Awesome
<p align="center"> <img src="https://user-images.githubusercontent.com/5199289/136844524-1527b09f-c5cb-4aa9-be54-5aa92a6086c1.png" width="271" alt="Cute pink owl syft logo"> </p>Syft
A CLI tool and Go library for generating a Software Bill of Materials (SBOM) from container images and filesystems. Exceptional for vulnerability detection when used with a scanner like Grype.
<p align="center"> <a href="https://github.com/anchore/syft/actions/workflows/validations.yaml" target="_blank"><img alt="Validations" src="https://github.com/anchore/syft/actions/workflows/validations.yaml/badge.svg"></a> <a href="https://goreportcard.com/report/github.com/anchore/syft" target="_blank"><img alt="Go Report Card" src="https://goreportcard.com/badge/github.com/anchore/syft"></a> <a href="https://github.com/anchore/syft/releases/latest" target="_blank"><img alt="GitHub release" src="https://img.shields.io/github/release/anchore/syft.svg"></a> <a href="https://github.com/anchore/syft" target="_blank"><img alt="GitHub go.mod Go version" src="https://img.shields.io/github/go-mod/go-version/anchore/syft.svg"></a> <a href="" target="_blank"><img alt="License: Apache-2.0" src="https://img.shields.io/badge/License-Apache%202.0-blue.svg"></a> <a href="https://anchore.com/discourse" target="_blank"><img alt="Join our Discourse" src="https://img.shields.io/badge/Discourse-Join-blue?logo=discourse"/></a> <a