Awesome
<a href="https://cycode.com/cygives/" alt="Raven is part of Cygives, the community hub for free & open developer security tools."/> <picture> <source media="(prefers-color-scheme: dark)" srcset="./assets/images/Cygives-darkmode.svg"> <source media="(prefers-color-scheme: light)" srcset="./assets/images/Cygives-lightmode.svg"> <img alt="Cygives Banner" src="./assets/images/Cygives-lightmode.svg"> </picture> </a> <picture> <source media="(prefers-color-scheme: dark)" srcset="https://raw.githubusercontent.com/CycodeLabs/raven/main/assets/images/raven-dark-mode.png"> <source media="(prefers-color-scheme: light)" srcset="https://raw.githubusercontent.com/CycodeLabs/raven/main/assets/images/raven-light-mode.png"> <img alt="Raven" src="https://raw.githubusercontent.com/CycodeLabs/raven/main/assets/images/raven-light-mode.png"> </picture>

Raven - CI/CD Security Analyzer
RAVEN (Risk Analysis and Vulnerability Enumeration for CI/CD) is a powerful security tool designed to perform massive scans for GitHub Actions CI workflows and digest the discovered data into a Neo4j database. Developed and maintained by the Cycode research team.
With Raven, we were able to identify and report security vulnerabilities in some of the most popular repositories hosted on GitHub, including:
- FreeCodeCamp (the most popular project on GitHub)
- Storybook (One of the most popular frontend frameworks)
- Fluent UI by Microsoft
- and much more
We listed all vulnerabilities discovered using Raven in the tool Hall of Fame.
What is Raven
The tool provides the following capabilities to scan and analyze potential CI/CD vulnerabilities:
- ⏬ Downloader: You can download workflows and actions necessary for analysis. Workflows can be downloaded either for multiple accounts (user/organization) simultaneously or for public GitHub repositories, sorted by star count. Performing this step is a prerequisite for analyzing the workflows.
- 📊 Indexer: Digesting the downloaded data into a graph-based Neo4j database. This process involves establishing relationships between workflows, actions, jobs, steps, etc.
- 📚 Query Library: We created a library of pre-defined queries based on research conducted by the community.
- ❗ Reporter: Raven has a simple way of reporting suspicious findings. As an example, it can be incorporated into the CI process for pull requests and run there.
Possible usages for Raven:
- Scanner for your own organization's security
- Scanning specified organizations for bug bounty purposes
- Scan everything and report issues found to save the internet
- Research and learning purposes
This tool provides a reliable and scalable solution for CI/CD security analysis, enabling users to query bad configurations and gain valuable insights into their codebase's security posture.
Why Raven
In the past year, Cycode Labs conducted extensive research on fundamental security issues of CI/CD systems. We examined the depths of many systems, thousands of projects, and several configurations. The conclusion is clear – the model in which security is delegated to developers has failed. This has been proven several times in our previous content:
- A simple injection scenario exposed dozens of public repositories, including popular open-source projects.
- We found that one of the most popular frontend frameworks was vulnerable to the innovative method of branch injection attack.
- We detailed a completely different attack vector, 3rd party integration risks, the most popular project on GitHub, and thousands more.
- Finally, the Microsoft 365 UI framework, with more than 300 million users, is vulnerable to an additional new threat – an artifact poisoning attack.
- Additionally, we found, reported, and disclosed hundreds of other vulnerabilities privately.
Each of the vulnerabilities above has unique characteristics, making it nearly impossible for developers to stay up to date with the latest security trends. Unfortunately, each vulnerability shares a commonality – each exploitation can impact millions of victims.
It was for these reasons that Raven was created, a framework for CI/CD security analysis workflows (and GitHub Actions as the first use case). In our focus, we examined complex scenarios where each issue isn't a threat on its own, but when combined, they pose a severe threat.
