Awesome
DigitalSide Threat-Intel
This repository contains a set of Open Source Cyber Threat Intelligence information, mostly based on malware analysis and compromised URLs, IPs and domains.
The purpose of this project is to develop and test new ways to hunt, analyze, collect and share relevant sets of IoCs to be used by SOC/CSIRT/CERT with minimum effort.
Sharing formats
Three formats are available to download the reports:
- MISP feed and events (retention: 7 days) - [GO TO]
- Structured Threat Information Expression - STIX™ v2 (retention: 30 days) [GO TO]
- Comma Separated Values (retention: 30 days) [GO TO]
- Public API using apiosintDS library - [DOCS]
- IoC lists of unique indicators in squid like format (retention: 7 days) splitted in:
- TAXII2 server implementation containing STIX2 bundles shared reports (retention: 24 hours) - [GO TO]
- apiosintDS MISP Module available in any up to dated MISP instance - [DOCS]
The majority of the information is stored in the MISP data format. So, best way to collect data is to subscribe to the Digitalside-misp-feed.
All sharing formats, except for STIX2.1 reports, are based on MISP export format. All reports in any format can be consumed by any up-to-dated MISP instance.
Sharing endpoints
Reports shared by two sharing endpoints:
- This repository: you can clone, subscribe, download managing it with the power of git!
- OSINT.DigitalSide.it: You can crawl it for free and permit you to subscribe tp the MISP feed.
How to subscribe to the Digitalside-misp-feed
Since 2019-09-23 OSINT.digitalside.it MISP feed has been added to the "Default feeds" list available in MISP default installation. The easy way to subscribe to the feed is to select the dedicated activation button.
- Login to MISP with a user having the right permissions to manage feeds
- Go to
Sync Actions -> List Feeds -> Default feeds - Find the OSINT.digitalside.it row
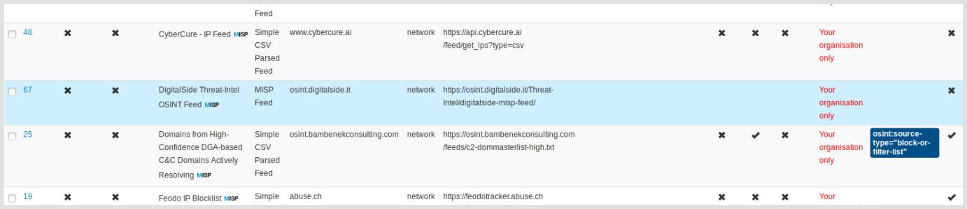
- Select the row and click on "Enable selected" button at the top of the table<br>
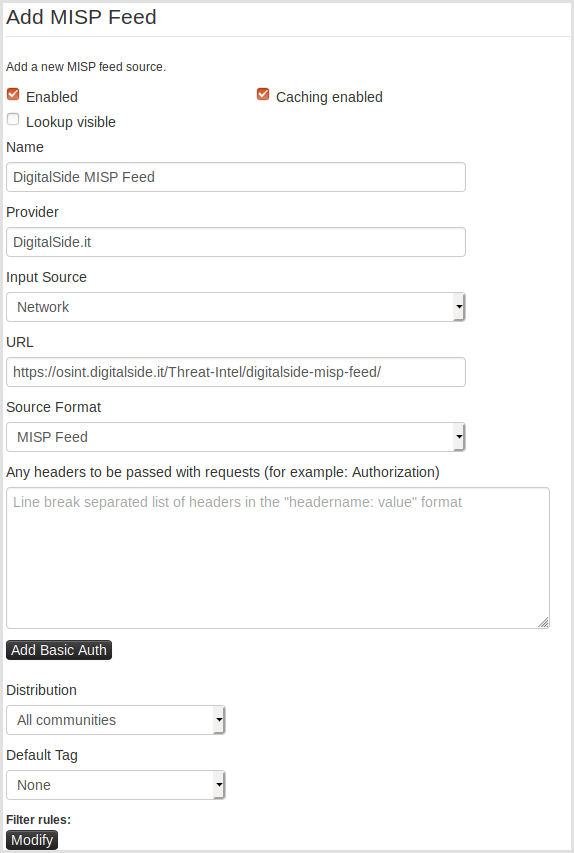
You can also subscribe to the feed manually, following the below instructions.
- Login to MISP with a user having the right permissions to manage feeds
- Go to
Sync Actions -> List Feeds -> Add Feed - Add the MISP feed by using the URL https://osint.digitalside.it/Threat-Intel/digitalside-misp-feed/
Domain white list and MISP Warning List
For more information about domain white list applied to the project, please refer to OSINT.DigitalSide.IT Threat-Intel Domains White List.
Public API
Please visit the DigitalSide-API project page.
Sharing samples
Malware samples are not included in the reports. If you need some binary file for further analysis and investigation, send an email to info[at]digitalside.it, qualifying yourself as member of a SOC/CSIRT/CERT or other cyber security organization working on public safety. No commercial company will be supported at all.
Only PGP signed and encrypted emails from a valid sender will have feedback.
My PGP key ID 30B31BDA. Fingerprint: 0B4C F801 E8FF E9A3 A602 D2C7 9C36 93B2 30B3 1BDA.
Workflow Automation Input/Output
Reports shared here are the result of my personal Malware Analysis Lab. In this first stage of the project I'll focus the activity to find the best way to share IoC. Report contents should change in time. Anyway, backward compatibility will be granted. The goal is to create an external know how to be used for correlation, digital forensics activities, threat intelligence processes, inside a workflow automation process for Incident Response.
In a second phase I'll share information about my Malware Analysis Lab. This way I hope to cover the two main IoC sharing topics:
- How to use OSINT data
- How to produce OSINT data
Credits are granted!
Many reports shared are based on OSINT and CLOSINT sources. All applicable credits are granted. If something wrong, please contact me at info[at]digitalside[dot]it.
About Me
My name is Davide Baglieri and I'm an independent security researcher and consultant. You can find more information at the following links:
My personal purpose about this project is basically for Research & Developing in a continue education and training process I started the 23rd of September 1979.