rel="me" href="https://fosstodon.org/@syft"><img alt="Follow on Mastodon" src="https://img.shields.io/badge/Mastodon-Follow-blue?logoColor=white&logo=mastodon"/></a> </p>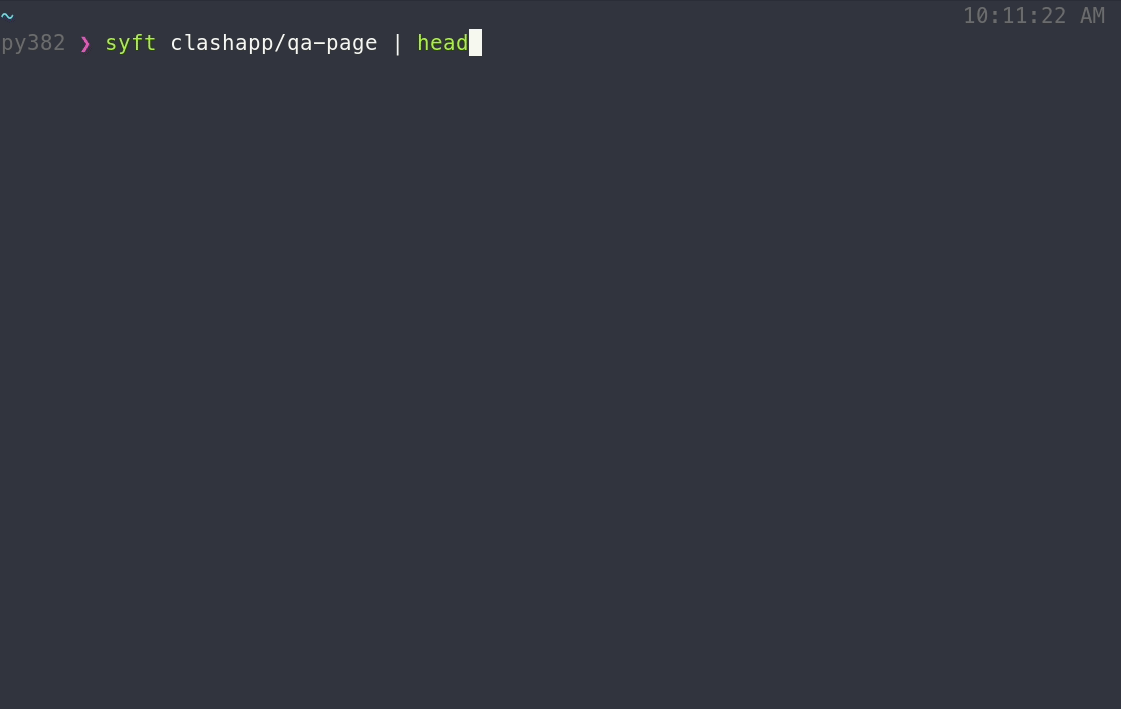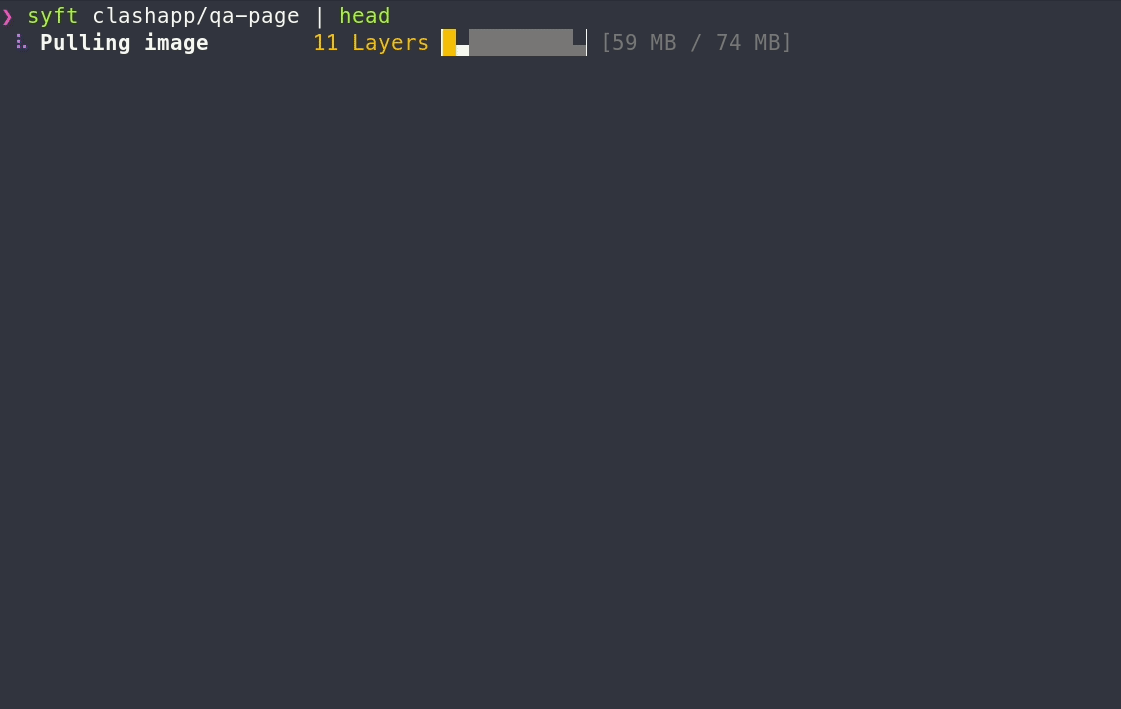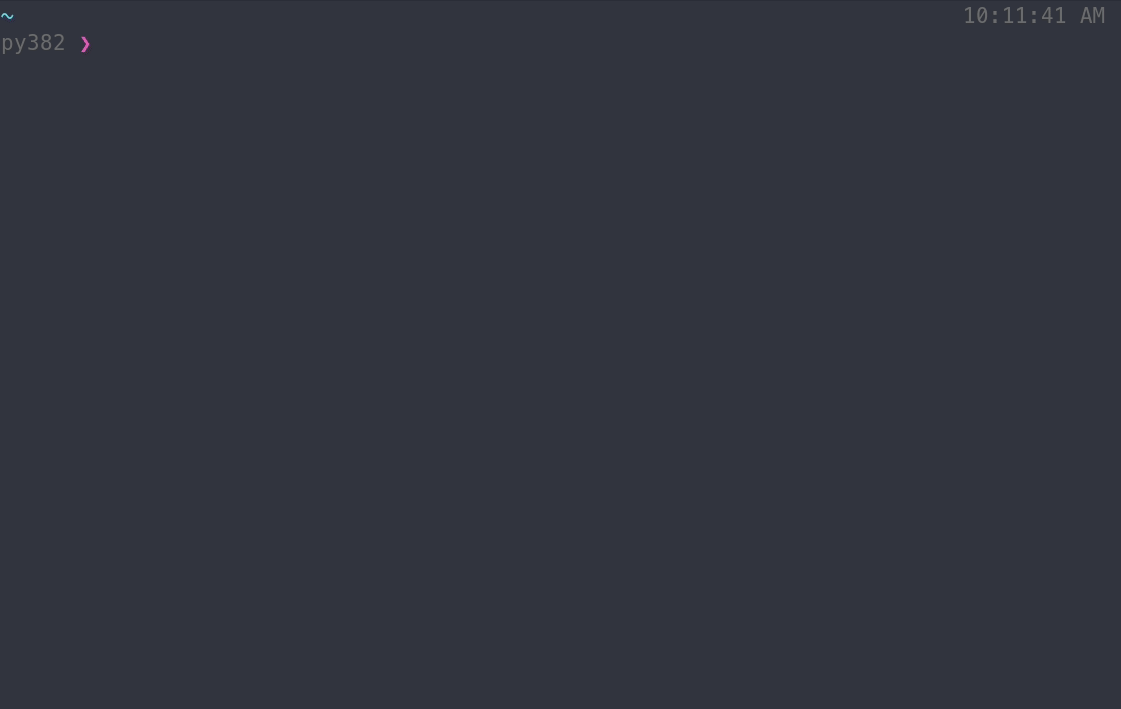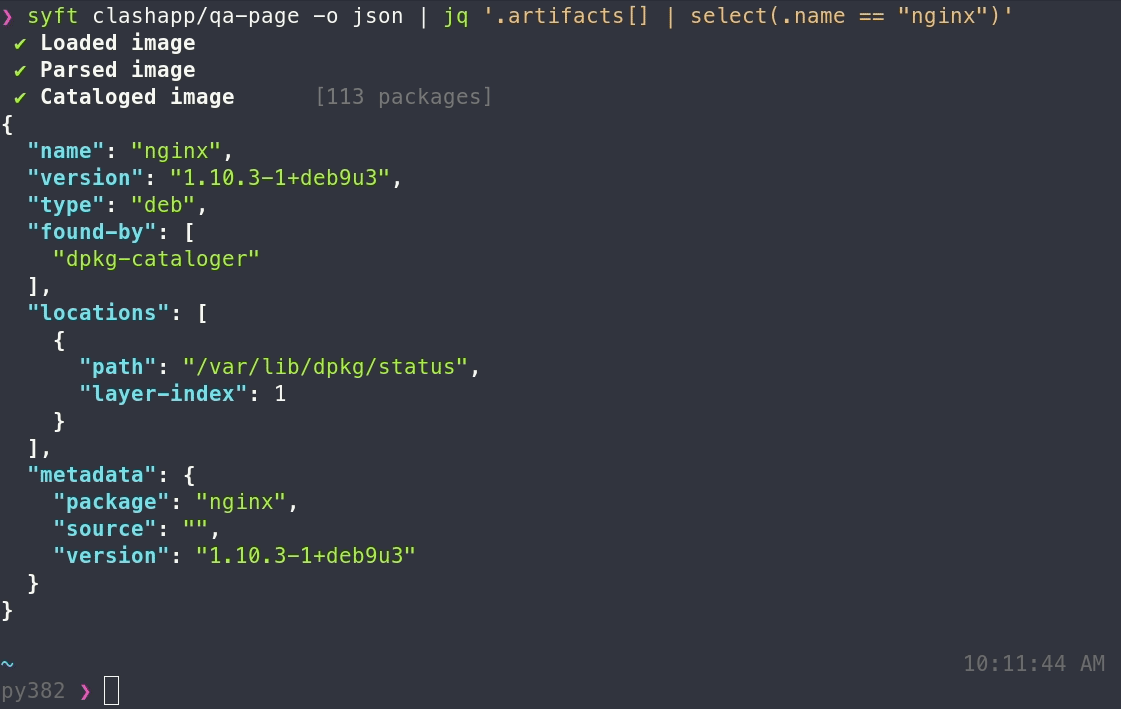
Introduction
Syft is a powerful and easy-to-use open-source tool for generating Software Bill of Materials (SBOMs) for container images and filesystems. It provides detailed visibility into the packages and dependencies in your software, helping you manage vulnerabilities, license compliance, and software supply chain security.