Setup && Run
To get started with Raven, follow these installation instructions:
Step 1: Install the Raven package
pip3 install raven-cycode
Step 2: Setup a local Redis server and Neo4j database
docker run -d --name raven-neo4j -p7474:7474 -p7687:7687 --env NEO4J_AUTH=neo4j/123456789 --volume raven-neo4j:/data neo4j:5.12
docker run -d --name raven-redis -p6379:6379 --volume raven-redis:/data redis:7.2.1
Another way to setup the environment is by running our provided docker compose file:
git clone https://github.com/CycodeLabs/raven.git
cd raven
make setup
Step 3: Run Raven Downloader
Account mode:
raven download account --token $GITHUB_TOKEN --account-name RavenDemo
Crawl mode:
raven download crawl --token $GITHUB_TOKEN --min-stars 1000
Step 4: Run Raven Indexer
raven index
Step 5: Inspect the results through the reporter
raven report --format raw
At this point, it is possible to inspect the data in the Neo4j database, by connecting http://localhost:7474/browser/.
Prerequisites
- Python 3.9+
- Docker Compose v2.1.0+
- Docker Engine v1.13.0+
Infrastructure
Raven is using two primary docker containers: Redis and Neo4j.
make setup will run a docker compose command to prepare that environment.
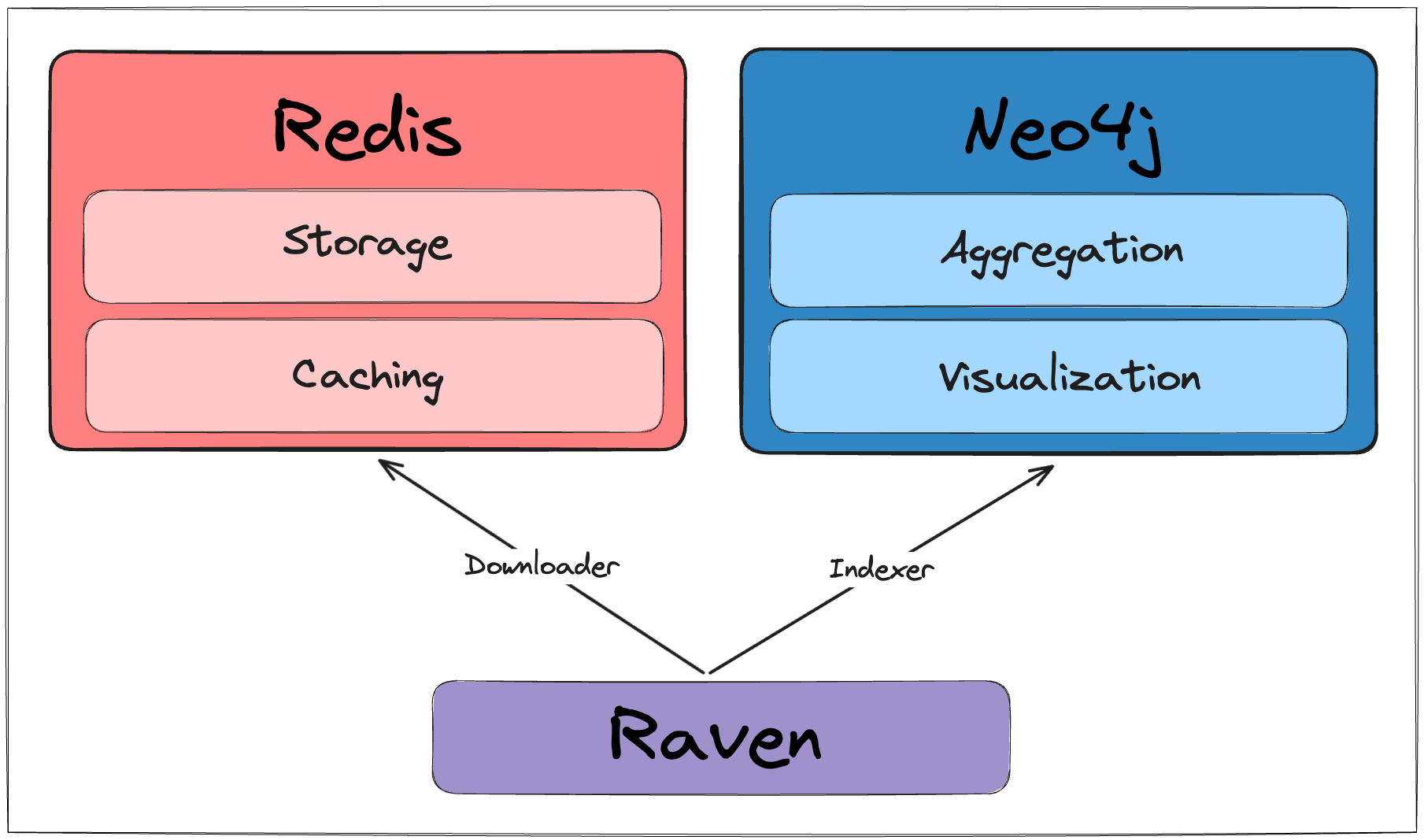
Usage
The tool contains three main functionalities, download and index and report.
