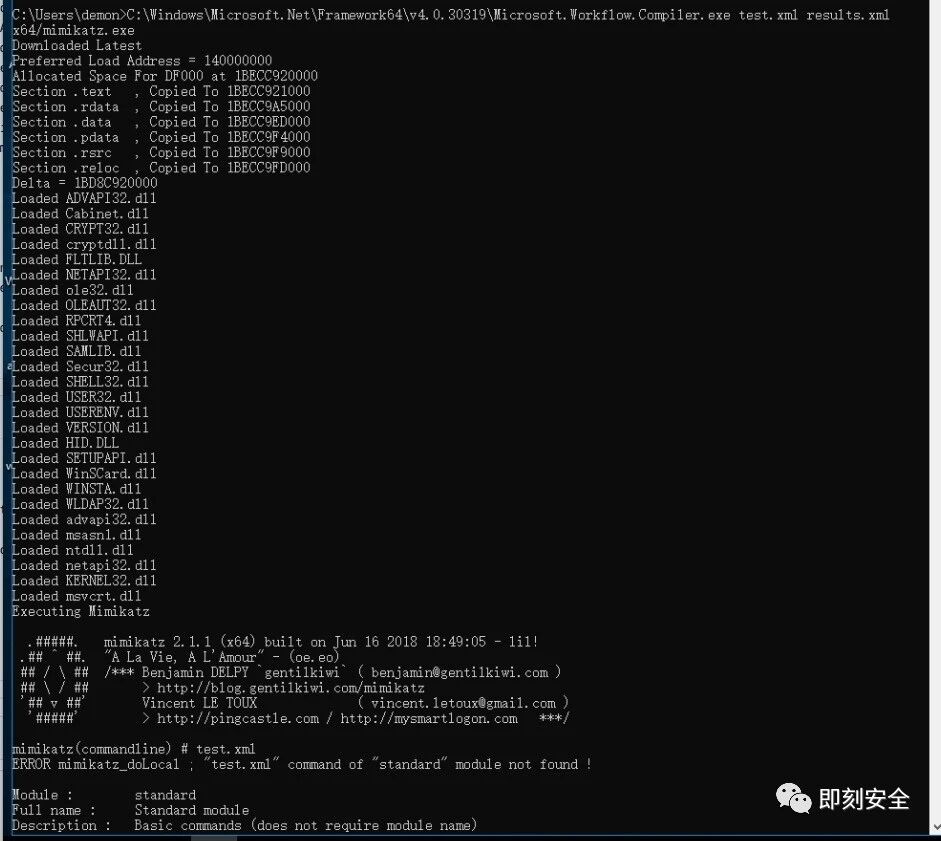 https://gist.github.com/caseysmithrc/b1190e023cd29c1910c01a164675a22e
https://gist.github.com/caseysmithrc/b1190e023cd29c1910c01a164675a22e
6.签名劫持sigthief
http://www.ggsec.cn/sigthief.html https://github.com/secretsquirrel/SigThief
7.Linux_inject_kimi
http://www.ggsec.cn/Linux-inject-kimi.html
内网渗透知识库
https://github.com/LOLBAS-Project/LOLBAS https://lolbas-project.github.io/ https://github.com/3gstudent/Pentest-and-Development-Tips/blob/master/README.md http://adsecurity.org/?p=483 https://gtfobins.github.io/ https://github.com/CyberMonitor/APT_CyberCriminal_Campagin_Collections https://bohops.com/2018/08/18/abusing-the-com-registry-structure-part-2-loading-techniques-for-evasion-and-persistence/ https://attack.mitre.org