Syft development is sponsored by Anchore, and is released under the Apache-2.0 License. For commercial support options with Syft or Grype, please contact Anchore.
Features
- Generates SBOMs for container images, filesystems, archives, and more to discover packages and libraries
- Supports OCI, Docker and Singularity image formats
- Linux distribution identification
- Works seamlessly with Grype (a fast, modern vulnerability scanner)
- Able to create signed SBOM attestations using the in-toto specification
- Convert between SBOM formats, such as CycloneDX, SPDX, and Syft's own format.
Installation
Syft binaries are provided for Linux, macOS and Windows.
Recommended
curl -sSfL https://raw.githubusercontent.com/anchore/syft/main/install.sh | sh -s -- -b /usr/local/bin
Install script options:
-b: Specify a custom installation directory (defaults to./bin)-d: More verbose logging levels (-dfor debug,-ddfor trace)-v: Verify the signature of the downloaded artifact before installation (requirescosignto be installed)
Homebrew
brew install syft
Scoop
scoop install syft
Chocolatey
The chocolatey distribution of Syft is community-maintained and not distributed by the Anchore team
choco install syft -y
Nix
Note: Nix packaging of Syft is community maintained. Syft is available in the stable channel since NixOS 22.05.
nix-env -i syft
... or, just try it out in an ephemeral nix shell:
nix-shell -p syft
Getting started
SBOM
To generate an SBOM for a container image:
syft <image>
The above output includes only software that is visible in the container (i.e., the squashed representation of the image). To include software from all image layers in the SBOM, regardless of its presence in the final image, provide --scope all-layers:
syft <image> --scope all-layers
Output formats
The output format for Syft is configurable as well using the -o (or --output) option:
syft <image> -o <format>
Where the formats available are:
syft-json: Use this to get as much information out of Syft as possible!syft-text: A row-oriented, human-and-machine-friendly output.cyclonedx-xml: A XML report conforming to the CycloneDX 1.6 specification.cyclonedx-xml@1.5: A XML report conforming to the CycloneDX 1.5 specification.cyclonedx-json: A JSON report conforming to the CycloneDX 1.6 specification.cyclonedx-json@1.5: A JSON report conforming to the CycloneDX 1.5 specification.spdx-tag-value: A tag-value formatted report conforming to the SPDX 2.3 specification.spdx-tag-value@2.2: A tag-value formatted report conforming to the SPDX 2.2 specification.spdx-json: A JSON report conforming to the SPDX 2.3 JSON Schema.spdx-json@2.2: A JSON report conforming to the SPDX 2.2 JSON Schema.github-json: A JSON report conforming to GitHub's dependency snapshot format.syft-table: A columnar summary (default).template: Lets the user specify the output format. See "Using templates" below.
Note that flags using the @<version> can be used for earlier versions of each specification as well.
Supported Ecosystems
- Alpine (apk)
- C (conan)
- C++ (conan)
- Dart (pubs)
- Debian (dpkg)
- Dotnet (deps.json)
- Objective-C (cocoapods)
- Elixir (mix)
- Erlang (rebar3)
- Go (go.mod, Go binaries)
- Haskell (cabal, stack)
- Java (jar, ear, war, par, sar, nar, native-image)
- JavaScript (npm, yarn)
- Jenkins Plugins (jpi, hpi)
- Linux kernel archives (vmlinz)
- Linux kernel modules (ko)
- Nix (outputs in /nix/store)
- PHP (composer)
- Python (wheel, egg, poetry, requirements.txt)
- Red Hat (rpm)
- Ruby (gem)
- Rust (cargo.lock)
- Swift (cocoapods, swift-package-manager)
- Wordpress plugins
Documentation
Our wiki contains further details on the following topics:
- Supported Sources
- File Selection
- Excluding file paths
- Output formats
- Package Cataloger Selection
- Using templates
- Multiple outputs
- Private Registry Authentication
- Attestation (experimental)
- Configuration
Contributing
Check out our contributing guide and developer docs.
Syft Team Meetings
The Syft Team hold regular community meetings online. All are welcome to join to bring topics for discussion.
- Check the calendar for the next meeting date.
- Add items to the agenda (join this group for write access to the agenda)
- See you there!