Download
Download Account Repositories
usage: raven download account [-h] --token TOKEN [--debug] [--redis-host REDIS_HOST] [--redis-port REDIS_PORT] [--clean-redis] (--account-name ACCOUNT_NAME | --personal)
options:
-h, --help show this help message and exit
--token TOKEN GITHUB_TOKEN to download data from Github API (Needed for effective rate-limiting)
--debug Whether to print debug statements, default: False
--redis-host REDIS_HOST
Redis host, default: localhost
--redis-port REDIS_PORT
Redis port, default: 6379
--clean-redis, -cr Whether to clean cache in the redis, default: False
--account-name ACCOUNT_NAME
Account name for downloading the workflows, can be used multiple times
--personal Download repositories owned by the authenticated user
Download Public Repositories
usage: raven download crawl [-h] --token TOKEN [--debug] [--redis-host REDIS_HOST] [--redis-port REDIS_PORT] [--clean-redis] [--max-stars MAX_STARS] [--min-stars MIN_STARS]
options:
-h, --help show this help message and exit
--token TOKEN GITHUB_TOKEN to download data from Github API (Needed for effective rate-limiting)
--debug Whether to print debug statements, default: False
--redis-host REDIS_HOST
Redis host, default: localhost
--redis-port REDIS_PORT
Redis port, default: 6379
--clean-redis, -cr Whether to clean cache in the redis, default: False
--max-stars MAX_STARS
Maximum number of stars for a repository
--min-stars MIN_STARS
Minimum number of stars for a repository, default: 1000
Index
usage: raven index [-h] [--redis-host REDIS_HOST] [--redis-port REDIS_PORT] [--clean-redis] [--neo4j-uri NEO4J_URI] [--neo4j-user NEO4J_USER] [--neo4j-pass NEO4J_PASS]
[--clean-neo4j] [--debug]
options:
-h, --help show this help message and exit
--redis-host REDIS_HOST
Redis host, default: localhost
--redis-port REDIS_PORT
Redis port, default: 6379
--clean-redis, -cr Whether to clean cache in the redis, default: False
--neo4j-uri NEO4J_URI
Neo4j URI endpoint, default: neo4j://localhost:7687
--neo4j-user NEO4J_USER
Neo4j username, default: neo4j
--neo4j-pass NEO4J_PASS
Neo4j password, default: 123456789
--clean-neo4j, -cn Whether to clean cache, and index from scratch, default: False
--debug Whether to print debug statements, default: False
Report
usage: raven report [-h] [--redis-host REDIS_HOST] [--redis-port REDIS_PORT] [--clean-redis] [--neo4j-uri NEO4J_URI] [--neo4j-user NEO4J_USER]
[--neo4j-pass NEO4J_PASS] [--clean-neo4j]
[--tag {injection,unauthenticated,fixed,priv-esc,supply-chain,best-practice,endoflife,reconnaissance}]
[--severity {info,low,medium,high,critical}] [--query_ids RQ-1,..,RQ-16] [--queries-path QUERIES_PATH] [--format {raw,json}]
{slack} ...
positional arguments:
{slack}
slack Send report to slack channel
options:
-h, --help show this help message and exit
--redis-host REDIS_HOST
Redis host, default: localhost
--redis-port REDIS_PORT
Redis port, default: 6379
--clean-redis, -cr Whether to clean cache in the redis, default: False
--neo4j-uri NEO4J_URI
Neo4j URI endpoint, default: neo4j://localhost:7687
--neo4j-user NEO4J_USER
Neo4j username, default: neo4j
--neo4j-pass NEO4J_PASS
Neo4j password, default: 123456789
--clean-neo4j, -cn Whether to clean cache, and index from scratch, default: False
--tag {injection,unauthenticated,fixed,priv-esc,supply-chain,best-practice,endoflife,reconnaissance}, -t {injection,unauthenticated,fixed,priv-esc,supply-chain,best-practice,endoflife,reconnaissance}
Filter queries with specific tag
--severity {info,low,medium,high,critical}, -s {info,low,medium,high,critical}
Filter queries by severity level (default: info)
--query_ids RQ-1,..,RQ-16, -id RQ-1,..,RQ-16
Filter queries by query ids (example: RQ-2,RQ-8)
--queries-path QUERIES_PATH, -dp QUERIES_PATH
Queries folder (default: library)
--format {raw,json}, -f {raw,json}
Report format (default: raw)
Examples
Retrieve all workflows and actions associated with any account (user/organization).
raven download account --token $GITHUB_TOKEN --account-name microsoft --account-name google --debug
Scrape all publicly accessible GitHub repositories.
raven download crawl --token $GITHUB_TOKEN --min-stars 100 --max-stars 1000 --debug
After finishing the download process or if interrupted using Ctrl+C, proceed to index all workflows and actions into the Neo4j database.
raven index --debug
Now, we can generate a report using our query library.
raven report --severity high --tag injection --tag unauthenticated
Rate Limiting
For effective rate limiting, you should supply a Github token. For authenticated users, the next rate limiting applies:
- Code search - 30 queries per minute
- Any other API - 5000 per hour
Research Knowledge Base
Current Limitations
- It is possible to run external action by referencing a folder with a
Dockerfile(withoutaction.yml). Currently, this behavior isn't supported. - It is possible to run external action by referencing a docker container through the
docker://...URL. Currently, this behavior isn't supported. - It is possible to run an action by referencing it locally. This creates complex behavior, as it may come from a different repository that was checked out previously. The current behavior is trying to find it in the existing repository.
- We aren't modeling the entire workflow structure. If additional fields are needed, please submit a pull request according to the contribution guidelines.
Future Research Work
- Implementation of taint analysis. Example use case - a user can pass a pull request title (which is controllable parameter) to an action parameter that is named
data. That action parameter may be used in a run command:- run: echo ${{ inputs.data }}, which creates a path for a code execution. - Expand the research for findings of harmful misuse of
GITHUB_ENV. This may utilize the previous taint analysis as well. - Research whether
actions/github-scripthas an interesting threat landscape. If it is, it can be modeled in the graph.
License
Hall of Fame - Vulnerabilities Found and Disclosed Using Raven
Want more of CI/CD Security, AppSec, and ASPM? Check out Cycode
If you liked Raven, you would probably love our Cycode platform that offers even more enhanced capabilities for visibility, prioritization, and remediation of vulnerabilities across the software delivery.
If you are interested in a robust, research-driven Pipeline Security, Application Security, or ASPM solution, don't hesitate to get in touch with us or request a demo using the form https://cycode.com/book-a-demo/.




















